ACM.51 Producing a random worth for batch job IDs
This can be a continuation of my collection on Automating Cybersecurity Metrics.
On the time of this writing we’re the purpose in our structure the place we need to set off a batch job.
I may simply run off and use some code on-line to implement a batch job on AWS. However my purpose will not be merely to get a batch job engaged on AWS. That might be easy. What I need to do is construct a safe structure that permits me to deploy and function batch jobs in a method that minimizes the possibilities of an information breach or safety incident.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Nonetheless ready for Google’s authorized staff to take away just a few websites listed right here which might be copying the contents of this weblog with out permission:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
One of many issues I want to do is to require MFA to run batch jobs as talked about once I began this collection. I’ve been fascinated by how to do that and whether or not there are holes in my concept and undecided but however we’ll simply begin constructing it and consider it as we go.
The very first thing I need to do is to create a novel batch job ID. With the intention to run a batch job, a batch job administrator will want a batch job ID and an MFA code. Each these two objects come from two separate sources so that’s is a part of true MFA as I defined in my guide on the backside of this submit. We’re doubtlessly getting the code on the identical telephone if we use a digital MFA gadget. I’ll revisit that in a later submit.
SMS Code Safety
We are able to textual content the batch job ID to the batch job administrator. How safe is that? Properly, lately some safety researchers defined how it’s potential to foil MFA codes despatched to your telephone at BlackHat 2022:
Properly, that’s not good. If we expect although our menace mannequin, there’s a probability that somebody may attempt to get the SMS code if we textual content it to a person. Nonetheless, the SMS code will not be the one factor the person will want. They may even want an MFA code. So we’ve got a little bit of safety there.
Since I’m at the moment in improvement I’m going to stay with texting an administrator a job ID for the second, as a result of I’m additionally planning on doing different issues to make it tougher for somebody apart from my batch job directors to make use of that code down the road. I may even construct an entire cell software to deal with this a part of the equation, however then I’d have all of the complexity that comes with constructing a securing a cell app, so we’ll begin with the SMS codes.
Session IDs and why cryptographically safe random values matter
One of many issues to contemplate when producing a novel code is whether or not or not it’s really random. Many safety vulnerabilities come from system implementations that don’t use really random values. What’s the issue with values that aren’t really random? They could be simpler for an attacker to guess. They can break encryption an entry techniques.
Think about a case the place a corporation has a web site that makes use of Session IDs to determine a person at the moment lively within the system and grant them entry. With the intention to get that Session ID, the person needed to login and show who they had been, after which the net software handed them again a Session ID.
What can the attacker do in the event that they get ahold of a Session ID? Something that person that originally obtained the session can do within the system. It’s as if the attacker is the person logged into the system as a result of that’s how the person is recognized after they submit an HTTP request.
Due to this fact Session IDs ought to usually solely be legitimate for a brief time frame after which expire, at which level the person has to re-authenticate. That method, if an attacker will get the Session ID, they will solely use it for a restricted time frame.
How may an attacker get the session ID? There are so might methods and that’s one thing I check for on penetration assessments. However for the needs of this weblog submit the style through which the person could possibly receive the Session ID is by guessing the session ID as a result of it’s not really random. Maybe the system generates a Session ID that’s the first preliminary of the person’s first identify and the final identify of the person. An attacker logins in and sees this within the URL:
https://banksite.notsecure?sessionid=tradichel
Clearly, if I login and see that I can simply attempt to guess who the opposite customers could be or I would even know some customers. I can simply change the session ID to get entry to the system as if I used to be that person:
https://banksite.notsecure?sessionid=mjordan
Now let’s say that you simply determine as an alternative to make use of Python’s random library:
You would possibly get a session that appears random, however it’s actually not a cryptographically safe random quantity.
Random Quantity Generator Assault
If you wish to dig into how attackers would possibly attempt to exploit non-random quantity turbines listed below are some hyperlinks:
Cryptographically Safe Random Values
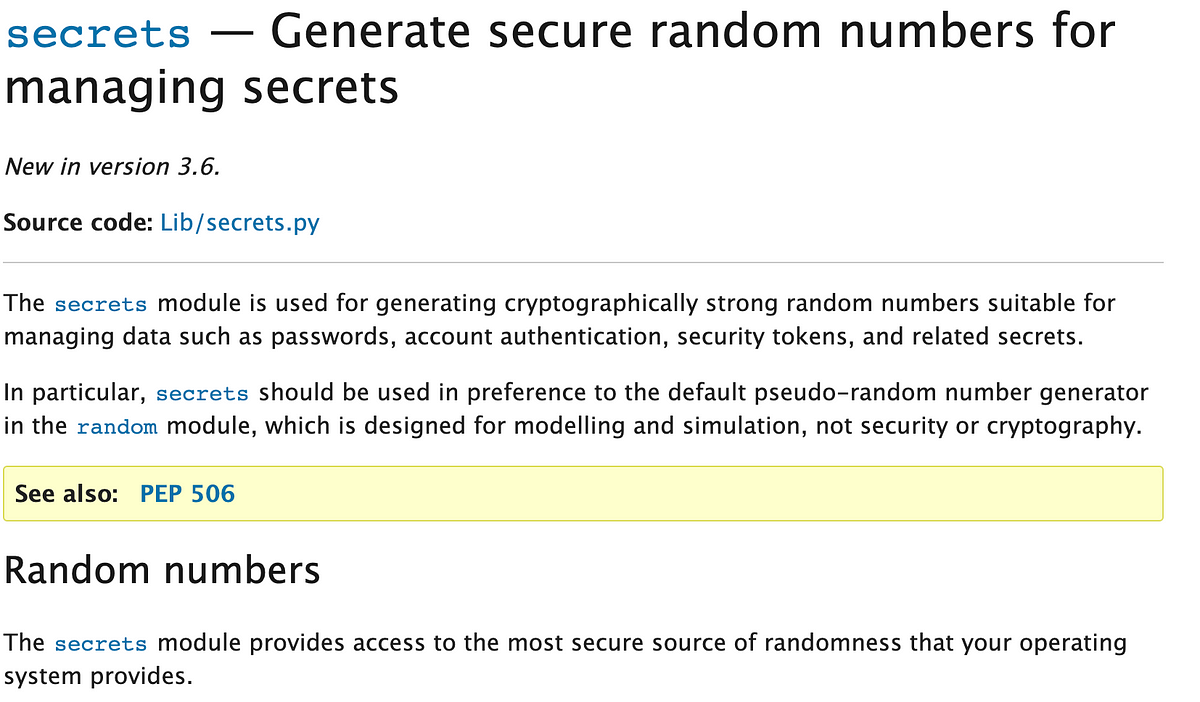
So if we will’t use python’s random module what can we use? There’s one other module in Python that claims to generate cryptographically safe values referred to as secrets and techniques.

If we care about having the job ids which might be really distinctive so somebody can’t guess and begin a job id then we will use the above. We may have loads of different controls round operating jobs in our system so I’m undecided how a lot good a job ID alone could be to an attacker, however the distinction in implementation time for me to make use of a safer library is mainly nothing. I’m going to make use of essentially the most safe choice each time I can.
It doesn’t matter what programming language you utilize it would be best to make sure that you utilize a cryptographically safe random quantity generator, not a flawed library or module with identified points. Do your homework earlier than you utilize some code you pulled off the Web or seize the primary library you come throughout in terms of random quantity era. Additionally examine any code you utilize from open supply libraries to make sure they’re utilizing a cryptographically safe random quantity generator.
We’ll be the secrets and techniques Python module in a Lambda perform to kick off our batch job course of. Observe for updates.
Teri Radichel
In case you appreciated this story please clap and observe:
Medium: Teri Radichel or E-mail Listing: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests companies through LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this collection:
____________________________________________
Creator:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, shows, and podcasts