
Goal: To dynamically Assign Wi-fi Person to VLAN based mostly on consumer credentials. This sort of setup is named “Dynamic VLAN Project”
Description: Dynamic VLAN project is one such characteristic that locations a wi-fi consumer into a selected VLAN based mostly on the credentials equipped by the consumer. This process of assigning customers to a selected VLAN is dealt with by a RADIUS authentication server, comparable to Cisco Safe ACS. This can be utilized, for instance, to permit the wi-fi host to stay on the identical VLAN because it strikes inside a campus community.
Associated- Cisco ACS vs ISE Comparability
Due to this fact, when a consumer makes an attempt to affiliate to a LAP registered with a controller, the LAP passes the credentials of the consumer to the RADIUS server for validation. As soon as the authentication is profitable, the RADIUS server passes sure Web Engineering Process Power (IETF) attributes to the consumer. These RADIUS attributes resolve the VLAN ID that must be assigned to the wi-fi consumer. The SSID (WLAN, when it comes to WLC) of the consumer doesn’t matter as a result of the consumer is all the time assigned to this predetermined VLAN ID.
WLC Configuration
This configuration requires these steps:
- Configure the WLC with the Particulars of the Authentication Server
- Configure the Dynamic Interfaces (VLANs)
- Configure the WLANs (SSID)
Configure the WLC with the Particulars of the Authentication Server
It’s essential to configure the WLC so it might talk with the RADIUS server to authenticate the purchasers, and in addition for every other transactions.
Full these steps:
- From the controller GUI, click on Safety.
- Enter the IP handle of the RADIUS server and the Shared Secret key used between the RADIUS server and the WLC.
This Shared Secret key must be the identical because the one configured within the RADIUS server underneath Community Configuration > AAA Shoppers > Add Entry. Right here is an instance window from the WLC:



Configure the Dynamic VLAN (Interfaces)
This process explains the way to configure dynamic interfaces on the WLC. As defined earlier on this doc, the VLAN ID specified underneath the Tunnel-Non-public-Group ID attribute of the RADIUS server should additionally exist within the WLC.
Within the instance, the user1 is specified with the Tunnel-Non-public-Group ID of 10 (VLAN =10) on the RADIUS server.
You may see the identical dynamic interface (VLAN=10) configured within the WLC on this instance. From the controller GUI, underneath the Controller > Interfaces window, the dynamic interface is configured.



- Click on Apply on this window.
This takes you to the Edit window of this dynamic interface (VLAN 10 right here).
Enter the IP Handle and default Gateway of this dynamic interface



Observe: As a result of this doc makes use of an inside DHCP server on the controller, the first DHCP server discipline of this window factors to the Administration Interface of the WLC itself. You may also use an exterior DHCP server, a router, or the RADIUS server itself as a DHCP server to the wi-fi purchasers. In such circumstances, the first DHCP server discipline factors to the IP handle of that machine used because the DHCP server. Check with your DHCP server documentation for extra info.
Now you might be configured with a dynamic interface in your WLC. Equally, you’ll be able to configure a number of dynamic interfaces in your WLC. Nevertheless, keep in mind that the identical VLAN ID should additionally exist within the RADIUS server for that individual VLAN to be assigned to the consumer.
Configure the WLANs (SSID)
This process explains the way to configure the WLANs within the WLC.
Full these steps:
- From the controller GUI, select WLANs > New so as to create a brand new WLAN.
The New WLANs window is displayed.
- Enter the WLAN ID and WLAN SSID info.
You may enter any identify to be the WLAN SSID. This instance makes use of VLAN10 because the WLAN SSID.
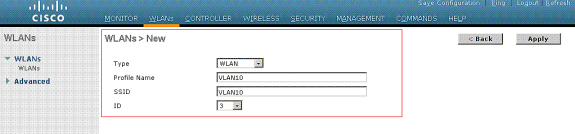


- Click on Apply so as to go to the Edit window of the WLAN SSID10.






Usually, in a wi-fi LAN controller, every WLAN is mapped to a selected VLAN (SSID) so {that a} explicit consumer that belongs to that WLAN is put into the particular VLAN mapped. This mapping is generally carried out underneath the Interface Title discipline of the WLAN SSID window.



Within the instance supplied, it’s the job of the RADIUS server to assign a wi-fi consumer to a selected VLAN upon profitable authentication. The WLANs needn’t be mapped to a selected dynamic interface on the WLC. Or, despite the fact that the WLAN to dynamic interface mapping is completed on the WLC, the RADIUS server overrides this mapping and assigns the consumer that comes by means of that WLAN to the VLAN specified underneath the consumer Tunnel-Group-Non-public-ID discipline within the RADIUS server.
- Test the Enable AAA Override verify field so as to override the WLC configurations by the RADIUS server.
- Allow the Enable AAA Override within the controller for every WLAN (SSID) configured.



When AAA Override is enabled, and a consumer has AAA and controller WLAN authentication parameters that battle, consumer authentication is carried out by the AAA (RADIUS) server. As a part of this authentication, the working system strikes purchasers to a VLAN returned by the AAA server. That is predefined within the controller interface configuration.
As an example, if the company WLAN primarily makes use of a Administration Interface assigned to VLAN 2, and if the AAA Override returns a redirect to VLAN 100, the working system redirects all consumer transmissions to VLAN 100 even when the bodily port to which VLAN 100 is assigned. When AAA Override is disabled, all consumer authentication defaults to the controller authentication parameter settings, and authentication is just carried out by the AAA server if the controller WLAN doesn’t include any client-specific authentication parameters.
Proceed Studying:
CONFIGURE INTERFACES ON WIRELESS CONTROLLER 5508


