As soon as upon a time, encrypted site visitors was thought of the protected, safe possibility for shopping and doing enterprise on-line. Nonetheless, going again to December 2013, the Google Transparency Report exhibits simply 48% of Internet site visitors was encrypted. Flash ahead to right now, and the quantity of encrypted Internet site visitors is as much as 95%. Nonetheless, the risk panorama has modified quite a bit since 2013, and now we discover the vast majority of cyberthreats lurking inside encrypted channels.
Hidden in your encrypted Web site visitors layers are malware payloads, phishing scams, delicate knowledge leaks, and extra. To grasp this higher, the State of Encrypted Assaults 2022 Report analyzed 24 billion threats from October 2021 to September 2022 to disclose particulars on threats embedded in HTTPS site visitors, together with SSL and TLS. The report exhibits a constant upward pattern of assaults utilizing encrypted channels — from 57% in 2020 to 80% in 2021 — finally discovering that greater than 85% of assaults have been encrypted in 2022. There have been different main findings as nicely.
Most Encrypted Threats Contain Malware
Whereas cybercriminals cover a wide range of assault ways in encrypted site visitors, malware stays essentially the most prevalent. Malicious scripts and payloads used all through the assault sequence make up practically 90% of the encrypted assault ways blocked in 2022.
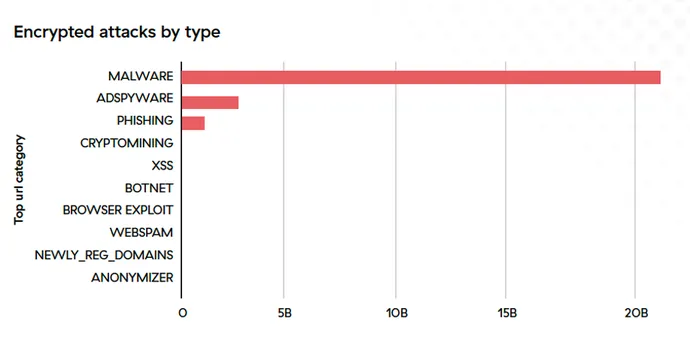
Malware continues to pose the best risk to people and companies throughout 9 key industries, with manufacturing, training, and healthcare the most typical targets. This class contains ransomware, which stays a high concern for CISOs, as ransomware assaults have elevated by 80% 12 months over 12 months.
Essentially the most prevalent malware households the ThreatLabz workforce noticed abusing encrypted channels embody ChromeLoader, Gamaredon, AdLoad, SolarMarker, and Manuscrypt.
US, India Are High Targets for Encrypted Assaults
The 5 nations most focused by encrypted assaults in 2022 have been the US, India, South Africa, the UK, and Australia. As well as, a number of nations noticed important upticks in targets 12 months over 12 months, together with Japan (+613%), the US (+155%), and India (+87%).
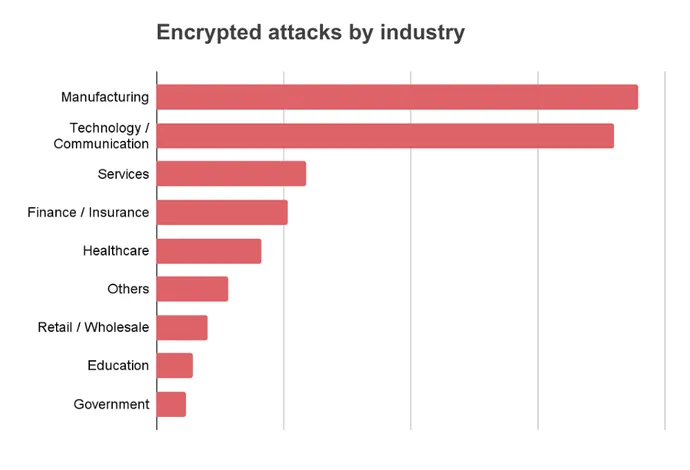
Encrypted Assaults Elevated in Manufacturing, Training
Greater than doubling in encrypted assaults (239%), manufacturing displaced expertise as essentially the most focused business in 2022. Encrypted assaults towards the training business have been additionally up considerably (134%). Attackers significantly favored manufacturing over different sectors as a goal for advert spyware and adware. Additionally it is one in all two industries most frequently phished through encrypted channels — the opposite being healthcare.
Right now, most assaults leverage SSL or TLS encryption, which is resource-intensive to examine at scale and greatest executed with a cloud-native proxy structure. Whereas legacy firewalls help packet filtering and stateful inspection, their useful resource limitations make them poorly fitted to this activity. This creates a important want for organizations to implement cloud-native architectures that help full inspection of encrypted site visitors in alignment with zero-trust rules.
Learn how to Shield Your self
For defenders, the crucial is evident: all encrypted site visitors should be totally inspected to detect and cease cyberthreats earlier than they trigger injury. Whereas we await governments, compliance frameworks, and different distributors to meet up with this actuality, will probably be as much as defenders and leaders to lift the flag and champion initiatives to mitigate this widespread risk tactic. Zero-trust methods and architectures — during which you belief no one and examine and authenticate every little thing — are the best approach to shield your group from encrypted assaults and different superior threats.
Assaults begin with reconnaissance and an preliminary compromise of an endpoint or asset uncovered to the Web. As soon as inside, attackers carry out lateral propagation, together with reconnaissance and establishing a community foothold. Lastly, attackers act to attain their targets, which frequently contain knowledge exfiltration.
Your defenses ought to embody controls for every of these levels. Reduce the assault floor by making inside apps invisible to the Web, and stop compromise through the use of cloud-native proxy structure to examine all site visitors inline and at scale, implementing constant safety insurance policies. Organizations also needs to cease lateral motion by connecting customers on to purposes (quite than the community) to scale back the assault floor, and include threats utilizing deception and workload segmentation. They’ll additionally cease knowledge loss by inspecting all Web-bound site visitors, together with encrypted channels, to stop knowledge theft.
If you’re seeking to reduce the chance of encrypted assaults in your group, think about these suggestions as a part of your adoption technique:
- Use a cloud-native, proxy-based structure to decrypt, detect, and stop threats in all encrypted site visitors at scale.
- Leverage an AI-driven sandbox to quarantine unknown assaults and cease patient-zero malware.
- Examine all site visitors, on a regular basis, whether or not a person is at residence, at headquarters, or on the go, to make sure everyone seems to be constantly protected towards encrypted threats.
- Terminate each connection to permit an inline proxy structure to examine all site visitors, together with encrypted site visitors, in real-time — earlier than it reaches its vacation spot — to stop ransomware, malware, and extra.
- Shield knowledge utilizing granular context-based insurance policies, verifying entry requests and rights primarily based on context.
- Get rid of the assault floor by connecting customers on to the apps and assets they want, by no means to networks.
Learn extra Associate Views from Zscaler.


