The implementation of defense-in-depth architectures and working system hardening applied sciences have altered the menace panorama. Traditionally, zero-click, singular vulnerabilities had been generally found and exploited. The trendy-day defensive posture requires attackers to efficiently chain collectively a number of exploit methods to achieve management of a goal system. The elevated utilization of dynamic evaluation programs has pushed attackers to evade detection by requiring enter or motion from the person. Generally, the sufferer should carry out a number of handbook steps earlier than the underlying payload is activated. In any other case, it stays dormant and undetectable by behavioral evaluation.
It’s well-known that client-side assaults are the predominant entry vector for many preliminary entry. Net browser and email-based malware campaigns goal customers by phishing, social engineering, and exploitation. Productiveness and enterprise instruments from distributors like Adobe and Microsoft are widespread and supply attackers with many choices. Combining the dearth of safety consciousness coaching and well-developed social engineering techniques often ends in customers allowing the execution of malicious embedded logic like weaponized macros or different scripts. Evaluation of those widespread malware carriers is time-consuming and tedious, and it requires skilled abilities. To adequately forestall, detect, and reply to those threats, a corporation should throw all the things on the drawback and increase this beforehand human-intensive course of.
Deep File Inspection (DFI) is one method to ease the burden related to steady safety monitoring. DFI is a static-analysis engine that inspects past Layer 7 of the OSI mannequin, basically automating the work of your typical SOC analyst or safety researcher. Whatever the complexity of evasive methods a menace actor makes use of, DFI dissects malicious carriers to show embedded logic, semantic context, and metadata. Coercive graphical lures
are extracted and processed by a machine imaginative and prescient layer, including to the semantic context of the unique file. Generally used obfuscation strategies and encoding mechanisms are routinely found and deciphered.
A public concern that SOC analysts, IR groups, and safety researchers encounter is the restricted availability of context for detection analytics. Within the case of intrusion prevention programs, sources are restricted to microseconds of time and kilobytes of analyzable knowledge. Intrusion detection programs can sometimes dig deeper, taking extra milliseconds to show additional knowledge.
Relating to the time-analysis trade-off, the subsequent step up is behavioral monitoring or sandboxed execution. This class of options detonates samples in a virtualized surroundings and annotates the system’s habits for menace detection; this course of is each compute- and time-intensive, taking minutes to investigate every file. There’s a center floor the place a couple of extra seconds can present beforehand unseen detection alternatives.
Use Case: Qbot Malware Delivered through Follina and Malspam
An instance of an evasive menace is the latest TA570 campaigns that delivered Qbot malware with thread-hijacked emails. This wave of malspam utilized two totally different strategies to supply the payload. The primary technique used a shortcut LNK to run a DLL with the hidden attribute. The second technique is a Phrase doc utilizing the Follina (CVE-2022-30190) exploit.
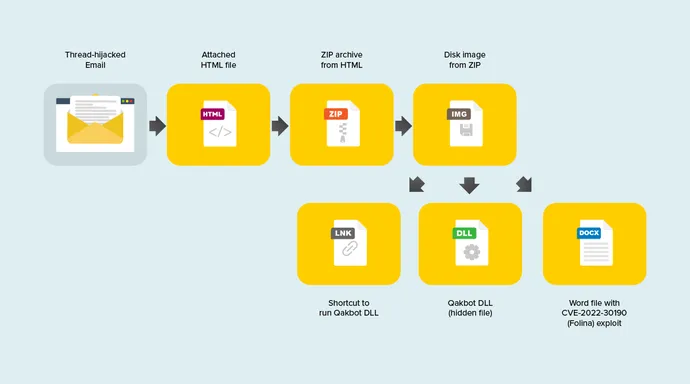
The connected HTML file incorporates an antiquated JS perform to transform the embedded base64 string into a zipper archive and immediate the sufferer to obtain. When extracted, the zip file incorporates a disk picture that can be mounted exhibiting both a shortcut or the shortcut and phrase doc. The shortcut will execute the Qbot DLL throughout the listing with the hidden attribute set. On the identical time, the Phrase file will try to take advantage of the MSDT vulnerability and obtain the payload from a distant server.
It’s difficult for a lot of options to carve the zip archive from the encoded HTML, extract the IMG file, and establish the weaponized contents. On this instance, a number of menace signatures are seen from ambiguities throughout the SMTP headers, right down to the hidden DLL or Follina doc.
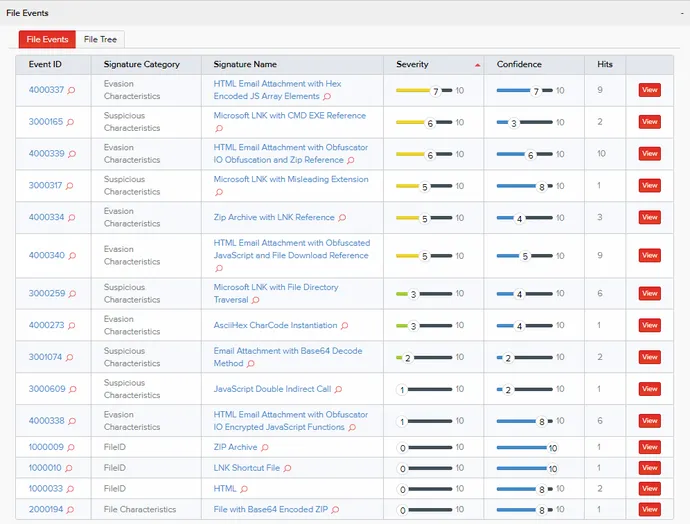
One other attention-grabbing method for detection is the idea of retrospective evaluation or RetroHunting. Whereas DFI creates a brand new dimension of knowledge, RetroHunting gives a brand new dimension of time for analyzing historic occasions. The looks of Follina and different zero-day vulnerabilities illustrates the usefulness of this functionality by facilitating the detection of beforehand unseen alerts with rising menace intelligence and detection logic.
Along with a library of predeveloped signatures, analysts can develop user-defined YARA
guidelines to mix strings, bytes patterns, and common expressions through versatile conditional logic.
When confronted with novel assault methods being encountered within the wild, safety leaders should present a possibility to empower your detection operations and overcome the restrictions inherent with different malware prevention options. A free useful resource to check the efficacy of a mail supplier’s safety controls is the E mail Safety Evaluation.
In regards to the Creator

Josiah Smith has virtually a decade of expertise within the realm of safety. Earlier than changing into a menace engineer, Josiah labored as a cyber operator, overseeing signature administration and host-based detection packages. He spent a number of years in a room with out home windows, specializing in community detection, menace looking, and IR investigations. He started his profession as a member of the US Air Power, and most of his expertise is with the DoD.


