Cybersecurity researchers have printed the inside workings of a brand new wiper referred to as Azov Ransomware that is intentionally designed to deprave information and “inflict impeccable harm” to compromised techniques.
Distributed by means of one other malware loader referred to as SmokeLoader, the malware has been described as an “efficient, quick, and sadly unrecoverable information wiper,” by Israeli cybersecurity firm Examine Level. Its origins have but to be decided.
The wiper routine is ready to overwrite a file’s contents in alternating 666-byte chunks with random noise, a way known as intermittent encryption that is being more and more leveraged by ransomware operators to evade detection and encrypt victims’ information sooner.
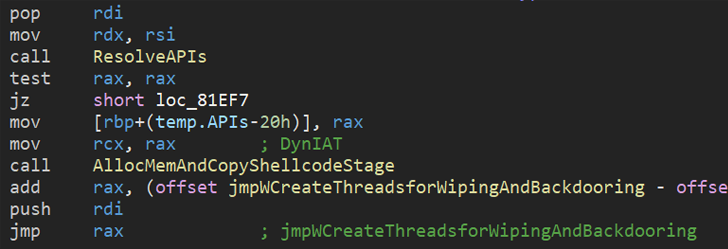
“One factor that units Azov aside out of your garden-variety ransomware is its modification of sure 64-bit executables to execute its personal code,” risk researcher Jiří Vinopal stated. “The modification of executables is completed utilizing polymorphic code, in order to not be doubtlessly foiled by static signatures.”
Azov Ransomware additionally incorporates a logic bomb – a set of circumstances that ought to be met earlier than activating a malicious motion – to detonate the execution of the wiping and backdooring capabilities at a predetermined time.
“Though the Azov pattern was thought-about skidsware when first encountered […], when probed additional one finds very superior methods — manually crafted meeting, injecting payloads into executables with a purpose to backdoor them, and a number of other anti-analysis tips normally reserved for safety textbooks or high-profile brand-name cybercrime instruments,” Vinopal added.
The event comes amid a profusion of harmful wiper assaults for the reason that begin of the yr. This contains WhisperGate, HermeticWiper, AcidRain, IsaacWiper, CaddyWiper, Industroyer2, DoubleZero, RURansom, and CryWiper.
Final week, safety agency ESET disclosed one other beforehand unseen wiper referred to as Fantasy that is unfold utilizing a provide chain assault concentrating on an Israeli software program firm to focus on prospects within the diamond trade. The malware has been linked to a risk actor referred to as Agrius.