Attackers are piggybacking on the facility of the Fb model by utilizing emails that appear like they’re coming from Fb Adverts Supervisor. The concept is to lure victims into coughing up credentials and bank card info on a Fb lead technology type.
In response to a Tuesday report by the safety analysis staff at Avanan, attackers are sending phishing messages that seem like pressing warnings from Meta’s “Fb AdManager” staff. The messages declare the sufferer isn’t complying with the corporate’s advert insurance policies and that the advert account can be disabled if the goal does not enchantment the phony violation.
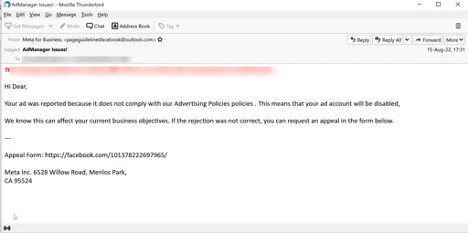
The “enchantment type” hyperlink results in a credential harvesting website that makes use of an actual Fb lead-generation type to gather passwords and bank card info.
Abusing the Fb Adverts System
An attention-grabbing side to the marketing campaign is that moderately than utilizing a harvesting website hosted on a sketchy IP someplace, attackers are gaming the Fb advertisements system to create lead-generation types with malicious intent. Doing so kills two birds with one stone: To start with, it fools quite a lot of automated checks for malicious hyperlinks utilized by e mail platforms. Utilizing official websites is what the Avanan staff refers to because the Static Expressway.
“Hackers are leveraging websites that seem on static Permit Lists,” defined Jeremy Fuchs, cybersecurity researcher for Avanan, within the report. “That implies that e mail safety providers have broadly determined that these websites are reliable, and thus something associated to them comes by to the inbox.”
Moreover, utilizing Fb Adverts types additionally affords a excessive diploma of verisimilitude for any of the eight billion promoting customers that Fb works with who’re already aware of the Adverts Supervisor platform and the lead-generation types it produces.
“For the tip consumer, seeing that their Fb advert account has been suspended is trigger for concern,” Fuchs mentioned. “Because it’s a official Fb hyperlink, the consumer would really feel assured persevering with on.”
Inform-Story Indicators of ‘Brandjacking’
Fuchs wrote that whereas the websites used on this credential harvesting marketing campaign gave the impression to be official, there’s a crimson flag within the phishing messages they uncovered: Usually, these are coming from Outlook accounts akin to [email protected]
Moreover, the bodily tackle footer within the emails are mistaken. But when customers did not discover these particulars, they may simply be foiled by this ploy.
In response to analysis launched earlier this yr, model impersonations, or brandjackings, like these elevated by 274% final yr as attackers proceed to hawk their scams by wanting like they arrive from dependable sources. Fb is a selected favourite amongst phishers to impersonate. A report launched by Vade this spring discovered Fb was the No. 1 impersonated model final yr, edging out perennial favourite Microsoft for the highest spot.
In response to Irregular Safety analysis detailing knowledge from the primary half of 2022, e mail assaults elevated by 48% in that timeframe, with greater than 1 in 10 assaults impersonating well-known manufacturers. Some 256 particular person manufacturers had been impersonated, with LinkedIn and Microsoft showing to be the favorites up to now in 2022.


