Authorities and navy organizations within the Asia-Pacific area are being focused by a beforehand unknown superior persistent menace (APT) actor, per the newest analysis.
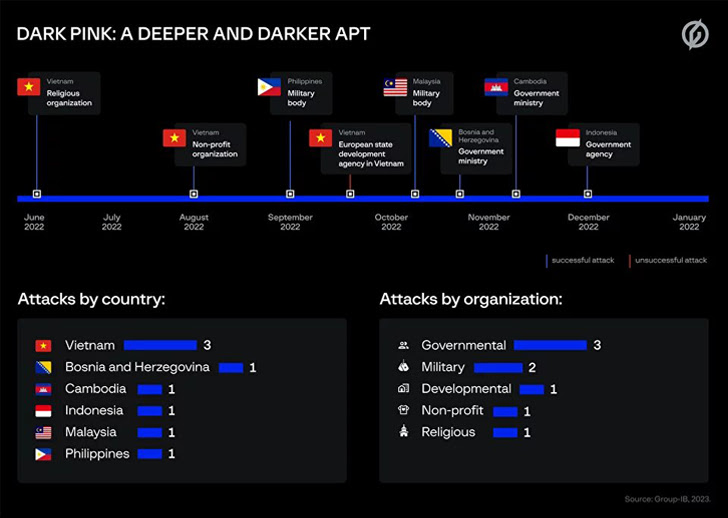
Singapore-headquartered Group-IB, in a report shared with The Hacker Information, stated it is monitoring the continuing marketing campaign beneath the title Darkish Pink and attributed seven profitable assaults to the adversarial collective between June and December 2022.
The majority of the assaults have singled out navy our bodies, authorities ministries and businesses, and spiritual and non-profit organizations in Cambodia, Indonesia, Malaysia, Philippines, Vietnam, and Bosnia and Herzegovina, with one unsuccessful intrusion reported towards an unnamed European state growth physique based mostly in Vietnam.
The menace actor is estimated to have commenced its operations method again in mid-2021, though the assaults ramped up solely a yr later utilizing a never-before-seen customized toolkit designed to plunder useful info from compromised networks.
“Darkish Pink APT’s main targets are to conduct company espionage, steal paperwork, seize the sound from the microphones of contaminated gadgets, and exfiltrate knowledge from messengers,” Group-IB researcher Andrey Polovinkin stated, describing the exercise as a “extremely advanced APT marketing campaign launched by seasoned menace actors.”
Group-IB informed The Hacker Information that there’s not sufficient knowledge to explicitly attribute the menace actor to a selected nation, however famous that it is seemingly of Asia-Pacific origin given the geolocation of recognized victims.
Along with its refined malware arsenal, the group has been noticed leveraging spear-phishing emails to provoke its assaults in addition to Telegram API for command-and-control (C2) communications.
Additionally notable is the usage of a single GitHub account for internet hosting malicious modules and which has been lively since Might 2021, suggesting that Darkish Pink has been in a position to function with out getting detected for over 1.5 years.
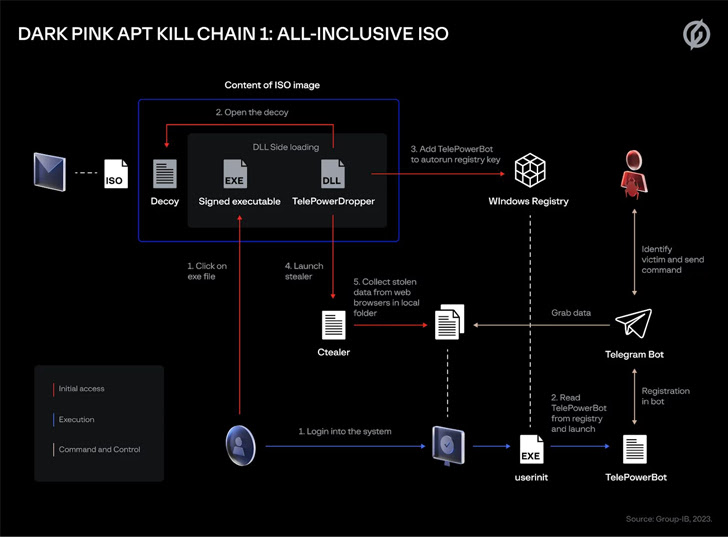
The Darkish Pink marketing campaign additional stands out for using a number of an infection chains, whereby the phishing messages comprise a hyperlink to a booby-trapped ISO picture file to activate the malware deployment course of. In a single occasion, the adversary posed as a candidate making use of for a PR internship.
It is also suspected that the hacking crew could also be trawling job boards with a view to tailor their messages and improve the probability of success of their social engineering assaults.
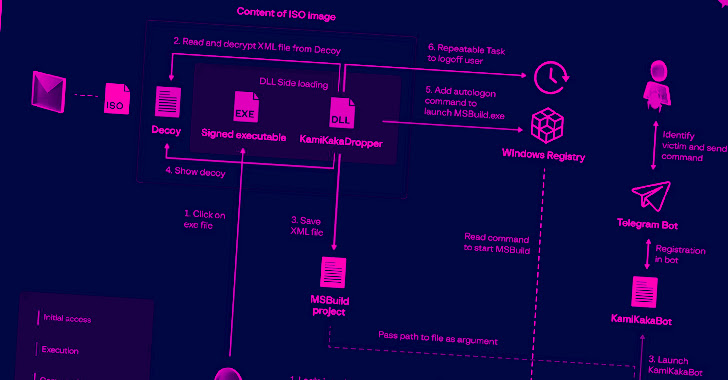
The last word aim is to deploy TelePowerBot and KamiKakaBot, that are able to executing instructions despatched through an actor-controlled Telegram bot, along with utilizing bespoke instruments like Ctealer and Cucky to siphon credentials and cookies from internet browsers.
Whereas Ctealer is written in C/C++, Cucky is a .NET program. One other customized malware is ZMsg, a .NET-based software that enables Darkish Pink to reap messages despatched through messaging apps similar to Telegram, Viver, and Zalo.
An alternate kill chain recognized by Group-IB makes use of a decoy doc included within the ISO file to retrieve a rogue macro-enabled template from GitHub, which, in flip, harbors TelePowerBot, a PowerShell script malware.
That is not all. A 3rd methodology noticed not too long ago in December 2022 sees the launch of KamiKakaBot, a .NET model of TelePowerBot, with the assistance of an XML file containing an MSBuild challenge that is positioned on the finish of a Phrase doc in encrypted view. The Phrase file is current in an ISO picture despatched to the sufferer in a spear-phishing e-mail.
“The menace actors behind this wave of assaults had been in a position to craft their instruments in a number of programming languages, giving them flexibility as they tried to breach protection infrastructure and acquire persistence on victims’ networks,” Polovinkin defined.
A profitable compromise is adopted by reconnaissance, lateral motion, and knowledge exfiltration actions, with the actor additionally utilizing Dropbox and e-mail in some circumstances to transmit information of curiosity. The malware, in addition to recording microphone audio through the Home windows Steps Recorder software, is tasked with taking screenshots and infecting connected USB disks to propagate TelePowerBot.
“Using an nearly fully customized toolkit, superior evasion strategies, the menace actors’ skill to remodel their malware to make sure most effectiveness, and the profile of the focused organizations show the menace that this explicit group poses,” Polovinkin stated.