Phishing, the theft of customers’ credentials or delicate information utilizing social engineering, has been a major menace because the early days of the web – and continues to plague organizations immediately, accounting for greater than 30% of all identified breaches. And with the mass migration to distant working throughout the pandemic, hackers have ramped up their efforts to steal login credentials as they reap the benefits of the chaos and lack of in-person person verification.
This has led to the revival of the old-school strategy of vishing, which, like phishing on-line, includes utilizing social engineering over the cellphone to steal delicate info. Vishing assaults have been on the rise in consequence, with 69% of corporations experiencing them in 2021, up from 54% in 2020. These assaults usually take the type of job or tech help scams and might be extremely convincing. In August 2020, the FBI together with the CISA issued a warning concerning distant customers being focused by attackers spoofing organizations’ enterprise numbers and impersonating the IT service desk.
Vishing bypassing 2FA
One of the regarding points of vishing is the attackers’ means to bypass two-factor authentication (2FA) safety measures. 2FA is a well-liked type of multi-factor authentication that requires customers to offer two varieties of info: a password and a one-time code despatched by way of SMS.
Attackers obtain this by impersonating a help consultant and requesting the sufferer’s 2FA code over the cellphone. If the sufferer offers the code, the attacker can acquire full entry to their account, doubtlessly resulting in monetary or private info being compromised.
Attackers impersonating as assist desk help
A typical occasion is when people obtain a pop-up alert claiming that their system has been breached or contaminated with malware and that skilled cellphone help is required to repair the issue. Alternatively, victims might obtain a name from an alleged tech help consultant from a good software program supplier, claiming that malware has been detected on their machine. The attacker will attempt to persuade the person to obtain distant entry software program below the pretext of company IT assist desk representatives. That is the ultimate section of the rip-off, after which it is checkmate for the unsuspecting victims and a possible payday for the attackers.
Attackers impersonating the assistance desk is clearly working: in July 2020, Twitter skilled a significant safety breach when hackers used a vishing rip-off to efficiently entry dozens of high-profile accounts, together with these of Barack Obama, Joe Biden, Jeff Bezos, and Elon Musk. The attackers used these accounts to tweet a bitcoin rip-off, ensuing within the swift theft of over $100,000. In contrast to conventional scams, these assaults goal rigorously chosen people by gathering in depth details about them from social media and different public sources. This info is then used to determine staff who’re most definitely to cooperate and have entry to the specified assets, at which level attackers are primed and able to wreak havoc.
A twist as attackers name the assistance desk & impersonate end-users
Social engineering assaults are rigorously fabricated with collected information and can be utilized to impersonate an end-user on a name to the assistance desk. An skilled attacker can simply purchase solutions to safety questions from numerous sources, particularly understanding end-users put an excessive amount of private info on social media and the online.
Microsoft mentioned that LAPSUS$, a identified menace group, calls on a focused group’s assist desk and makes an attempt to persuade help personnel to reset a privileged account’s credentials. The group would use beforehand gathered info, have an English-speaking caller converse with the assistance desk. They’d be capable of reply frequent restoration prompts equivalent to “first road you lived on” or “mom’s maiden identify” from information collected to persuade assist desk personnel of authenticity.
In one other try to achieve the assistance desk, slack was used. Digital Arts had 780GB of supply code downloaded by hackers presumed to even be LAPSUS$. The menace actors used the authentication cookies to impersonate an already-logged-in worker’s account and entry EA’s Slack channel, then satisfied an IT help worker into granting them entry to the corporate’s inner community.
How can your Assist Desk know who’s actually calling
Verifying person identification within the vishing age is extra vital than ever. With the rise of cyber-attacks and social engineering, it is essential for organizations to have safety measures in place to safeguard their staff, defend their delicate info, and forestall unauthorized entry.
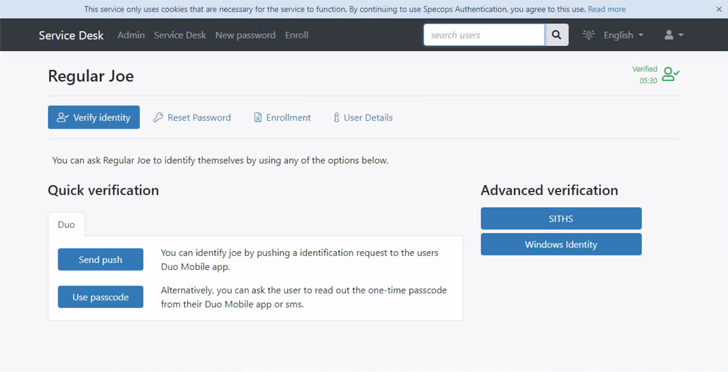
One efficient approach to safeguard towards most of these assaults is to implement a safe service desk answer, which permits for the verification of person accounts with present information past simply knowledge-based authentication. This may be achieved by sending a one-time code to the cell quantity related to the person’s account or utilizing present authentication providers to confirm callers.
Implementing person authentication is one other key facet of Specops Safe Service Desk. This ensures that info and password resets are solely supplied to licensed customers, which is important for shielding high-security accounts and adhering to regulatory necessities. With a Safe Service Desk, you’ll be able to take away the chance for person impersonation by requiring verification with one thing the person has and never simply counting on one thing the person – or an attacker – might know.
Along with verifying and implementing person authentication, a safe service desk additionally permits for the safe reset or unlocking of person accounts. That is accomplished solely after the person has been efficiently verified and might be mixed with a self-service password reset device to help with account unlocks and the password reset course of.
With vishing scams exhibiting no indicators of slowing down, investing in Specops Safe Service Desk answer may very well be a essential step for organizations seeking to defend their folks from even the subtlest of social engineering makes an attempt. By instilling a complete and efficient approach to confirm person identification, implement person authentication, and reset or unlock person accounts, would-be victims can relaxation assured that they will all the time know who’s actually calling.