An ongoing marketing campaign dubbed Earth Bogle is leveraging geopolitical-themed lures to ship the NjRAT distant entry trojan to victims throughout the Center East and North Africa.
“The risk actor makes use of public cloud storage companies corresponding to recordsdata[.]fm and failiem[.]lv to host malware, whereas compromised net servers distribute NjRAT,” Development Micro mentioned in a report printed Wednesday.
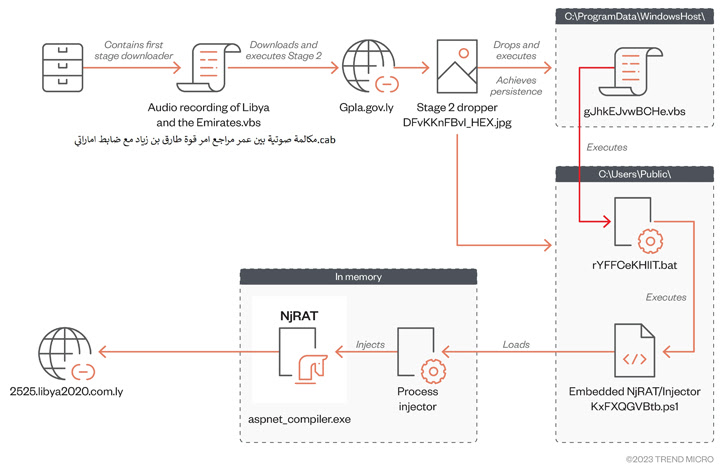
Phishing emails, sometimes tailor-made to the sufferer’s pursuits, are loaded with malicious attachments to activate the an infection routine. This takes the type of a Microsoft Cupboard (CAB) archive file containing a Visible Primary Script dropper to deploy the next-stage payload.
Alternatively, it is suspected that the recordsdata are distributed by way of social media platforms corresponding to Fb and Discord, in some instances even creating bogus accounts to serve advertisements on pages impersonating respectable information shops.
The CAB recordsdata, hosted on cloud storage companies, additionally masquerade as delicate voice calls to entice the sufferer into opening the archive, just for the VBScript to be executed, resulting in the retrieval of one other VBScript file that masks itself as a picture file.
The second-stage VBScript, for its half, fetches from an already breached area a PowerShell script that is chargeable for loading the RAT payload into reminiscence and executing it.
NjRAT (aka Bladabindi), first found in 2013, has myriad capabilities that enable the risk actor to reap delicate info and achieve management over compromised computer systems.
“This case demonstrates that risk actors will leverage public cloud storage as malware file servers, mixed with social engineering methods interesting to folks’s sentiments corresponding to regional geopolitical themes as lures, to contaminate focused populations,” the researchers concluded.