DNS or Area Title System abbreviated as DNS is a system used to resolve domains, IP addresses, totally different servers for e.g., FTP servers, recreation servers, energetic directories, and so forth., and preserve their data. Invented by Jon Postel and Paul Mockapetris in 1982, DNS has now turn out to be one of the crucial vital gamers within the modern-day internet world.
DNS truly offers a mapping of the hostname of a community and its deal with. It has proved to ease human life manifold when one seems at its working and the service it provides. It helps customers by translating the domains into IP addresses, permitting them to surf the online with out memorizing such complicated IP codes. Approaching to Wireshark, which is an open-source packet analyzer and has been extensively in use since its inception within the internet world, to research packets acquired or despatched in a community. We will use Wireshark to phase the DNS system and get an in depth have a look at it. The default port for DNS site visitors in Wireshark is 53, and the protocol is UDP (Consumer Datagram Protocol). After we begin Wireshark, we will analyze DNS queries simply. We will be following the beneath steps:
- Within the menu bar, Seize → Interfaces.
- Choose a specific Ethernet adapter and click on begin.
- After this, browse to any internet deal with after which return to Wireshark. Searching would get packets captured and in Wireshark click on the cease within the Seize menu to cease the seize.
- If you happen to haven’t acquired the packet listing by now, you’ll be able to entry it utilizing Edit → Discover Packets. This provides you with the packet listing.
- Since we’re going to analyze DNS we will be finding out solely DNS packets and to get DNS packets, solely you’ll be able to apply DNS within the filters above.
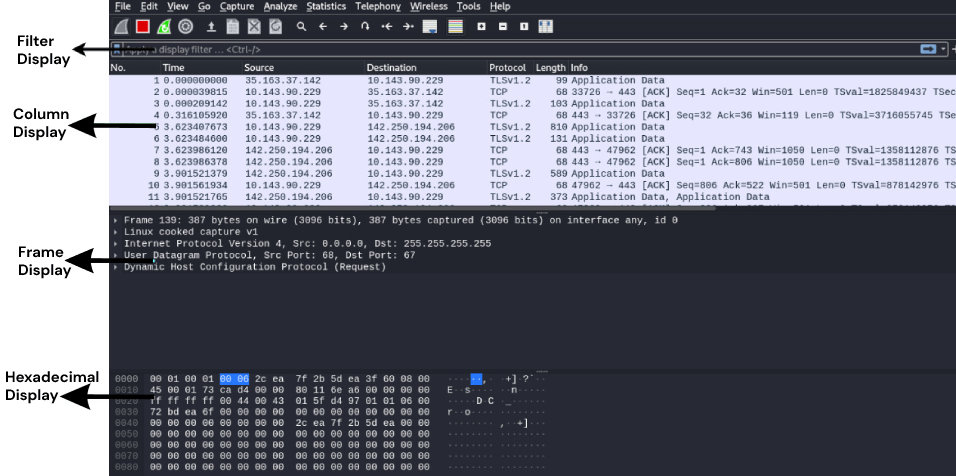
You may have entry to the DNS particulars of any packet by clicking the Area Title System label within the body element part of the Wireshark window. You may take a look at totally different sections of the interface within the picture above.
A fundamental DNS response has:
- Transaction Id-for identification of the communication finished.
- Flags-for verification of response whether or not it’s legitimate or not.
- Questions-default is 1 for any request despatched or acquired. It primarily denotes whether or not you’ve queried for one thing or not.
- Solutions-default is 0 if the response is shipped, and it’s 1 if acquired. If the acquired packet is considered then the Solutions part has the IP deal with of the specified area identify together with Time to Stay which is principally a counter which expires after its allotted time.

Moreover, these, it has a Queries part which provides the subjective particulars of the communication. The queries part has the next:
- Title: Area identify of the vacation spot or internet deal with to be reached or reached by in case of the acquired packet. This part additional has its size, character by character beneath[Name-Length], and the depend of phrases separated by separators, i.e., dot(.) beneath the identify[Labels].
- Sort: which is ‘A‘ for IPv4(32 bits) and is ‘AAAA‘ for IPv6(128 bits).
- Class: which is ‘IN‘ by default, which implies an web IP deal with has been requested for.
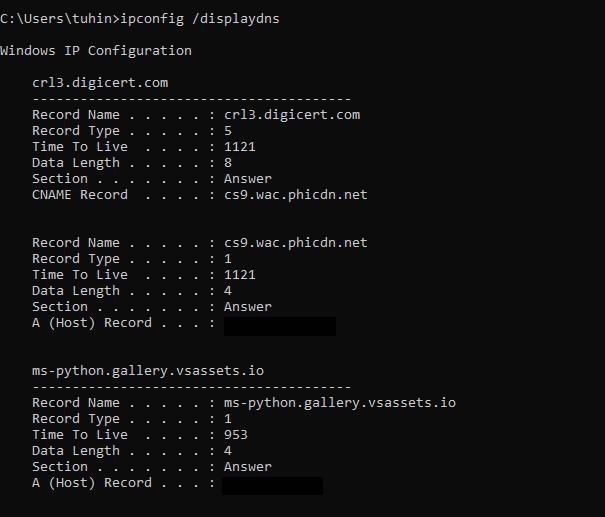
Captured packets are additionally saved within the native machine, We will additionally view our acquired packets in command immediate by typing the next instruction:
ipconfig /displaydns:
You may take a look on the beneath diagram for reference. After you have visited a specific useful resource it will likely be saved and the following time you wish to find a specific useful resource, the host will attempt to discover it within the native storage. So that is how we will analyze DNS queries in Wireshark and get an in depth information of DNS packet functionalities. Checking DNS queries in Wireshark is among the main instruments for finding out community behaviors, and Wireshark is by far the main discussion board for protocol evaluation due to its beginner-friendly and detailed nature.
Wireshark’s packet capturing and extra options of decoding numerous protocol responses have been the most important consider community evaluation in at present’s world. Analyzing DNS will be very helpful because it exhibits the place are the failings current within the community. Particularly in case of irregular DNS conduct, issues come up akin to delay in internet web page loading or larger response time. Bizarre DNS conduct is of main symptom of a hacked system or community. Such circumstances are primarily of the sort referred to as “MIM”(Man-in-the-Center) which causes a delay in packet trade because it will get entry to all of the packets, thus compromising the system. Cyber safety analysts usually search for the DNS question responses first as a way to perceive the community flaw.


