 We all know everyone seems to be busy. Everybody already has an excessive amount of on their plate and is making an attempt to be taught as a lot as they’ll every single day.
We all know everyone seems to be busy. Everybody already has an excessive amount of on their plate and is making an attempt to be taught as a lot as they’ll every single day.
However right here, in a nutshell, is what you possibly can educate your self, your co-workers, your mates, and your loved ones to assist them to higher acknowledge and beat social engineering and phishing. It’s not good. It doesn’t cowl each state of affairs, nevertheless it does cowl an enormous proportion of them. And in the event you be taught and educate it nicely…in the event you make a tradition of wholesome skepticism round these frequent social engineering/phishing traits, nothing else you would be taught or educate will scale back extra danger.
We’ve been educating the identical lesson for the reason that very starting: Cease! Look! Assume!
It’s the guiding message of all content material we ship.
Educate two frequent traits of all social engineering and advocate one response. What may very well be simpler to show and create a tradition round?
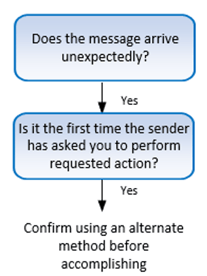
If any message (be it in an e-mail, web site, social media, SMS textual content, or voice name), arrives unexpectedly and the sender, regardless of who it first seems to be, is asking you to carry out a brand new motion for the primary time, understand that it is a increased danger message than all of the others. Most social engineering scams start this manner.
You could or might not acknowledge the sender. It actually doesn’t matter. The sender’s e-mail handle may be faked, or it may possibly even be the sender’s actual account which has been hacked and utilized by a scammer. So, discover that the stream chart doesn’t embody the oft repeated suggestion, “Do you acknowledge the sender?” It’s not a foul trait to care about, nevertheless it simply means much less nowadays as hackers are so often taking on folks’s authentic accounts. Who amongst us hasn’t gotten a phishing message in social media from a trusted good friend’s account that has been taken over?
Most social engineering scams arrive unexpectedly. We weren’t ready for the message or the decision. It simply got here to us. It was in our inbox or by way of an inbound voice name, and all of the sudden somebody was asking us to do one thing, for them, that we’ve by no means executed earlier than. The request might even sound believable. The truth is, most social engineering scams comprise believable requests…to verify on so and so, obtain this doc, present this needed piece of knowledge, and so forth. If social engineering scams didn’t ask for believable actions, nobody would ever fall for the scams. Most are asking for issues that appear regular for the state of affairs they’re claiming.
So, the trait to be careful for is the requestor, whoever they’re, are asking you to do one thing distinctive for them that you just’ve by no means executed for that particular person or group earlier than. It might probably even be one thing you’ve executed earlier than…simply not for that requestor.
Sure, many authentic requests have each traits: arrive unexpectedly and ask you to do one thing new.
However the secret’s to acknowledge that these are additionally quite common indicators of social engineering scams. It might not be that the surprising request is a rip-off. Simply prepare your self that everytime you see these two issues, that you just decelerate and ensure utilizing an alternate trusted technique (e.g., name the particular person on a identified good telephone quantity, go on to the seller’s identified good web site URL as an alternative of clicking on the hyperlink within the e-mail, and so forth.).
There are different frequent traits of social engineering scams, such because the request incorporates a “stressor occasion” the place they’re making an attempt to get you to make a fast resolution…since you’ll lose entry to a trusted account, lose cash, lose a enterprise deal, make somebody mad, and so forth. and any message together with a stressor occasion provides to the suspicion.
However let’s begin with two straightforward circumstances that anybody can be taught to lookout for and the best way to reply. Fast and simple. Not a lot to recollect. However a lot energy in studying to create a tradition and wholesome degree of default skepticism round any message with these two traits. Actually, it’s crucial cybersecurity lesson and protection you possibly can educate. Nothing would cut back extra danger.
Cease! Look! Assume!

%20(1).jpg#keepProtocol)
