ACM.71 Determine and explicitly configure all networking in your AWS Account
It is a continuation of my sequence of posts on Automating Cybersecurity Metrics.
Whenever you create an AWS VPC as we did with our earlier automated VPC creation, you’re going to get an related safety group by default.
Sadly, you can’t delete that safety group. We may attempt to modify it and make it one among our different safety teams however it simply creates sophisticated code. I depart the default safety group in place and rename it to establish it and we will affiliate our no entry rule coverage to that group.
You would additionally write IAM insurance policies to disallow folks from utilizing it, however when you’ve got totally automated deployments then that shouldn’t be an issue. Additionally, the group gained’t permit connections anyplace so it’s not an enormous drawback if somebody does use it after our adjustments.
Add a Identify to the Default Safety Group
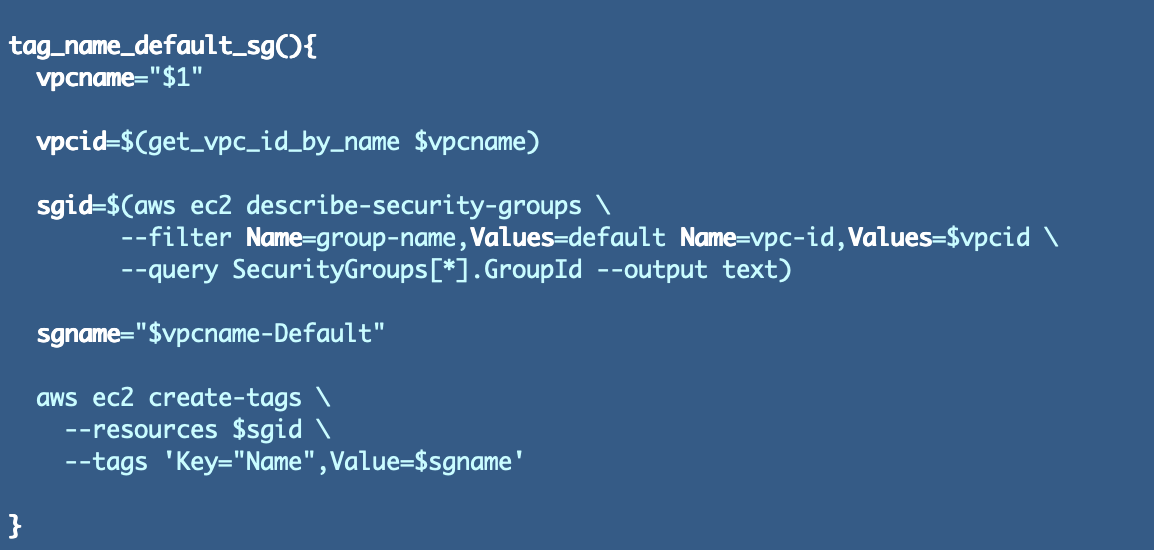
We wish to add a reputation to our default safety group. The place’s one of the best place to try this? I believe it might be best to do from the VPC creation operate as a result of we have already got a deal with on the VPC identify so as to add to the Safety Group and that may assist when including our ruleset as effectively. Nonetheless, as a result of this could possibly be a bit lengthy and it’s actually a separate motion I’ll break it into it’s personal operate.
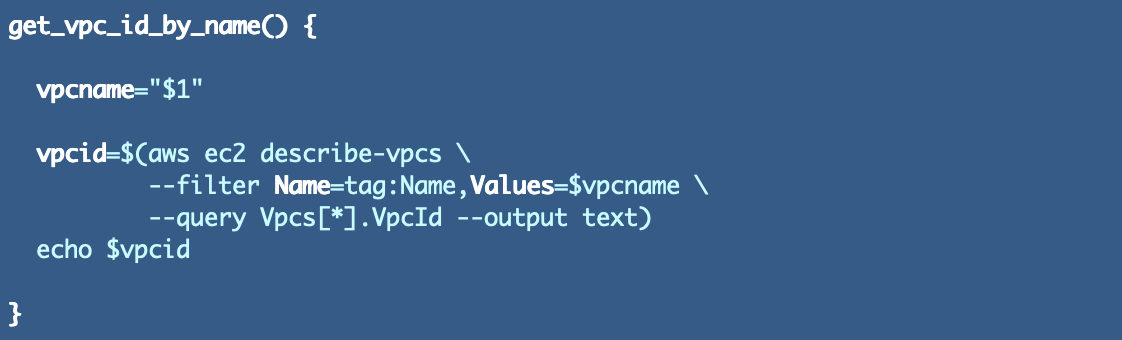
I additionally created a separate operate to get VPC id primarily based on a reputation which is useful:
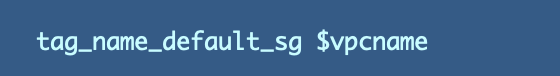
Then it’s straightforward to name the brand new operate from inside our VPC creation operate:
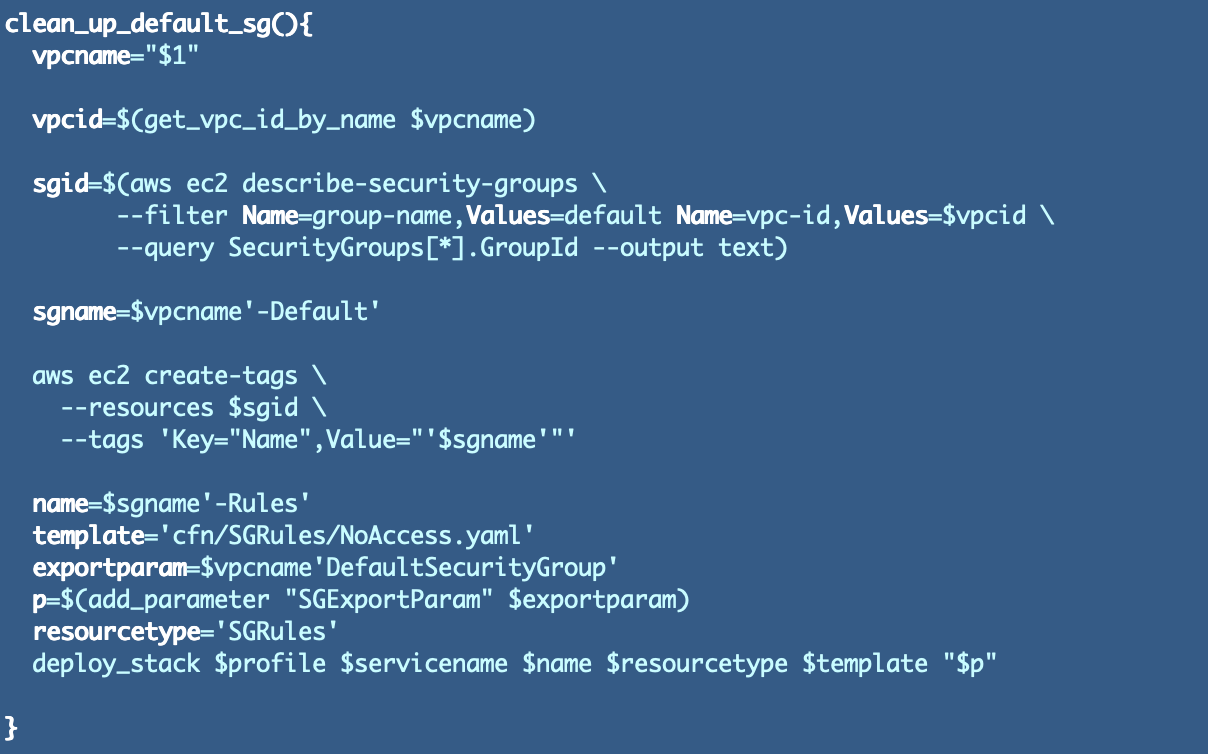
We’re including a Identify tag to the default safety group which incorporates the VPC identify so it’s simply identifiable within the AWS Console.
Add the No Entry Ruleset to the Default Safety Group
Now we will use our NoAccess template so as to add the foundations to the safety group. However wait. That template requires an output from our Safety Group template as a parameter and we didn’t deploy this safety group. What can we do?
In the event you recall our VPC template has quite a few outputs utilizing the obtainable GetAtt values obtainable to us — one among which is the default safety group ID.
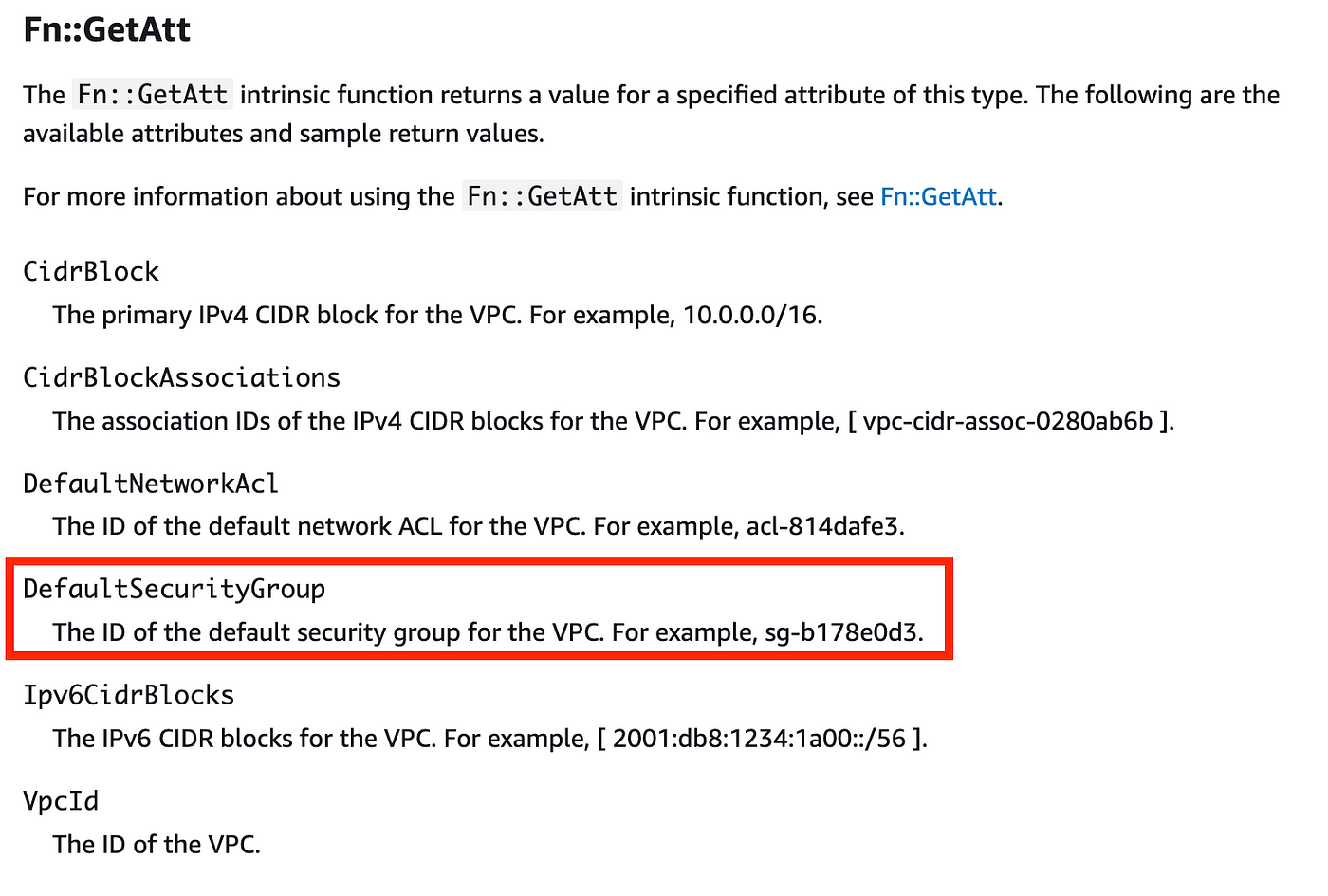
Be aware that I want we additionally had the route desk id right here as that may permit us to extra simply delete the default route desk.
Examine our outputs to get the proper identify so we will use that in our code.
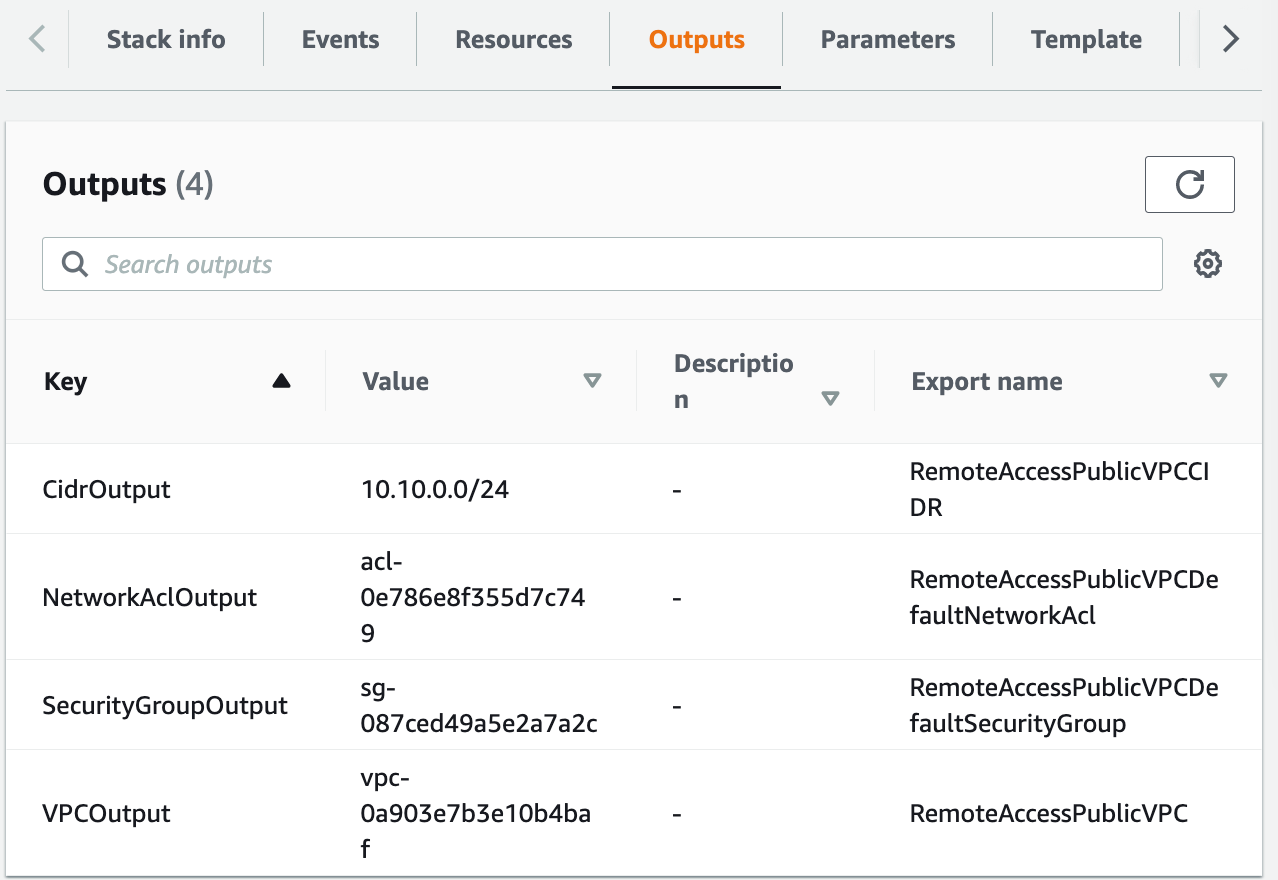
We’re going to make use of the Export identify of the SecurityGroupOutput above which we will calculate utilizing the VPC identify.
As a result of I added this extra performance I ended up renaming it to:
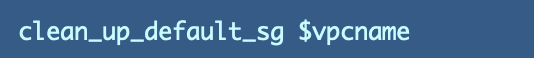
I added the code so as to add the safety group:
What I observed subsequent (after getting the prevailing template working as defined within the final put up) was test the foundations on the default safety teams. Though a brand new safety group with no inbound guidelines will find yourself with no inbound guidelines, the prevailing default safety teams have a rule that by default permits something with that safety group utilized to it hook up with the rest with the identical safety group utilized to it. That features IPv4 or IPv6 site visitors.
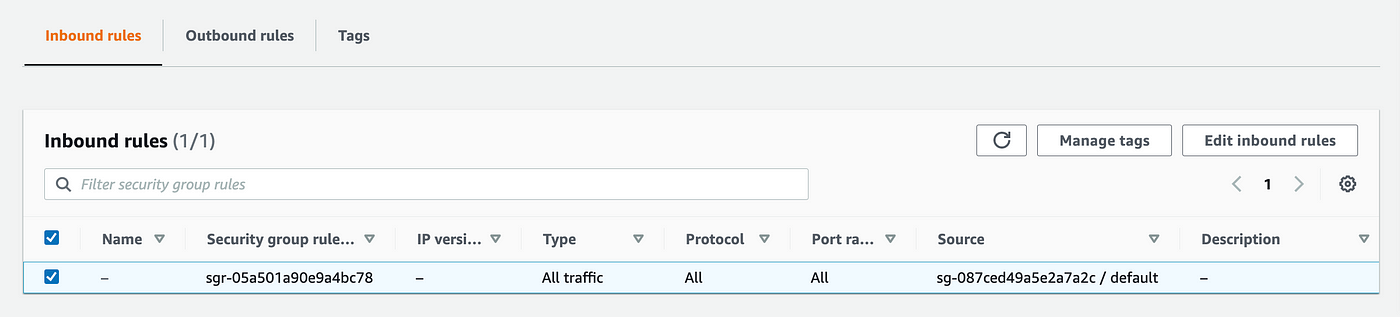
We might want to override that rule, and it gained’t damage to create a restrictive rule for our different new safety teams as effectively. Copy and paste the egress rule and switch it into an ingress rule.
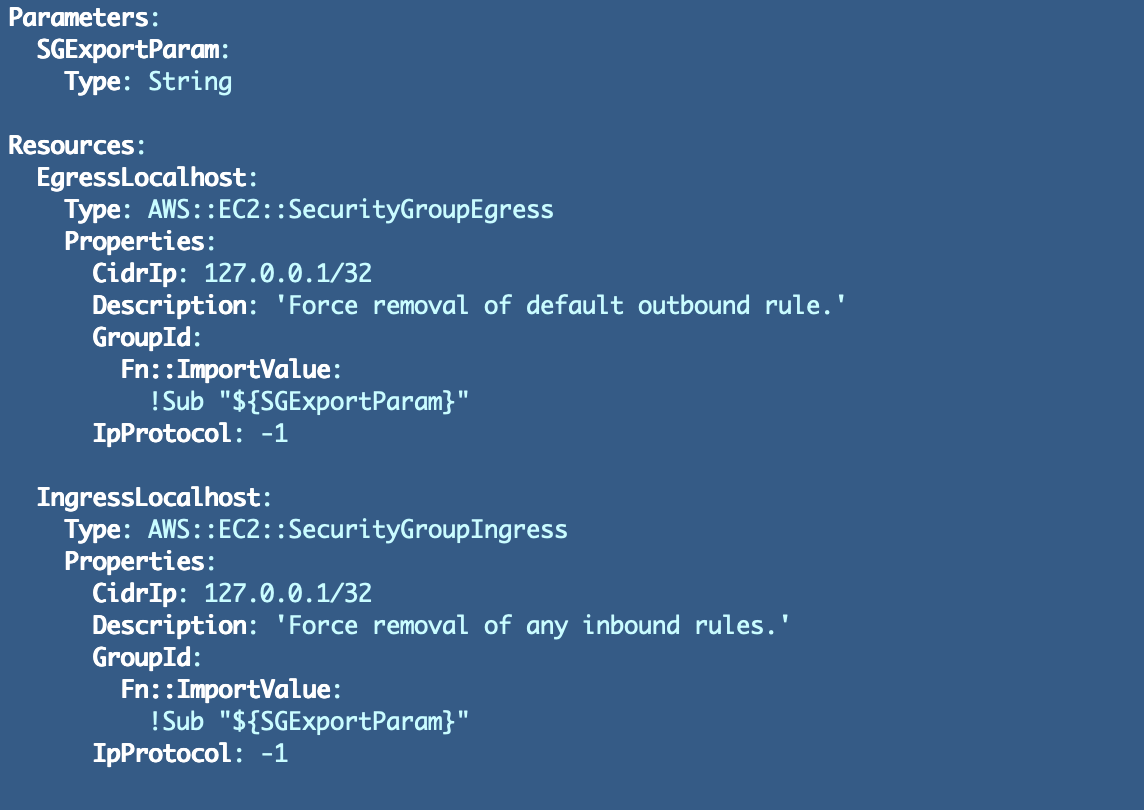
Now we now have default safety teams with names and guidelines we management in our automated VPCs.
AWS Management Tower and non-automated VPCs
In the event you use AWS Management Tower it creates a VPC in your account with a no-name default safety group. We will nearly use this for any current VPCs as effectively, however what in regards to the export names?
You would write code to work round that and rename the Management Tower default safety teams however it might be higher to vary the Management Tower code and redeploy it with the names you need. Sadly that may be a bit difficult the way in which the code is written. You possibly can manually rename the teams however that’s time consuming and people names would possibly get overwritten later if Management Tower must make a change. Sadly I don’t have a great reply for you on that time.
You might also wish to delete the default VPC until you actually need it and solely have the VPCs you explicitly created and handle by means of code in your AWS accounts:
I actually want I didn’t should spend time scripting this weblog put up. It could be higher if AWS allowed you to outline the default safety group as you would like as an alternative of forcing you to do all this work after the actual fact. I suppose Amazon requires the default safety group for some motive in any other case why would it not get created in any respect? I don’t know.
However now we will transfer onto the subject I needed to jot down about which prompted me to create all this networking at this level: VPC Endpoints.
Keep tuned for extra about these and the way they will help you on the subject of community safety. Observe for updates.
Teri Radichel
In the event you favored this story please clap and observe:
Medium: Teri Radichel or E-mail Checklist: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests providers through LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this sequence:
____________________________________________
Writer:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, displays, and podcasts


