Cybercriminals focusing on the retail and hospitality {industry} are sticking to tried and examined menace vectors resembling credential harvesting and phishing, in keeping with evaluation by the Retail & Hospitality Data Sharing and Evaluation Middle (RH-ISAC).
An ISAC is an industry-specific group that acts as a centralized repository of knowledge on threats affecting a particular {industry} sector. Member organizations share menace intelligence and mitigation info, with the concept that organizations can put together their defenses higher in the event that they know the sorts of assaults their friends are experiencing.
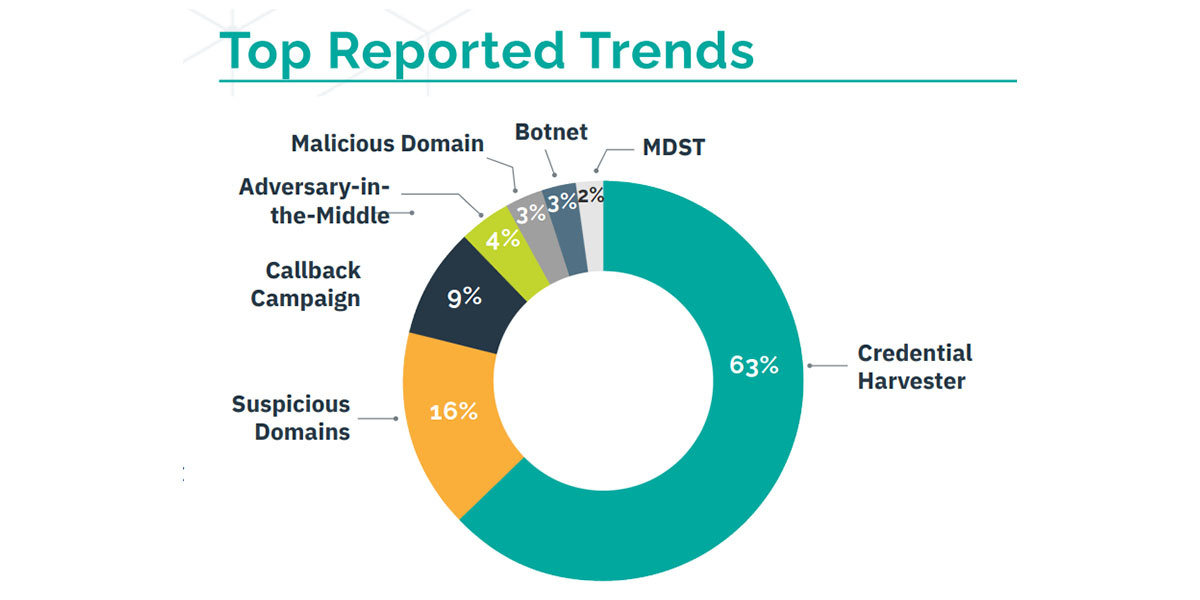
The RH-ISAC Intelligence Traits Abstract, which encompasses info shared by member organizations from Could to August, highlights shifts within the menace panorama for the retail, hospitality, and journey sectors. Credential harvesting was “by far essentially the most prevalent reported menace,” at 63%, in keeping with the Intelligence Traits Abstract. Suspicious domains had been the second most prevalent, at 16%. Different menace indicators reported by members embody malicious domains (3%), botnets (3%), and adversary-in-the-middle assaults (4%).
Ten malware households made up 81% of whole reviews the RH-ISAC tracked through the four-month interval, of which Emotet was essentially the most prevalent. Whereas it is attainable that the rise in Emotet-related reviews might be related to member organizations’ focusing extra on Emotet protection, it additionally means that Emotet exercise is “as soon as once more regular after the group’s reemergence earlier this yr,” the report says.
RH-ISAC is not nearly reporting menace indicators — member organizations additionally share details about particular menace matters. The Prime Shared Traits graph is an indicator of what sort of threats organizations are most involved about.
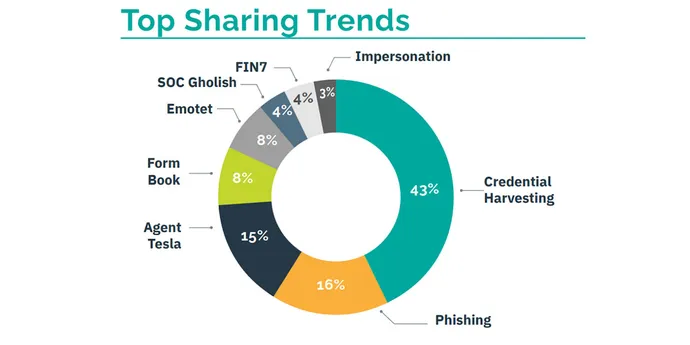
Credential harvesting stays the most typical menace shared by members, at 43%, adopted by phishing, at 16%. Details about malware assaults — particularly Agent Tesla, Formbook, and Emotet — made up 31% of the threats shared by members.
Prime Shared Traits define the frequency of sharing concerning a menace subject, whereas Prime Reported Traits graph reveals the quantity of menace indicators shared associated to a given subject, in keeping with RH-ISAC.