The time is ripe to consolidate and simplify your safety toolsets.
A July 2022 survey of 300 U.S. Division of Protection (DoD) IT contractors reveals a woeful lack of understanding safety within the majority of conditions. These contractors are a part of the DoD’s provide chain that, in typical authorities communicate, is labeled the Protection Industrial Base (DIB). The report must be a warning even for these know-how contractors that don’t do any DoD work.
A latest assault known as STEEP#MAVERICK focused protection contractors in Europe. One in all them was a provider for one of many US Air Power fighter plane applications. The assault was fairly refined, containing a number of phases and numerous obfuscation and defensive measures to keep away from detection.
This makes the DIB survey extra related. For instance, the survey discovered that:
-
80% lack any vulnerability administration answer
-
79% lack a complete multi-factor authentication (MFA) set of insurance policies and procedures to safe their logins
-
73% lack an endpoint detection and response answer
-
70% haven’t deployed any sort of safety data and occasion administration
Granted, that is a variety of safety infrastructure however at the moment’s enterprise — of any sort, authorities consulting or not — requires these fundamental instruments to be shielded from potential assault. The survey discovered that 82% of the respondents discovered it “reasonably to extraordinarily obscure the governmental laws on cybersecurity.” Whereas the laws are complicated, there’s one aspect of those laws that deserves focus, known as the Cybersecurity Maturity Mannequin Certification (CMMC). We touched on its introduction a number of years in the past and advised that following the CMMC might assist to enhance general cybersecurity posture with US-based firms.
On the coronary heart of the CMMC is a sequence of 110 completely different safety controls which might be a part of a Nationwide Institute of Requirements and Expertise’s doc SP 800-171. This recommends necessities for safeguarding the confidentiality of managed unclassified data from authorities suppliers. The necessities are damaged down into 14 completely different classes, corresponding to entry controls and configuration administration. The doc isn’t new — it additionally has been via one main revision prior to now two years — however it’s complete. The federal government means that “distributors that wish to retain their federal and state company contracts must have a plan that meets the necessities of NIST SP 800-171,” and perceive the assorted controls for his or her IT and operational safety.
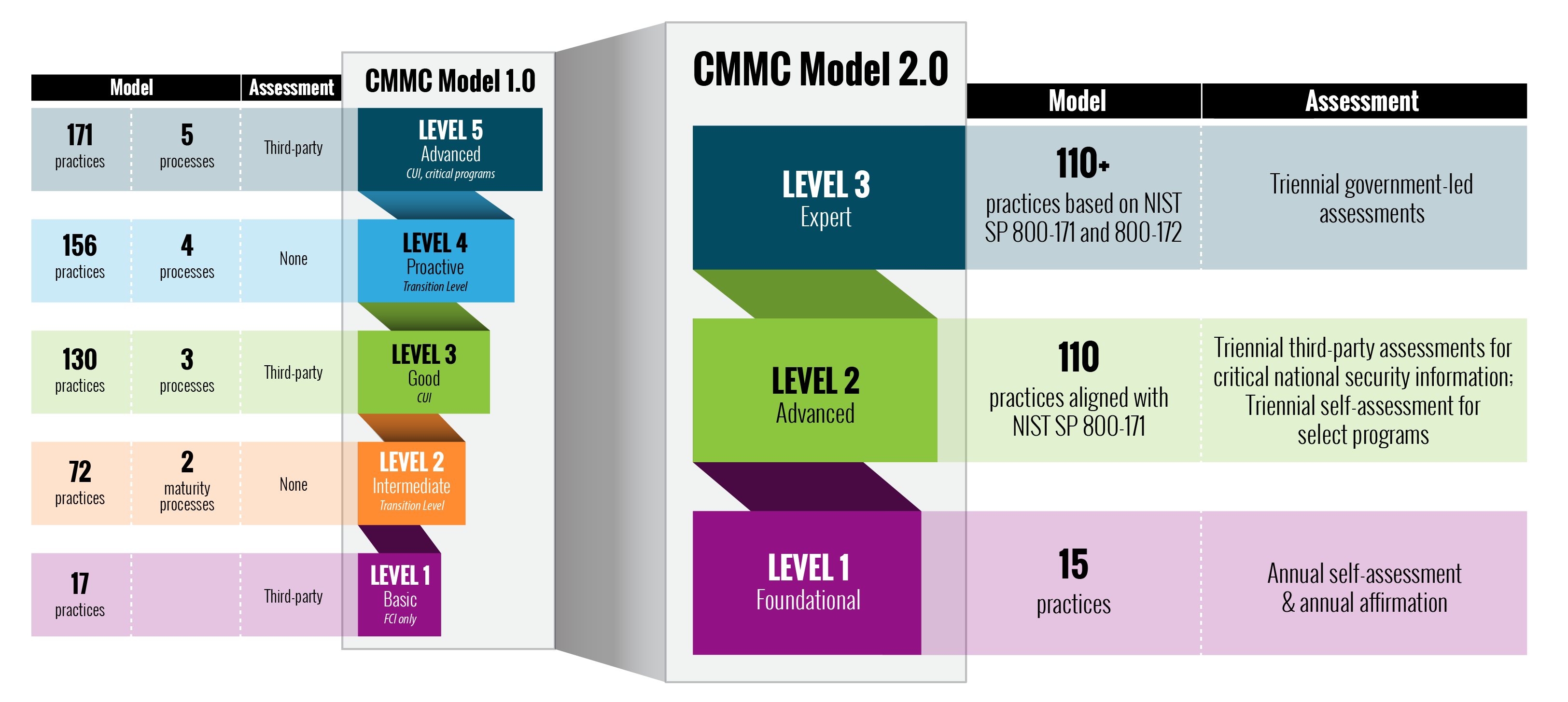
A comparability of the v1 and v2 CMMC rule units. (Picture credit score: U.S. Division of Protection)
The DoD’s hope is that the CMMC compliance will finally catch on, and earlier this yr they introduced that it’s present process a serious revision to v2, which is meant to be in place by March 2023. Within the meantime, the DoD can present all types of useful recommendations on implement higher cybersecurity practices. Definitely, the time is ripe to consolidate and simplify your safety toolsets. And reviewing the CMMC tips can be a good way to seek out your individual safety weak factors.


