Two point-of-sale (PoS) malware variants have been put to make use of by a menace actor to steal data associated to greater than 167,000 bank cards from cost terminals.
Based on Singapore-headquartered cybersecurity firm Group-IB, the stolen information dumps might internet the operators as a lot as $3.34 million by promoting them on underground boards.
Whereas a big proportion of assaults geared toward gathering cost information depend on JavaScript sniffers (aka net skimmers) stealthily inserted on e-commerce web sites, PoS malware continues to be an ongoing, if much less well-liked, menace.
Simply final month, Kaspersky detailed new ways adopted by a Brazilian menace actor often known as Prilex to steal cash by the use of fraudulent transactions.
“Virtually all PoS malware strains have the same card dump extraction performance, however completely different strategies for sustaining persistence on contaminated units, information exfiltration and processing,” researchers Nikolay Shelekhov and Mentioned Khamchiev stated.
Treasure Hunter and its superior successor MajikPOS are alike in that they’re designed to brute-force their method right into a PoS terminal, or alternatively buy preliminary entry from different events often known as preliminary entry brokers, adopted by extracting cost card data from the system’s reminiscence, and forwarding it to a distant server.
It is value noting that MajikPOS first got here to gentle in early 2017, primarily affecting companies throughout the U.S. and Canada. Treasure Hunter (aka TREASUREHUNT), then again, has been chronicled since 2014, with its supply code struggling a leak in 2018.
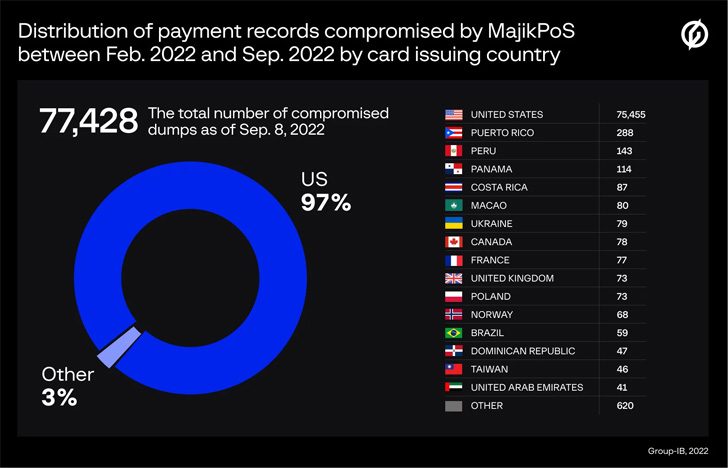
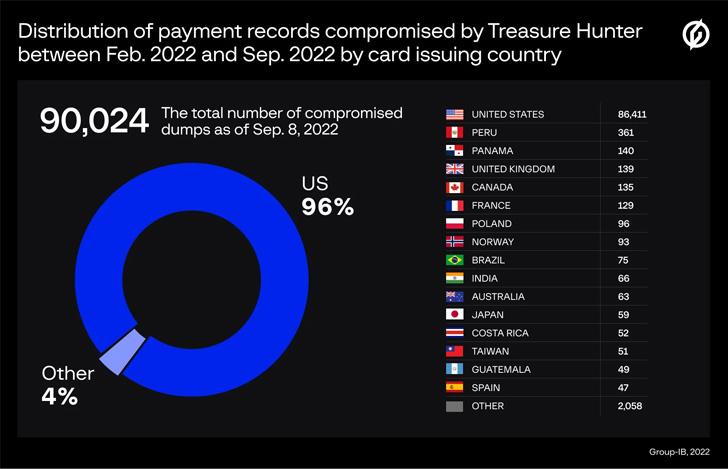
Group-IB, which recognized the command-and-control (C2) servers related to the 2 PoS malware, stated 77,428 and 90,024 distinctive cost information had been compromised by MajikPOS and Treasure Hunter between February and September 2022.
Many of the stolen playing cards are stated to have been issued by banks within the U.S., Puerto Rico, Peru, Panama, the U.Okay., Canada, France, Poland, Norway, and Costa Rica.
The identification of the felony actors behind the scheme is unknown, and it is at present not clear if the pilfered information has already been offered for financial positive aspects by the group.
This will have extreme penalties ought to the card-issuing banks not implement ample safety mechanisms, successfully enabling dangerous actors to make use of cloned playing cards to illicitly withdraw funds and make unauthorized transactions.
“PoS malware has change into much less enticing for menace actors lately because of a few of its limitations and the safety measures carried out inside the card cost trade,” the researchers stated.
“Nonetheless, […] it stays a big menace to the cost trade as an entire and to separate companies that haven’t but carried out the most recent safety practices. It’s too early to write down off PoS malware.”