The Black Basta ransomware-as-a-service (RaaS) syndicate has amassed almost 50 victims within the U.S., Canada, the U.Okay., Australia, and New Zealand inside two months of its emergence within the wild, making it a outstanding risk in a brief window.
“Black Basta has been noticed concentrating on a spread of industries, together with manufacturing, building, transportation, telcos, prescription drugs, cosmetics, plumbing and heating, vehicle sellers, undergarments producers, and extra,” Cybereason mentioned in a report.
Much like different ransomware operations, Black Basta is understood to make use of the tried-and-tested tactic of double extortion to plunder delicate data from the targets and threaten to publish the stolen knowledge until a digital fee is made.
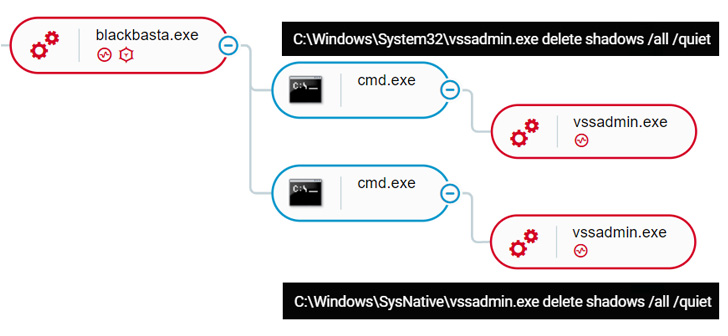
A brand new entrant within the already crowded ransomware panorama, intrusions involving the risk have leveraged QBot (aka Qakbot) as a conduit to take care of persistence on the compromised hosts and harvest credentials, earlier than shifting laterally throughout the community and deploying the file-encrypting malware.
Moreover, the actors behind Black Basta have developed a Linux variant designed to strike VMware ESXi digital machines (VMs) operating on enterprise servers, placing it on par with different teams reminiscent of LockBit, Hive, and Cheerscrypt.
The findings come because the cybercriminal syndicate added Elbit Methods of America, a producer of protection, aerospace, and safety options, to the record of its victims over the weekend, in accordance to safety researcher Ido Cohen.
Black Basta is claimed to be comprised of members belonging to the Conti group after the latter shuttered its operations in response to elevated legislation enforcement scrutiny and a significant leak that noticed its instruments and techniques coming into the general public area after siding with Russia within the nation’s warfare in opposition to Ukraine.
“I can not shoot something, however I can combat with a keyboard and mouse,” the Ukrainian pc specialist behind the leak, who goes by the pseudonym Danylo and launched the treasure trove of knowledge as a type of digital retribution, advised CNN in March 2022.
The Conti crew has since refuted that it is related to Black Basta. Final week, it decommissioned the final of its remaining public-facing infrastructure, together with two Tor servers used to leak knowledge and negotiate with victims, marking an official finish to the legal enterprise.
Within the interim, the group continued to take care of the facade of an energetic operation by concentrating on the Costa Rican authorities, whereas some members transitioned to different ransomware outfits and the model underwent a organizational revamp that has seen it devolve into smaller subgroups with totally different motivations and enterprise fashions starting from knowledge theft to working as unbiased associates.
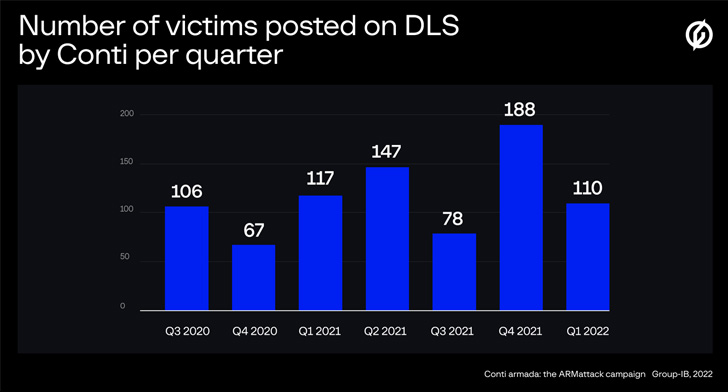
In line with a complete report from Group-IB detailing its actions, the Conti group is believed to have victimized greater than 850 entities because it was first noticed in February 2020, compromising over 40 organizations worldwide as a part of a “lightning-fast” hacking spree that lasted from November 17 to December 20, 2021.
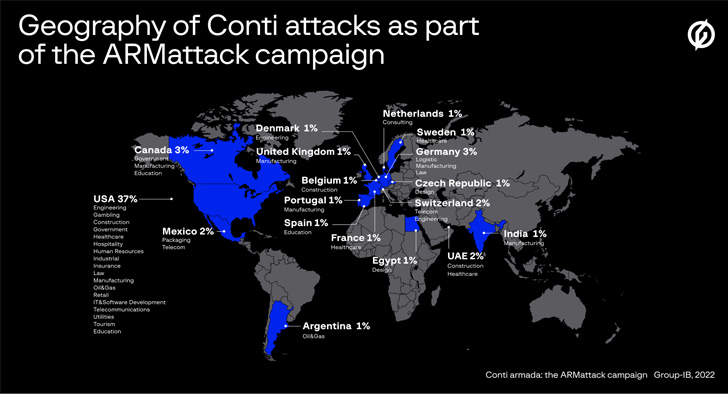
Dubbed “ARMattack” by the Singapore-headquartered firm, the intrusions had been primarily directed in opposition to U.S. organizations (37%), adopted by Germany (3%), Switzerland (2%), the U.A.E. (2%), the Netherlands, Spain, France, the Czech Republic, Sweden, Denmark, and India (1% every).
The highest 5 sectors traditionally focused by Conti have been manufacturing (14%), actual property (11.1%), logistics (8.2%), skilled providers (7.1%), and commerce (5.5%), with the operators particularly singling out corporations within the U.S. (58.4%), Canada (7%), the U.Okay. (6.6%), Germany (5.8%), France (3.9%), and Italy (3.1%).
“Conti’s elevated exercise and the information leak recommend that ransomware is now not a recreation between common malware builders, however a bootleg RaaS trade that offers jobs to tons of of cybercriminals worldwide with varied specializations,” Group-IB’s Ivan Pisarev mentioned.
“On this trade, Conti is a infamous participant that has in actual fact created an ‘IT firm’ whose aim is to extort massive sums. It’s clear […] that the group will proceed its operations, both by itself or with the assistance of its ‘subsidiary’ tasks.”