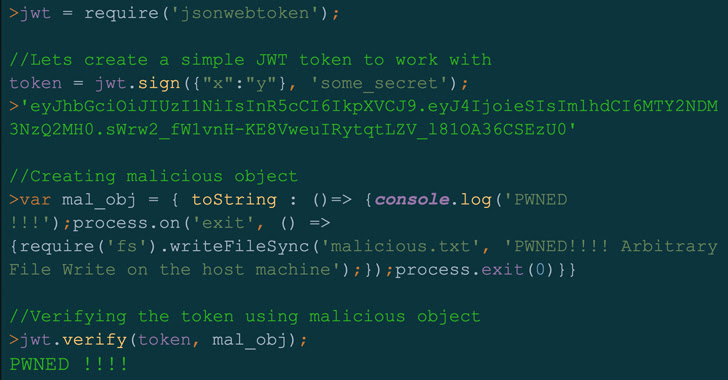
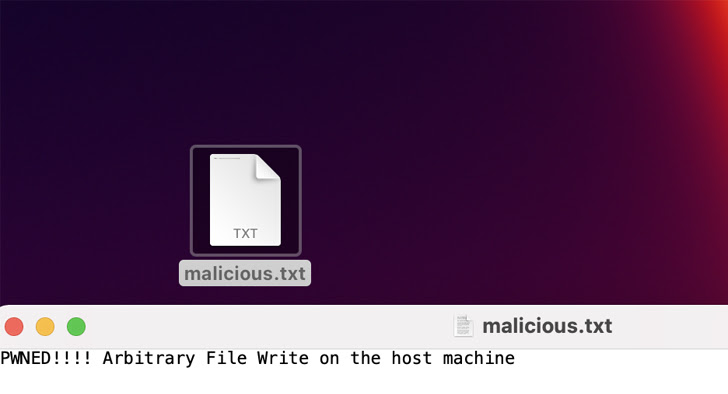
A high-severity safety flaw has been disclosed within the open supply jsonwebtoken (JWT) library that, if efficiently exploited, might result in distant code execution on a goal server.
“By exploiting this vulnerability, attackers might obtain distant code execution (RCE) on a server verifying a maliciously crafted JSON net token (JWT) request,” Palo Alto Networks Unit 42 researcher Artur Oleyarsh mentioned in a Monday report.
Tracked as CVE-2022-23529 (CVSS rating: 7.6), the problem impacts all variations of the library, together with and beneath 8.5.1, and has been addressed in model 9.0.0 shipped on December 21, 2022. The flaw was reported by the cybersecurity firm on July 13, 2022.
jsonwebtoken, which is developed and maintained by Okta’s Auth0, is a JavaScript module that enables customers to decode, confirm, and generate JSON net tokens as a method of securely transmitting data between two events for authorization and authentication. It has over 10 million weekly downloads on the npm software program registry and is utilized by greater than 22,000 tasks.
Subsequently, the flexibility to run malicious code on a server might break confidentiality and integrity ensures, probably enabling a foul actor to overwrite arbitrary information on the host and carry out any motion of their selecting utilizing a poisoned secret key.
“With that being mentioned, with the intention to exploit the vulnerability described on this submit and management the secretOrPublicKey worth, an attacker might want to exploit a flaw throughout the secret administration course of,” Oleyarsh defined.
As open supply software program more and more emerges as a profitable preliminary entry pathway for risk actors to stage provide chain assaults, it is essential that vulnerabilities in such instruments are proactively recognized, mitigated, and patched by downstream customers.
Making issues worse is the truth that cybercriminals have turn out to be a lot quicker at exploiting newly revealed flaws, drastically shrinking the time between a patch launch and exploit availability. In line with Microsoft, it solely takes 14 days on common for an exploit to be detected within the wild after public disclosure of a bug.
To fight this downside of vulnerability discovery, Google, final month, introduced the discharge of OSV-Scanner, an open supply utility that goals to establish all transitive dependencies of a venture and spotlight related shortcomings impacting it.