A financially motivated cybercrime group has been linked to an ongoing wave of assaults geared toward hospitality, lodge, and journey organizations in Latin America with the aim of putting in malware on compromised programs.
Enterprise safety agency Proofpoint, which is monitoring the group beneath the title TA558 relationship all the way in which again to April 2018, referred to as it a “small crime risk actor.”
“Since 2018, this group has used constant techniques, strategies, and procedures to try to put in quite a lot of malware together with Loda RAT, Vjw0rm, and Revenge RAT,” the corporate’s risk analysis staff stated in a brand new report.
The group has been operational at the next tempo in 2022 than regular, with intrusions primarily geared in direction of Portuguese and Spanish audio system in Latin America, and to a lesser extent in Western Europe and North America.
Phishing campaigns mounted by the group contain sending malicious spam messages with reservation-themed lures corresponding to lodge bookings that include weaponized paperwork or URLs in a bid to entice unwitting customers into putting in trojans able to reconnaissance, information theft, and distribution of follow-on payloads.
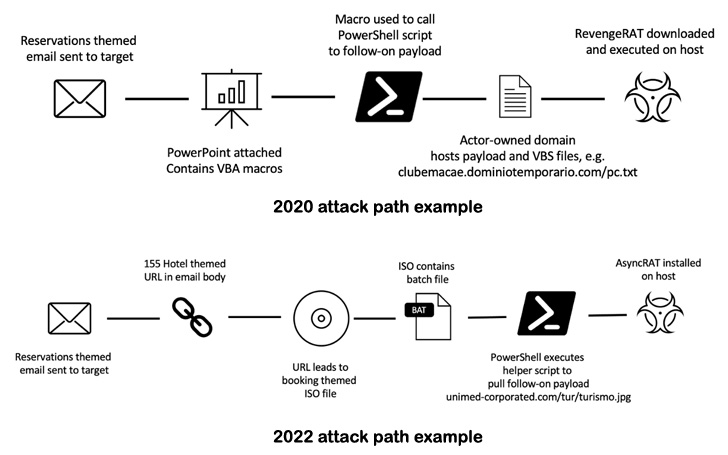
The assaults have subtly advanced over time: Those noticed between 2018 and 2021 leveraged emails with Phrase paperwork that both contained VBA macros or exploits for flaws corresponding to CVE-2017-11882 and CVE-2017-8570 to obtain and set up a mix of malware corresponding to AsyncRAT, Loda RAT, Revenge RAT, and Vjw0rm.
In latest months, nevertheless, TA558 has been noticed pivoting away from macro-laden Microsoft Workplace attachments in favor of URLs and ISO recordsdata to attain preliminary an infection, a transfer probably in response to Microsoft’s determination to dam macros in recordsdata downloaded from the online by default.
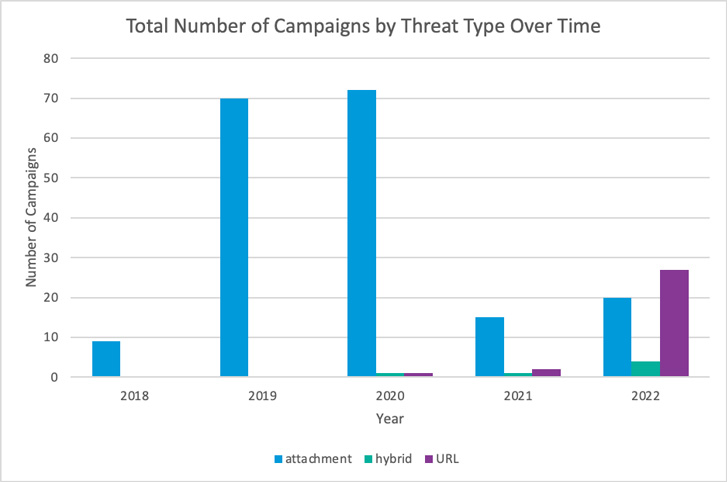
Of the 51 campaigns carried out by the group to this point this 12 months, 27 of them are stated to have integrated URLs pointing to ISO recordsdata and ZIP archives, compared to simply 5 campaigns altogether from 2018 via 2021.
Proofpoint additional famous that the intrusions chronicled beneath TA558 are a part of a broader set of malicious actions specializing in victims within the Latin American area. However within the absence of any post-compromise exercise, it is suspected that TA558 is a financially motivated cybercriminal actor.
“The malware utilized by TA558 can steal information together with lodge buyer person and bank card information, permit lateral motion, and ship follow-on payloads,” the researchers stated. “Exercise performed by this actor may result in information theft of each company and buyer information, in addition to potential monetary losses.”