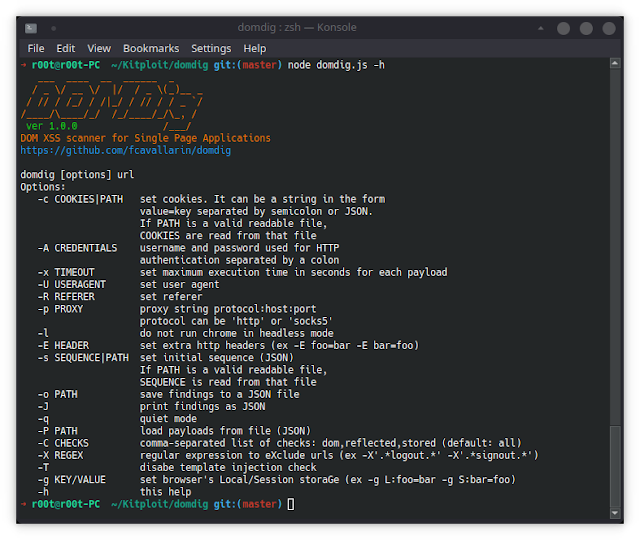
DOMDig is a DOM XSS scanner that runs contained in the Chromium internet browser and it could possibly scan single web page functions (SPA) recursively.
Not like different scanners, DOMDig can crawl any webapplication (together with gmail) by conserving observe of DOM modifications and XHR/fetch/websocket requests and it could possibly simulate an actual consumer interplay by firing occasions. Throughout this course of, XSS payloads are put into enter fields and their execution is tracked with the intention to discover injection factors and the associated URL modifications.
It’s based mostly on htcrawl, a node library highly effective sufficient to simply crawl a gmail account.
KEY FEATURES
- Runs inside an actual browser (Chromium)
- Recursive DOM crawling engine
- Handles XHR, fetch, JSONP and websockets requests
- Helps cookies, proxy, customized headers, http auth and extra
- Scriptable login sequences
GETTING STARTED
Set up
git clone https://github.com/fcavallarin/domdig.git
cd domdig && npm i && cd ..
node domdig/domdig.js
Instance
node domdig.js -c 'foo=bar' -p http:127.0.0.1:8080 https://htcap.org/scanme/domxss.php
Crawl Engine
DOMDig makes use of htcrawl as crawling engine, the identical engine utilized by htcap.
The diagram reveals the recursive crawling proccess.
The video beneath reveals the engine crawling gmail. The crawl lasted for a lot of hours and about 3000 XHR request have been captured.
Login Sequence
A login sequence (or preliminary sequence) is a json object containing a listing of actions to take earlier than the scan begins. Every component of the checklist is an array the place the primary component is the title of the motion to take and the remaining parts are “parameters” to these actions. Actions are:
- write <selector> <textual content>
- click on <selector>
- clickToNavigate <selector>
- sleep <seconds>
Instance
Payloads might be loaded from json file (-P choice) as array of strings. To construct customized payloads, the string window.___xssSink({0}) have to be used because the perform to be executed (as a substitute of the basic alert(1))
Instance
[
';window.___xssSink({0});',
'<img src="http://www.kitploit.com/2022/06/a" onerror="window.___xssSink({0})">'
]