The 5 extensions all exhibit the identical malicious habits. As soon as put in, these extensions start logging each website visited by the consumer and sending that data to servers managed by a risk actor. The command-and-control (C2) servers verify every web site towards an inventory of on-line marketplaces for which the risk actor has registered an affiliate ID. If the consumer visits a website on this checklist, the browser extensions inject code into the web site, modifying the browser cookies to incorporate the risk actor’s affiliate code for that website. Within the occasion the consumer makes a purchase order on this e-commerce website, the risk actor receives an affiliate fee for the acquisition.
The extensions masks their malicious habits by performing their marketed capabilities as customers anticipate them to do. This helps clarify why the extensions have so many downloads. A number of the extensions additionally wait fifteen days earlier than starting to report browser exercise to the C2 servers to additional evade suspicion. Google has eliminated these extensions from the Chrome Net Retailer, however customers who already put in the extensions will nonetheless need to delete them from their browsers.
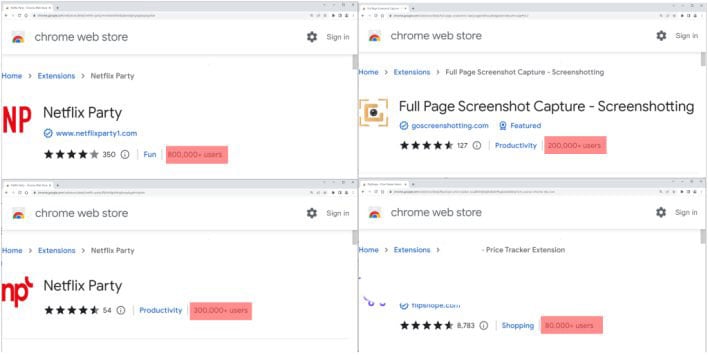
The 5 malicious extensions are as follows:
| Title |
Extension ID | Downloads |
| Netflix Celebration |
mmnbenehknklpbendgmgngeaignppnbe | 800,000 |
| Netflix Celebration 2 |
flijfnhifgdcbhglkneplegafminjnhn |
300,000 |
| FlipShope – Value Tracker Extension |
adikhbfjdbjkhelbdnffogkobkekkkej |
80,000 |
| Full Web page Screenshot Seize – Screenshotting |
pojgkmkfincpdkdgjepkmdekcahmckjp |
200,000 |
| AutoBuy Flash Gross sales |
gbnahglfafmhaehbdmjedfhdmimjcbed | 20,000 |


