Cybercriminals and different menace actors are more and more utilizing knowledge dumped from ransomware assaults in secondary enterprise electronic mail compromise assaults, in line with new evaluation by Accenture Cyber Risk Intelligence. https://www.accenture.com/us-e…
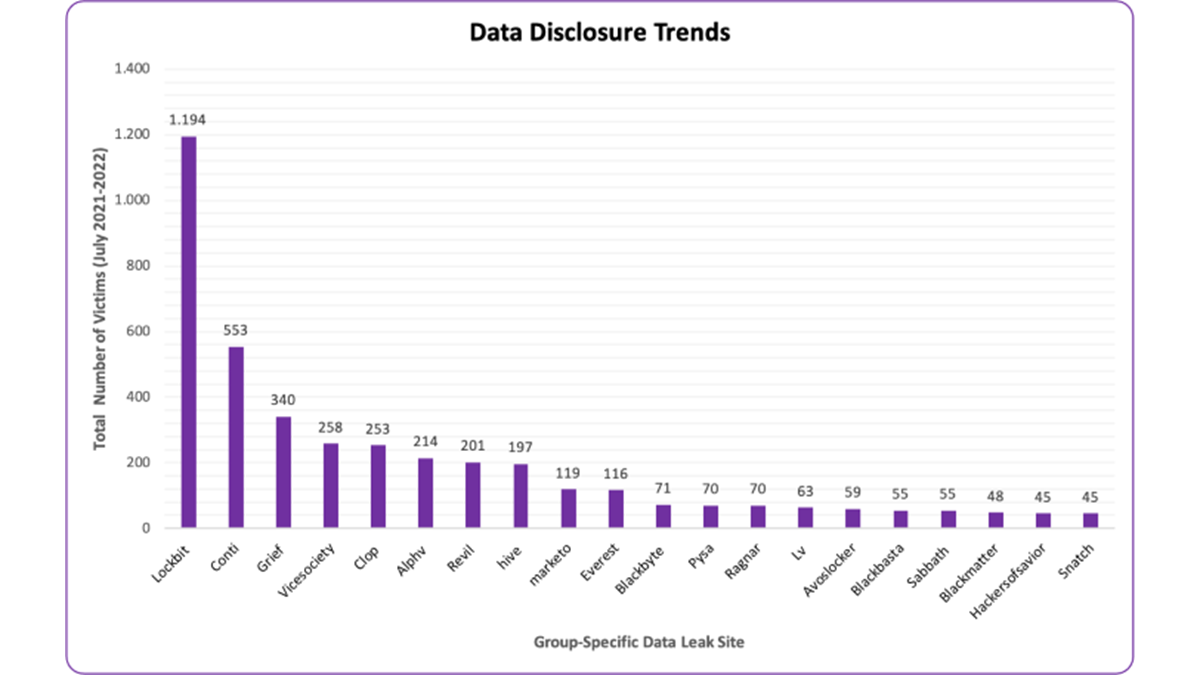
The ACTI workforce analyzed knowledge from 20 most lively ransomware leak websites, measured by variety of featured victims, between July 2021 and July 2022. Of the 4,026 victims (company, non-governmental organizations and governmental entities) uncovered on numerous ransomware teams’ devoted leak websites, an estimated 91% incurred subsequent knowledge disclosures, ACTI discovered.
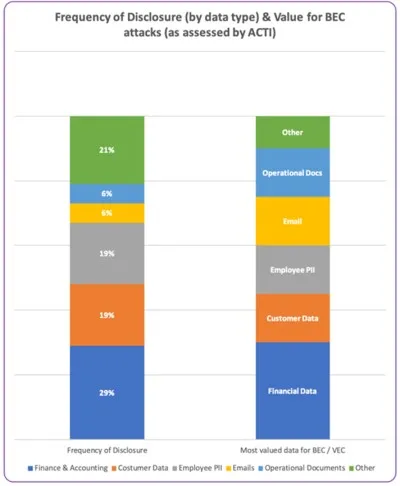
Devoted leak websites mostly present monetary knowledge, adopted by worker and shopper personally identifiable data, and communication documentation. The rise of double extortion makes an attempt – the place assault teams use ransomware to exfiltrate knowledge after which publicize the information on devoted leak websites – has made giant quantities of delicate company knowledge accessible to any menace actor. Essentially the most precious sorts of knowledge most helpful for conducting BEC assaults are monetary, worker, and communication knowledge, in addition to operational paperwork. There’s a vital overlap between the sorts of knowledge most helpful for conducting BEC assaults and the sorts of knowledge mostly posted on these ransomware leak websites, ACTI Mentioned.
The information is a “wealthy supply for data for criminals who can simply weaponize it for secondary BEC assaults,” ACTI stated. “The first issue driving an elevated menace of BEC and VEC assaults stemming from double-extortion leaks is the provision of [corporate and communication data].”
Knowledge thieves are making it simpler for his or her prospects to seek out and entry the stolen data. The devoted leak websites are more and more accessible on publicly accessible websites, not hidden away on Tor domains, and a few supply searchable listed knowledge, to make it simpler for menace actors to seek out what they want for his or her assaults.
For instance, the operators of the data-selling market Industrial Spy manage and identify folders with labels that replicate their content material to make discovering particular information simple, ACTI stated. Prospects can use {the marketplace}’s search performance to seek out particular information akin to worker knowledge, invoices, scans, contracts, authorized paperwork, and electronic mail messages. The search may hunt for knowledge from particular industries and international locations.
“Listed and searchable databases like these assist actors extra effectively purchase particular knowledge versus downloading bulk knowledge and hoping to seek out desired data,” ACTI stated.