ACM.100 Utilizing an EIP to acquire a set IP tackle for EC2 cases and community interfaces
It is a continuation of my sequence of posts on Automating Cybersecurity Metrics.
In a previous put up I needed to change my IP tackle to an IP tackle that was already allowed by means of my native firewall so I might connect with it.
On this put up I’m going to interchange that present IP tackle with an Elastic IP Deal with (EIP). By utilizing an EIP I’ll have a set IP tackle that continues to be constant when my EC2 occasion (VM) on AWS is stopped and began. I can even level that IP tackle at completely different VMs.
I’m going to deploy the EIP with a CloudFormation template. Then I’m going to affiliate that new IP tackle to the Developer EC2 occasion we deployed.
Your organization might have an AWS Direct Join or a VPNs to create non-public connections to AWS. In some smaller corporations, or if you’re a single person connecting to your personal cloud account, you may use the straightforward choices I’ll current under to enhance safety to your cloud sources. You may additionally want a static IP in some instances comparable to for a penetration check or another connection to a third-party with community restrictions, as I clarify under.
Default AWS EC2 Occasion IP Deal with
Once you deploy EC2 cases on AWS with a public IP tackle you don’t management the IP tackle assigned to your occasion by default. AWS controls that. You’ll get an tackle assigned from one of many many IP addresses within the AWS tackle house. As I wrote about earlier than you’ll find these right here:
https://ip-ranges.amazonaws.com/ip-ranges.json
One of many issues with these random assignments of IP addresses is that it makes it very troublesome to assemble firewall guidelines. You don’t know which IP tackle it is advisable to enable, due to this fact chances are you’ll find yourself merely permitting the entire AWS IP ranges. Then what occurs?
Effectively in some instances attackers leverage AWS and different cloud suppliers to hold out their assaults as a result of they know that’s what you’ve carried out. One instance was the Photo voltaic Winds breach. I defined how attackers used Azure and AWS on this put up:
Firewall guidelines typically want an IP tackle or CIDR block. That is determined by whether or not the firewall is stateless or stateful — phrases I clarify in my e-book on the backside of this put up and in prior posts on this weblog. Stateless firewalls examine particular person packets which don’t have full software layer information like absolutely certified domains (FQDNS). A stateful firewall will put the packets again collectively to carry out inspection and implement guidelines. There are the reason why every are useful in your general community structure.
Even when you should utilize a site identify in your community guidelines, additionally, you will nonetheless have issues with DNS in the case of firewall guidelines and EC2 cases. Your area identify is configured to ship somebody to a selected IP tackle. Then you definitely resolve it is advisable to cease and begin your EC2 occasion. Now it has a brand new IP tackle. Your DNS information not resolve to the right host.
Another person occurs to start out an EC2 occasion and get your outdated tackle. Now your web site guests are getting another machine. If that machine occurs to server up an internet site your area could be pointing to another web site!
I used to be extraordinarily involved about this challenge when deploying a bastion host at Capital One. Builders have been supposed to make use of a site identify to get to it to login — doubtlessly with manufacturing credentials. The individual working the DNS servers couldn’t perceive why a 1 hour TTL was too lengthy.
Elastic IP Deal with
As a substitute of relying on domains, we will use an elastic IP tackle (EIP) on AWS to present an EC2 occasion or load balancer or another useful resource a set IP tackle. You configure a set IP tackle from AWS after which you may assign it to numerous sources. You can even disassociate an IP tackle and assign it to a brand new IP tackle later.
It’s very versatile however you’re restricted to five per area for an IPv4 tackle.
Moreover bear in mind that you’ll not be charged for an EIP in use however when you shouldn’t have it assigned to any useful resource you can be billed for it. Click on on Elastic IP Addresses on this web page to see the pricing.
An alternative choice is to deliver your personal IP to AWS. This matter is extra difficult than we’re going to get into on this sequence however you may examine it right here.
It additionally seems that you just might be able to request contiguous mounted IP addresses.
Why does that matter? Let’s say you will have 5 IP addresses. If the addresses are steady you should utilize a single entry with a CIDR block to permit entry to your IP vary. In any other case you want a single rule in your community guidelines for every tackle. Now let’s say that you’re utilizing Energetic Listing must open 50 separate ports and protocols (that’s what it felt like once I was making an attempt to implement it anyway). 50 x 5 = 250 guidelines.
Let’s say you’re in a fancy networking atmosphere that has acquired many corporations and has quite a few forests and bushes for AD and none of them are contiguous. I’ve having flashbacks. You get the thought. That drawback is a part of the explanation now you can add extra guidelines for safety teams on AWS than was once potential. It was one other certainly one of our function requests whereas I used to be at Capital One.
Fortunately, AWS has provide you with a brand new function that may assist with that challenge known as Prefix Lists. I’ll write extra about these in a couple of posts. You possibly can add a listing of IPs to a prefix checklist and use that in Safety Teams and Firewalls. It gained’t work for AWS NACLs, nevertheless.
Makes use of for elastic IP addresses to enhance safety
Generally clients need me to offer a set IP tackle for a penetration check. I don’t choose this strategy as a result of it’s too straightforward to overlook one thing when solely utilizing a set IP that by some means will get blocked or processed in another way than new IP Addresses, but when it’s a requirement I can use a an EIP.
I began writing about my residence community and the way I’m configuring and testing firewall merchandise. Sorry I’m nonetheless not carried out with this I simply have too many pursuits however hope to get again to it quickly. I would like the code within the sequence I’m writing for enterprise initiatives so it comes first. Anyway, you may configure your own home firewall to solely enable SSH entry to particular hosts when you assign an EIP. There are different methods, some higher than others. I don’t like utilizing DNS providers that aren’t really vetted, for instance. A VPN could be one other good possibility.
As well as, you may specify that solely sure IP addresses are allowed entry in sure cloud providers like GitHub. For those who use an EC2 occasion to obtain and entry code in a non-public GitHub account you may lock it all the way down to solely the IP addresses you wish to authorize. I’ll present you that in a minute. I choose to solely use cloud providers that permit me management entry by way of IP addresses in that means.
Creating an EIP in CloudFormation
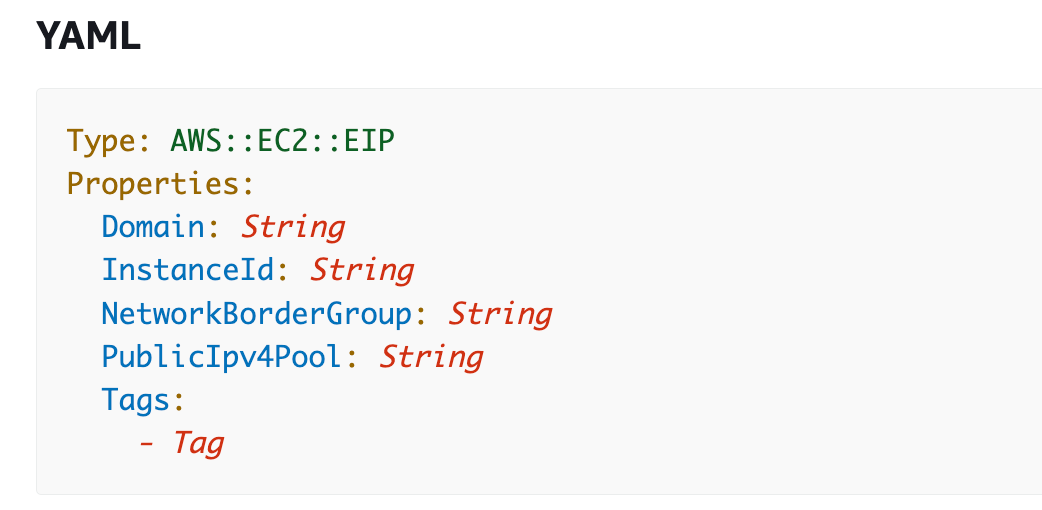
Listed here are the properties out there to us when creating an EIP in CloudFormation.
The one properties that I’m actually involved about are the next:
Tags — Tag: I wish to use a tag to establish the IP tackle with a reputation.
InstanceId: we will affiliate the EIP with an EC2 occasion.
The InstanceId isn’t required, so we will create the EIP and related it at a later time utilizing the EIP Affiliation CloudFormation useful resource. This selection is likely to be crucial if an EC2 occasion has a number of interfaces otherwise you wish to affiliate the IP with a community interface moderately than an EC2 occasion.
Separation of Duties for EIPs to stop community misconfigurations
The EIP ought to in all probability be created beneath networking. Our community directors will management the creation of IP addresses. We’d additionally need them to regulate which sources may be assigned which IP addresses.
Let’s say that you’ve got a rogue person who needs to entry a manufacturing useful resource however she or he can not. If that individual can affiliate a useful resource they aren’t purported to entry on account of networking guidelines with an EIP they’re allowed to entry by means of the firewall they may have the ability to entry one thing they need to not.
Discuss with my prior weblog put up for an instance the place I couldn’t get by means of my firewall to AWS, so I disassociated an IP tackle from an present occasion and assigned it to the occasion to which I needed to attach. 
EIP CloudFormation Dependency issues
Alright so community directors will create and assign EIPs so we’ve some new dependency issues. We’d like the networking earlier than we will create the EC2 occasion however the EC2 occasion earlier than we create the EIP. We’ll wish to create a separate deploy script for the EIP so we will accurately order all of the issues in our check and delete script.
Easy EIP Template
Let’s begin with a easy EIP template and see if it really works. I put this in EIP.yaml in my Networking CloudFormation (cfn) listing.
Subsequent I must replace the deploy script — however discover that we have to move in two parameters. How am I going to get the occasion ID? Recall that we had an output once we created our developer EC2 occasion:
We will reference that in our deploy script. I’ll create a brand new deploy script known as deploy_eip.sh for the explanations talked about above. I’m going to wish to alter the occasion ID to reference that export, so I’ll move within the export identify, and use the export with an ImportValue operate to get the Occasion ID in my template:
Subsequent I added a operate to network_functions.sh
By the best way, I initially used the $identify for my variable and obtained bizarre outcomes. So want to maneuver this out of bash however that is is the quickest option to get the preliminary POC carried out. Keep tuned for a greater possibility (hopefully I’ll have time).
Now I can name the operate from my deploy_eips.sh script.
And check it out…that labored. And our output for the EIP stack has the brand new IP tackle in case we want it. Notice that that is NOT my IP within the screenshot under anymore so don’t be calling it up like 867–5309. For those who’re outdated what I’m speaking about.
You can even check out the checklist of EIPs on the EC2 dashboard and examine your EC2 occasion to confirm that the the IP tackle was assigned accurately.
You will note that public IP tackle in your EC2 occasion as properly. Discover that although my occasion is stopped it nonetheless has the general public IP assigned:
Now which will or will not be sufficient to mean you can connect with that host on AWS. It is determined by your native community. Within the subsequent put up, I’ll present you the way to configure native community firewall guidelines.
Comply with for updates.
Teri Radichel
For those who preferred this story please clap and comply with:
Medium: Teri Radichel or E-mail Record: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests providers by way of LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this sequence:
____________________________________________
Writer:
Cybersecurity for Executives within the Age of Cloud on Amazon
Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, displays, and podcasts