ACM.29: Creating a singular coverage for batch jobs whose roles are created with a typical CloudFormation template.
It is a continuation of my collection on Automating Cybersecurity Metrics.
On this publish we’re going so as to add a coverage for a job created with a typical function template. As defined earlier, we are able to use the identical function CloudFormation template to deploy completely different roles or our batch jobs.
Though we use the identical CloudFormation template for batch job function deployments, we are able to affiliate a singular coverage with every function. If a corporation wished to they might have a crew that deploys the function and every crew creating a selected batch job may create their very own coverage.
As additionally mentioned earlier, a corporation might wish to put boundaries on these capabilities. However the groups constructing the purposes will perceive what it must do higher than anybody else, if they’re constructing a well-architected system. Every crew ought to be capable to create it’s personal zero-trust coverage for a batch job.
I moved the IAM code to a central IAM listing earlier, however I’m going to maintain the IAM coverage related to a batch job within the batch job folder itself. In case you have completely different groups deploying batch jobs you’ll wish to be certain every crew can solely change the insurance policies for its personal batch jobs. You possibly can try this by assigning every crew a separate supply code repository for his or her work in a bigger group.
Create an IAM coverage for a batch job function
We’ve been desirous about making a batch job that may deploy the credentials for our batch job directors. We decided that this function will have to be assumed by our IAM administrator since that’s the consumer that has permissions to take IAM actions in our account. Making a developer entry secret’s an IAM motion.
Since this job would require the IAM administrator to imagine the function to run it, I’m going to create a subdirectory in my jobs folder known as iam and transfer the job there:
/jobs/iam/DeployBatchJobCredentials
After I create jobs which might be executed by a job assumed by our batch job directors I’ll transfer them right into a folder known as “batch”. That may assist me bear in mind what jobs et run by which roles.
I might want to alter my take a look at script that creates the function and ensure it nonetheless works.

I examined and verified that this script nonetheless works.
Now we have to add a coverage to the function to permit it to create the credentials and deploy them to Secrets and techniques Supervisor, encrypted with a KMS key.
Listed here are the permissions we might want to give our function:
- Run CloudFormation Script to create AWS Secret Key and Entry Key for our IAM consumer
- Run CloudFormation Script to create Secrets and techniques Supervisor Secret
- Assign the Encryption Key in our CloudFormation script to the Secret Supervisor Secret and retailer the key
A method to do that can be to provide the batch job function all permissions for KMS, Secrets and techniques Supervisor, and CloudFormation. We will confirm our code capabilities. Then we are able to evaluate the actions the function took and refine our coverage based mostly on that.
The opposite method can be to provide the function no permissions after which take a look at and add permissions based mostly on the errors we get.
I attempted the latter method first however sadly the error messages you get from AWS whenever you get permissions and entry errors should not at all times clear. It is extremely time-consuming to attempt to use that method. That may be my most popular method however because of the roadblocks I hit we’re going to make use of the primary possibility.
For now, to get this working we’re going to add all permissions for the companies we expect we’d like. Then I’ll clarify methods to create a zero-trust function in an upcoming publish.
We’ll wish to use a constant identify for batch job CloudFormation coverage templates so we are able to write a normal deployment mechanism for batch jobs sooner or later. For now we’ll identify this coverage file:
policy_batch_job.yaml
Affiliate the coverage with the batch job function
If we examine the CloudFormation documentation for IAM Coverage, we see that we are able to move in a listing of Roles.

After we scroll right down to see what values we are able to insert for a job, the documentation says we must always use a job identify:

The output for the function ARN we’d like is:
batchjobroleDeployBatchJobCredentials
Should you ran the prior CloudFormation templates you need to see this output on your corresponding CloudFormation stack.

We will use this output with ImportValue to assign the ARN to the Roles factor of our coverage.

For testing functions, we all know that this function will want CloudFormation, SecretsManager, IAM, and KMS. For now we are going to grant full permission to these companies after which evaluate the logs after executing out instructions to see what actions are required.
Be aware that I’d *NEVER USE THIS IN A PRODUCTION ENVIRONMENT*.

I’d most likely need a PermissionBoundary on this in a growth atmosphere for all however those that are liable for implementing IAM Insurance policies.
We’ll have the deployment move within the batch job identify.

We’ll use that parameter within the coverage identify so the coverage identify and batch job identify match.

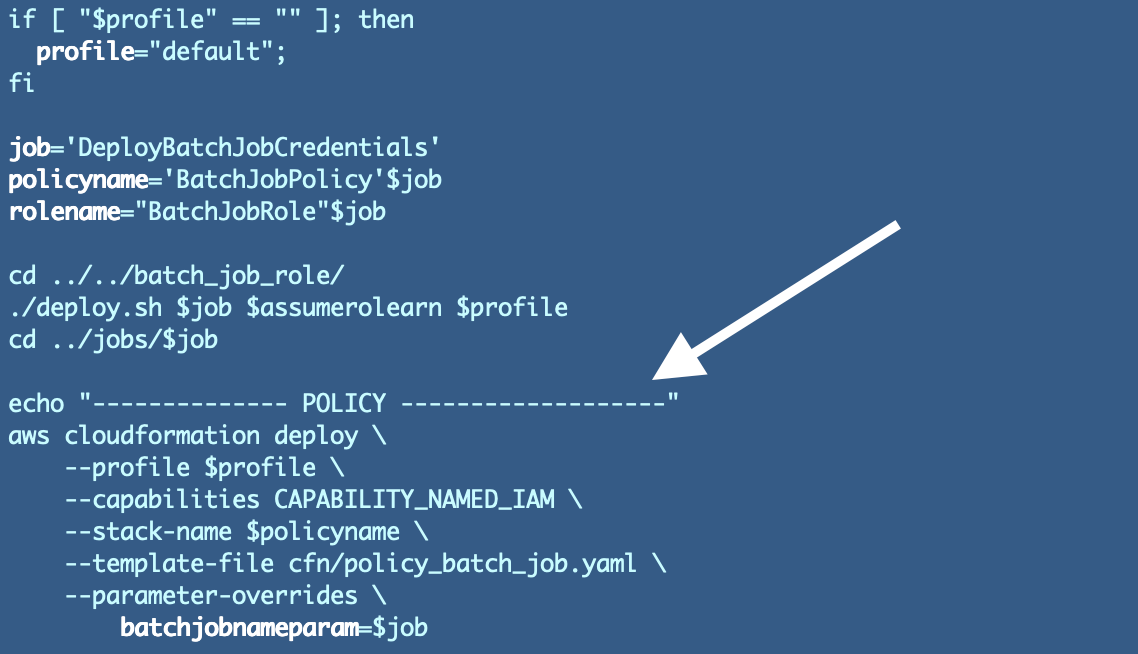
Add the code to our deploy.sh script for our batch job to deploy the useful resource:

Deploy the coverage utilizing the deploy.sh script within the Batch Job listing:
jobs/iam/DeployBatchJobCredentials/deploy.sh
For every new batch job you may create a separate coverage as demonstrated above, however use the prevailing function template. This helps cut back potential errors. It additionally lets you to have a separate crew keep the function template if you could try this than the crew that creates the insurance policies and permissions for every batch job.
Teri Radichel
Should you favored this story please clap and comply with:
Medium: Teri Radichel or E-mail Checklist: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests companies through LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this collection:
____________________________________________
Writer:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration take a look at or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, displays, and podcasts