ConfluencePot is an easy honeypot for the Atlassian Confluence unauthenticated and distant OGNL injection vulnerability (CVE-2022-26134).
Concerning the vulnerability
You’ll find the official advisory by Atlassian to this vulerability right here. For particulars in regards to the internal workings and exploits within the wild it is best to check with the studies by Rapid7 and Cloudflare. Affected however not but patched methods ought to be deemed compromised till additional investigation.
Concerning the instrument
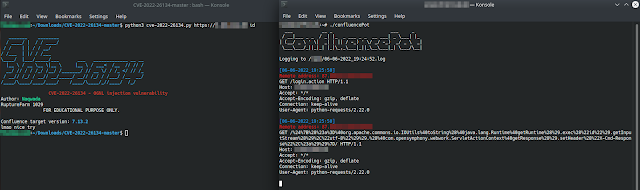
ConfluencePot is written in Golang and implements its personal HTTPS server to attenuate the general assault floor. To make it seem like a legit Confluence occasion it returns a bare-bones model of a Confluence touchdown web page. Log output is written to stdout and a log file on disk. ConfluencePot DOES NOT permit attackers to execute instructions/code in your machine, it solely logs requests and returns a bogus response.
Constructing & Operating it
You want a latest model of Golang to run/construct confluencePot and the suitable privileges to bind to port 443. We suggest to execute it in a tmux session for simpler dealing with. To run ConfluencePot you both have to create a self-signed TLS certificates with openssl or request one from e.g. Let’s Encrypt.
go construct confluencePot.go
./confluencePot
Testing and Points
ConfluencePot was examined utilizing the general public exploit by Nwqda, which appears to be essentially the most used variant within the wild on the time of writing. Should you discover something fallacious with confluencePot please be happy to open a problem or ship us a pull request.
Observe us on Twitter –> @SI_FalconTeam <– to remain updated with our newest analysis. Keep protected!