An evaluation of threats encountered by 4 organizations has recognized the commonest methods utilized by attackers to compromise programs, infiltrate networks, and steal information, in response to information analysts at Splunk SURGe, which printed particulars of the analysis on Dec. 14.
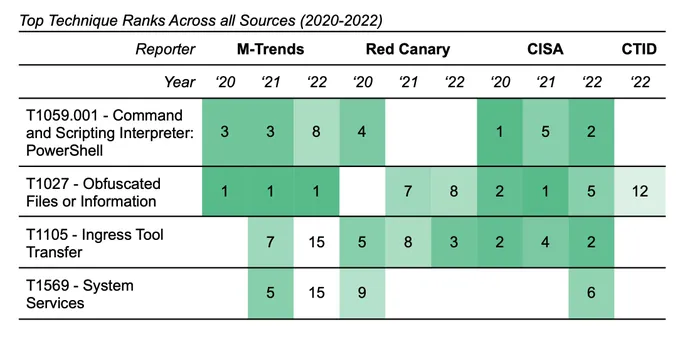
The evaluation used printed information from Mandiant, Purple Canary, MITRE’s Heart for Menace Knowledgeable Protection, and the US Cybersecurity and Infrastructure Safety Company (CISA) to search out the most well-liked post-compromise menace actions, as outlined by the MITRE ATT&CK framework. Menace teams that achieve entry to a compromised system, for instance, are doubtless (28% of the time) to begin up the PowerShell command line utility to increase their assault laterally all through a community and to achieve persistence on the compromised machine, the evaluation discovered.
Using PowerShell, obfuscating information, and exploiting public-facing functions are the three hottest methods for attackers, the evaluation discovered. Utilizing the info, safety operations middle (SOC) managers can make sure that they’re targeted on detecting frequent techniques, says Ryan Kovar, distinguished safety strategist and chief of Splunk’s SURGe analysis workforce.
“Loads of occasions, SOC analysts do not know the place to begin, and these are the areas the place 4 trusted sources are saying they see adversaries constantly utilizing these methods,” he says. “I speak to lots of people all over the world, and they don’t have logging turned on for PowerShell, and for those who don’t have logging for PowerShell you’re by no means going to see what’s arguably the No. 1 adversary method in response to these 4 teams.”
The evaluation effort mixed information on cyberattacks from a number of industries and a number of years, together with greater than 400 methods from the MITRE ATT&CK framework and greater than 100 methods focusing on industrial management programs (ICS).
The evaluation comes at a time when attackers are shifting towards utilizing extra stealthy techniques and hands-on intrusion methods, making the coaching of SOC analysts more and more vital. Prior to now 12 months, for instance, cybersecurity providers agency CrowdStrike has seen a small however measurable enhance in focused assaults, which now account for 18% of all assaults. As well as, attackers are eschewing malware of their assaults, with 71% of intrusions investigated by the agency not utilizing malicious instruments.
For defenders, discovering methods to detect assaults stays troublesome, Splunk researchers said within the evaluation.
“It has by no means been tougher to determine which threats deserve essentially the most consideration,” the evaluation said. “A sound defensive strategy to directing evaluation efforts ought to be data-driven, specializing in the tendencies and development of attacker tradecraft, akin to represented in ATT&CK.”
PowerShell, Obfuscated Information Prime Techniques
The highest 4 techniques utilized by intruders contains utilizing PowerShell as a command shell and script interpreter and trying to obfuscate information and instructions to stay stealthy. Utilizing vulnerabilities in public-facing functions is the third most typical method, whereas spear-phishing assaults are the No. 1 preliminary entry method, in response to Splunk’s evaluation.
The corporate plans to broaden the listing to a high 20 most typical techniques, permitting safety groups to debate whether or not they can detect the methods and the way greatest to make use of their present instruments to take action.
A crucial a part of the hassle ought to be to recreation out every method, the way it may very well be detected, and whether or not the present data, telemetry, and logs are in a position to detect attackers who use the method. Figuring out which logs and telemetry to trace is the onerous half, Kovar says.
“Discover all of the methods to log and present that data as a result of each vendor and firm has such totally different data and totally different platforms,” he says. “That’s the place the onerous work is available in, and for lots of people, they know what they need to do, however they simply do not know the place to begin.”
Easing the Ache for Menace Hunters
By specializing in the assault methods mostly utilized by attackers, SOCs and safety groups ought to have extra details about methods to enhance their applications and higher detect attackers.
Easing the work of SOC evaluation is crucial. A year-old survey discovered that 72% of SOC analysts rated the ache of doing their jobs a minimum of a 7 out of 10.
Ultimately, Splunk’s SURGe workforce goals to offer cybersecurity professionals a option to harden their networks in opposition to assaults. Tackling the highest 20 listing of attacker techniques and guaranteeing that the SOC can detect each method is an effective way to start 2023, Kovar says.
“Your mileage could differ,” he provides, “however I’m very assured that if you wish to begin your menace searching program in a pair areas and need an instantaneous return on funding, that is the place you can begin.”


