In keeping with a 2022 Stack Overflow survey of greater than 50K skilled builders, JavaScript is the highest programming language of selection. Discovering cybersecurity dangers in JavaScript code is important for builders working with fashionable internet applied sciences. CodeSec by Distinction may help builders discover and repair dangers of their code, like cross-site scripting (XSS) or damaged entry management vulnerabilities.
CodeSec is Distinction Safety’s free developer safety movement that could be very simple to put in with both Homebrew, npm or straight from binary. You will discover CodeSec at Distinction’s Developer Central on-line portal.
As soon as CodeSec is put in in your machine and you’ve got authenticated with both your GitHub or Google account, you can begin scanning your JavaScript mission for vulnerabilities with the command distinction scan. Scan will look as much as three folders deep in your mission for both a single *.js file to scan or a *.zip file of JavaScript information to scan. At first look, this may appear unusual, however ZIP format is only a extra compact method to add the code information that have to be examined.
On this article, we are going to assume that you’ve got a contemporary JavaScript mission with a number of code information, such because the “browser-test-bench” mission within the beneath screenshots.
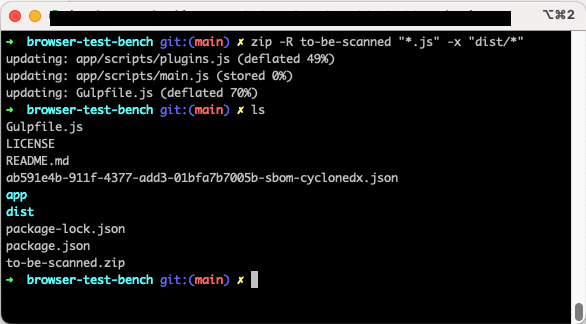
First, let’s zip the mission’s JavaScript information. The zip command-line utility device gives arguments for recursively looking by way of your mission’s folders to seek out JavaScript information whereas additionally excluding sure folders, equivalent to node_modules.
Run Command (from inside your mission folder):
zip -R to-be-scanned “*.js” -x “node_modules”
There are, in fact, loads of variations of this command that you possibly can do to make the ZIP file:
- You might identify it one thing aside from “to-be-scanned.zip,” such because the day’s date or a company-specific format.
- Your mission might not have a node_modules folder stuffed with third-party libraries however might have a lib folder as a substitute.
- Moreover, it’s possible you’ll not wish to do a recursive search by way of the mission’s folders for JavaScript information. As an alternative, you may wish to specify zipping solely sure information as a substitute.
No matter your wants, the ZIP command’s man web page (accessible in your terminal with the command man zip), and looking Stack Overflow are each nice assets for studying in regards to the ZIP device’s choices.
_Creating to-be-scanned.zip of mission JavaScript information
_
As soon as the ZIP file of the mission’s JavaScript information is created, you might be able to run the command to scan for vulnerabilities.
Run Command (from inside your mission folder): distinction scan
Distinction Safety’s Scan product is a Static Evaluation Safety Testing (SAST) cybersecurity device. Which means Scan examines static code information, versus Distinction’s extra dynamic evaluation instruments like Assess (an Interactive Software Safety Testing [IAST] device) and Defend (a Runtime Software Safety device).
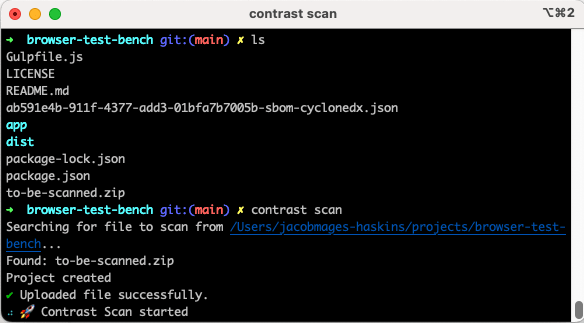
When the scan command begins, it appears for the ZIP file that we made earlier. Subsequent, CodeSec uploads the ZIP file in an effort to analyze its JavaScript code information for vulnerabilities.
_In-progress cybersecurity evaluation for JavaScript information
_
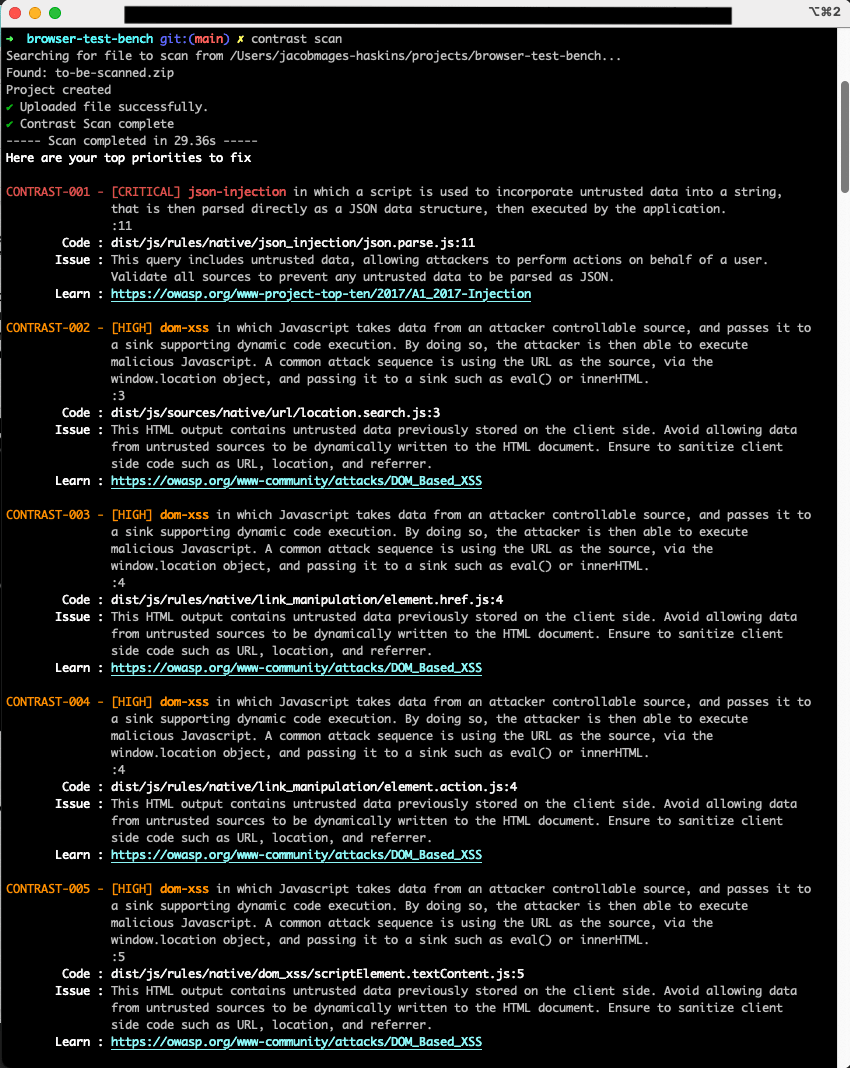
As soon as the Scan evaluation is full, CodeSec lists the vulnerabilities discovered. The vulnerabilities are sorted with probably the most critical-to-fix ones on the prime after which descending in severity. Every vulnerability is described, has the file and line variety of its prevalence listed, and gives assets for studying extra about that cybersecurity threat. The entire info within the Scan evaluation outcomes may help you discover and repair cybersecurity vulnerabilities earlier than they grow to be production-level incidents that your mission’s assist crew must triage.
CodeSec’s Scan evaluation outcomes
Professional tip #1: Many fashionable front-end JavaScript tasks minify their code for deployment in manufacturing. Minified JavaScript just isn’t human-readable and, usually, all on a single line, which implies that the file and line quantity itemizing for a vulnerability within the evaluation outcomes received’t be very helpful for you. As an alternative, strive working distinction scan towards your preminified code.
Professional tip #2: As a result of CodeSec is a command-line device, you may incorporate Scan into your automated software program processes, like we confirmed in our earlier article on utilizing CodeSec with Git hooks.
Conclusion
CodeSec’s free vulnerability scanning assist may help you discover cybersecurity dangers in your JavaScript mission. CodeSec is a free manner for builders to offer high-value software program for this widespread internet know-how selection.