Spotify’s Backstage has been found as susceptible to a extreme safety flaw that might be exploited to achieve distant code execution by leveraging a lately disclosed bug in a third-party module.
The vulnerability (CVSS rating: 9.8), at its core, takes benefit of a vital sandbox escape in vm2, a well-liked JavaScript sandbox library (CVE-2022-36067 aka Sandbreak), that got here to gentle final month.
“An unauthenticated risk actor can execute arbitrary system instructions on a Backstage software by exploiting a vm2 sandbox escape within the Scaffolder core plugin,” software safety agency Oxeye mentioned in a report shared with The Hacker Information.
Backstage is an open supply developer portal from Spotify that enables customers to create, handle, and discover software program parts from a unified “entrance door.” It is utilized by many corporations like Netflix, DoorDash, Roku, and Expedia, amongst others.
In accordance with Oxeye, the flaw is rooted in a instrument referred to as software program templates that can be utilized to create parts inside Backstage.
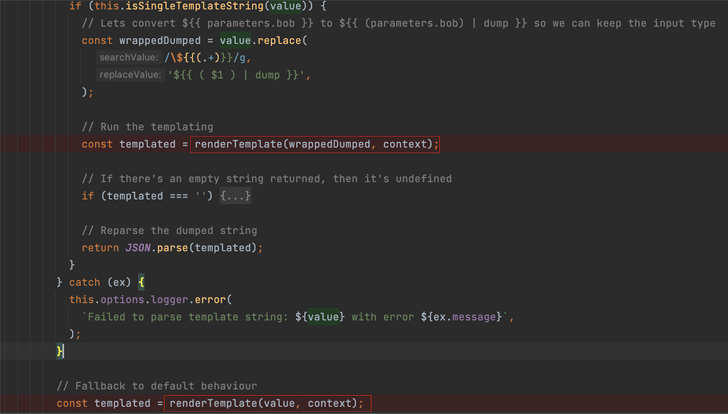 |
| Screenshot reveals Backstage calling the renderTemplate operate (that calls renderString2) twice within the occasion of an error. |
Whereas the template engine makes use of vm2 to mitigate the danger related to working untrusted code, the sandbox escape flaw within the latter made it attainable to execute arbitrary system instructions exterior of the safety perimeter.
Oxeye mentioned it was in a position to establish greater than 500 publicly-exposed Backstage cases on the web, which might then be remotely weaponized by an adversary with out requiring any authorization.
Following accountable disclosure on August 18, the difficulty was addressed by the mission maintainers in model 1.5.1 launched on August 29, 2022.
“The basis of any template-based VM escape is gaining JavaScript execution rights throughout the template,” the Israeli firm famous. “Through the use of ‘logic-less’ template engines corresponding to Mustache, you possibly can keep away from introducing server-side template injection vulnerabilities.”
“Separating the logic from the presentation as a lot as attainable can tremendously cut back your publicity to probably the most harmful template-based assaults,” it additional added.



