Attackers proceed to seek out vital success focusing on unpatched servers and susceptible remote-access programs, researchers say — and these kinds of compromises price sufferer organizations 54% greater than compromises brought on by consumer actions (i.e., falling for phishing and opening malicious paperwork).
In response to a Wednesday report by safety agency Tetra Protection, which analyzed incident knowledge from the primary quarter, unpatched vulnerabilities and exposing dangerous companies—akin to Distant Desktop Protocol (RDP)—account for 82% of profitable assaults, whereas social-engineering staff to take some motion accounted for simply 18% of profitable compromises.
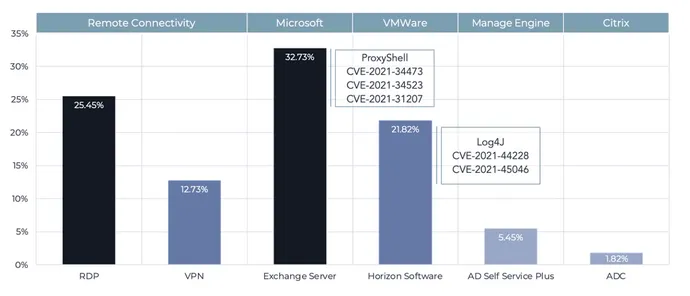
Incident knowledge collected by the agency confirmed that the ProxyShell exploit for Microsoft Change servers accounted for a few third of exterior breaches, whereas insecure Distant Desktop Protocol (RDP) servers accounted for 1 / 4.
Whereas the Log4Shell bug continued to see quite a lot of media protection, the assault vector was solely utilized in 22% of breaches, says Nathan Little, senior vice chairman of digital forensics and incident response (DFIR) at Tetra Protection.
“We count on these techniques to proceed—nevertheless, there’s a finite quantity of susceptible Change servers,” he says. “Over time—and now we have seen this over the previous five-plus years—the vulnerabilities which can be utilized by risk actors will change, however [in general] externally accessible vulnerabilities will proceed to be a favourite assault vectors for cybercriminals.”
Healthcare topped the record of focused industries, with almost 20% of compromised organizations falling in that class. Finance and schooling tied for second at 13%, and manufacturing accounted for 12% of incidents, in accordance with Tetra Protection’s knowledge.
Tetra Protection additionally tracked the cybercrime actors liable for most breaches, and located that 4 teams—Lockbit 2.0, BlackCat, Conti, and Hive—are liable for about half of all compromises investigated by the agency.
Cloud Misconfiguration: Much less Pricey Than Different Cyber-Incidents
Whereas a typical type of vulnerability, misconfigurations didn’t account for a lot of the price of breaches, with few requests to research such compromises, Tetra Protection’s Little says.
“For misconfigurations—as a result of they’ll vary from an AWS S3 bucket being publicly accessible with delicate data saved in it — to a non-sensitive server being uncovered with a default username and password — the prices can vary drastically,” he says. “Usually talking, the prices of misconfiguration are decrease than unpatched programs and unintended consumer motion.”
Whereas damages are arduous to estimate, Little sees the potential impression as a proportion of income, with an inexpensive monetary impression of a significant cybersecurity incident accounting for two% to 10% of annual income.
He additionally notes that two controls — complete patching and utilizing multifactor authentication (MFA) — may have prevented almost 80% of the investigated incidents. That features 57% of exterior compromises that used an unpatched vulnerability, and the 13% of profitable assaults on digital non-public networks that both exploited a vulnerability or used stolen credentials to realize entry the place there was not MFA enabled, Little says.
“This exhibits that these two controls alone would have a drastic impression in lowering the chance of a ransomware incident,” he says. “The price financial savings for an organization could be the distinction between having an information breach and ransomware incident that would cease enterprise for every week or extra and trigger reputational hurt or not.”
Conflicting Information
Information on profitable compromises will help corporations decide probably the most essential assault vectors to handle, however it must be famous that the conclusions rely significantly on the precise incident-response agency.
As an example, earlier this 12 months, security-advisory agency Kroll noticed phishing proceed to develop, with 60% of the circumstances the corporate investigated utilizing phishing assaults because the initial-access vector. In the meantime, the exploitation of vulnerabilities dropped by half to 13% of all preliminary compromises, down from 27% in This autumn 2021.
“Regardless of a lower in ransomware incidents and the disruption and publicity of a variety of key risk teams … 2022 is proving to be the 12 months of attacker range, with actors exploiting new strategies, akin to e mail compromise, resulting in extortion,” Kroll said in its newest quarterly risk panorama report.
Ransomware Spike
By the use of context, in February, incident-response agency CrowdStrike launched its annual report by itself incident knowledge from 2021 displaying that breaches associated to ransomware assaults had grown by 82%. As well as, the corporate’s knowledge confirmed that malware had solely been utilized in solely 38% of profitable intrusions, with 45% of attackers manually conducting the assaults.
The common time to maneuver from an preliminary compromise to attacking different programs on the community—what CrowdStrike calls the “breakout time”—remained close to 1.5 hours, in accordance with the corporate’s knowledge.


