ACM.36: Instruments and methods to create zero belief useful resource, IAM, and Belief insurance policies on AWS (Zero Belief Insurance policies ~ Half 1)
This can be a continuation of my collection on Automating Cybersecurity Metrics.
Within the final submit we created a IAM function coverage with permissions that have been a lot too broad. Now we wish to prohibit the IAM function coverage to solely what the function requires to carry out the actions the function simply did once we created our new Entry Key.
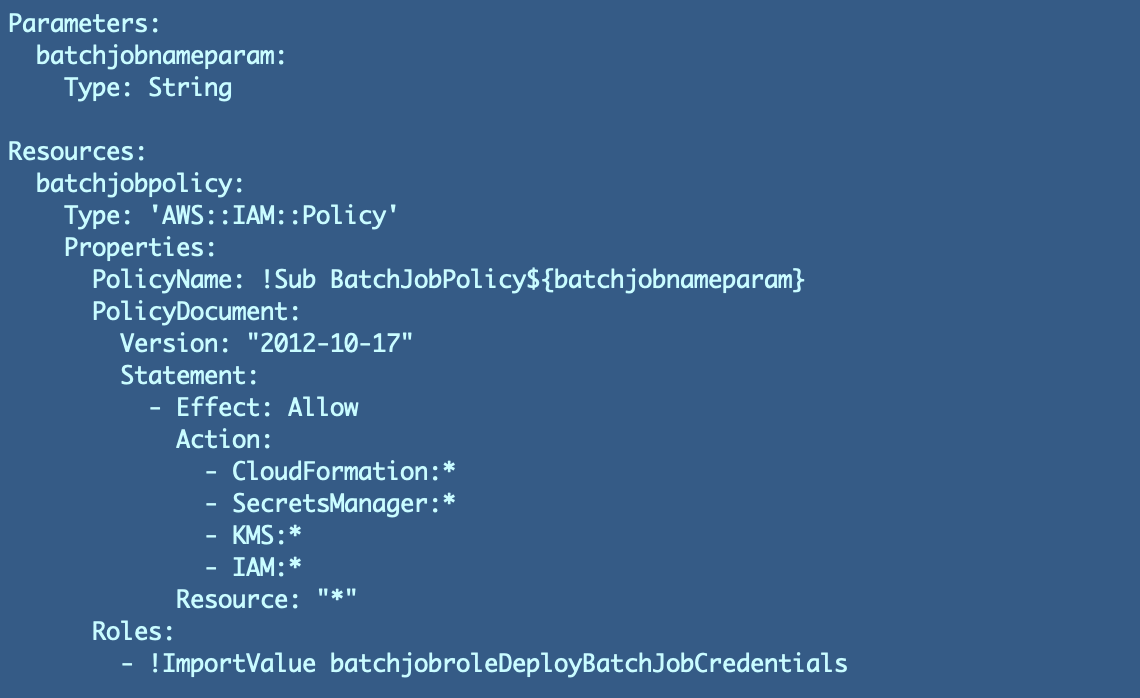
As a reminder the function coverage is discovered on this file within the GitHub repo:
/jobs/iam/DeployBatchJobCredentials/cfn/policy_batch_job.yaml
It seems like this with very broad entry and no useful resource restrictions:
With the intention to see what actions the function took and create a coverage we have now a number of choices, a few of which don’t presently work for all use circumstances.
- AWS Entry Advisor — which ought to give us an inventory of actions the person took in CoudTrail logs.
- AWS Entry Advisor Coverage Generator — which ought to use the above info to generate a coverage.
- CloudTrail Logs — when all else fails, we should always be capable to question CloudTrail logs to see what actions the person took.
- Trial and Error — Give the person or function no permissions after which attempt to take the actions you wish to carry out. Repair every error message by including permissions because it happens. Sadly, for those who get error message that don’t let you know what service or useful resource the person couldn’t entry, this shall be troublesome.
IAM Entry Analyzer
That is fascinating. I wrote about IAM Entry Analyzer in a separate weblog submit (not a part of this collection) and it seems like we have now a brand new message on the display now that explains that this characteristic solely works with sure AWS companies.

Though the message on the display says in any other case, entry analyzer lists all of the companies our function used. Nonetheless, it solely exhibits the actions for the companies listed: EC2, IAM, Lambda, and S3. So of the companies used we will solely get the precise actions taken for IAM. Let’s take a look at what it offers for IAM.
Click on the hyperlink for IAM. Right here we will see the IAM actions the function took.
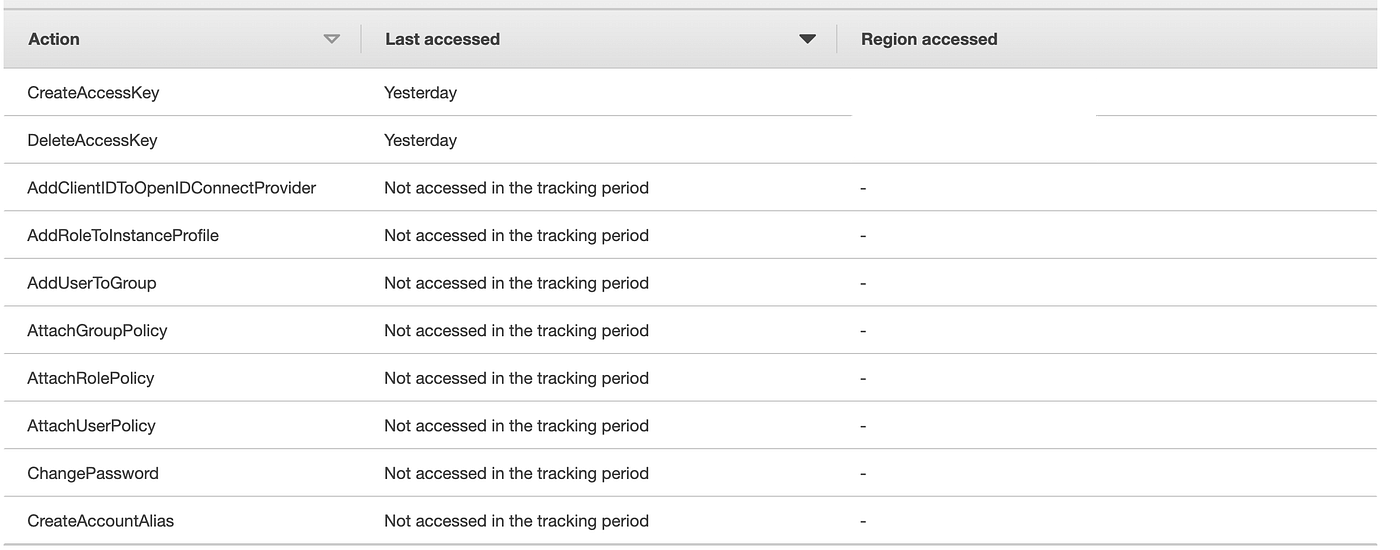
Solely two actions within the above record have been utilized by our function to create the credentials. We are able to change iam.* with solely these two actions. Now our coverage seems like this:

Warning on granting full administrative permissions:When you see iam.* in a coverage that's just like area admin in a Home windows Energetic Listing atmosphere. Perceive who has these permissions and why. Restrict their use if potential to solely activated when wanted, requiring MFA, or different restrictions to restrict their potential abuse. What I am exhibiting you here's a higher different. Create jobs for particular actions and use these jobs with particular roles and insurance policies as an alternative of giving full IAM entry.Additionally, simply because a person has to "swap" to an IAM function doesn't suggest a lot. If an attacker has entry to their energetic session or person credentials, they can also "swap" to the IAM function. For this reason, though SSO is helpful, it's also dangerous if you give a person entry to a number of highly effective roles throughout the enterprise.An Azure you need to use a characteristic known as Simply-In-Time entry which you'll be able to set as much as require a second occasion to authorize permissions earlier than performing some administrative actions. You are able to do the identical factor on AWS, you simply have to create that performance your self. I hope that performance involves AWS sometime:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/just-in-time-access-overview?tabs=defender-for-container-arch-aksActually, I wrote a weblog submit concerning the idea for AWS earlier than the Azure characteristic was accessible with an IOT button to permit entry to connect with a VPN. Similar idea, totally different utility.
https://aws.amazon.com/blogs/aws/just-in-time-vpn-access-with-an-aws-iot-button/
Once I examined earlier it didn’t seem that IAM Entry Analyzer confirmed cross-account actions. I have to additional discover this idea now that it’s clear that this characteristic solely works for sure companies as a result of I imagine I used to be testing KMS on the time. Actually, I couldn’t discover the cross-account logs in any respect. This web page states that actions needs to be current in each accounts. We’ll revisit that if I get again round to establishing cross-account KMS key administration.
What can be nice is that if this IAM coverage generator UI would mean you can choose a person or function after which it could solely embody the actions taken by that person or function, and any assets it accessed. Then it could let you choose from that subset because it does beneath to incorporate which objects you need in your coverage. Then it could output a coverage **in both JSON or YAML** (there needs to be a straightforward conversion library to do this) which you could possibly use in a CloudFormation template.
SSO (I do know it has a brand new identify, nevertheless it’s nonetheless SSO) appears to be off on it’s personal island and missing among the performance on this submit — and all my posts actually. I hope these helpful options should not misplaced within the push for integration.
Entry Advisor Coverage Generator
As of but, I’ve not been capable of get the IAM Entry Advisor Coverage Generator to work. It appears to me that’s probably associated to the above situation the place IAM Entry Advisor doesn’t present you all of the actions taken by an IAM function. I presume I used to be utilizing companies that the coverage generator didn’t assist however the error message after it ran didn’t inform me that.
Nonetheless, in case you are solely utilizing the companies proven on the above display shot, this may occasionally be just right for you.
Click on on any person or function and scroll to the underside of the web page. Click on the Generate coverage button and comply with the directions on the display.

This can be a actually nice characteristic. Nonetheless I’d like to have the ability to select which of the actions a person took that I wish to embody in my coverage when generated, in addition to detailed assets I wish to enable the person to entry. It additionally must work with cross-account roles.
CloudTrail
One technique to a zero-trust coverage we’re going to overview actions taken in CloudTrail logs with AWS Athena. With the intention to make certain you need to use Athena on the finish of this submit, be sure you have CloudTrail enabled with an S3 bucket. When you don’t have a path or a bucket comply with this tutorial to set that up:
CloudTrail logs could take 5 minutes or so to look, relying on how you might have it configured. You will discover the small print of the timing of log entries within the CloudTrail documentation.
Let’s test CloudTrail for the actions take by our function. Copy the identify of the function.
Navigate to CloudTrail. Click on View Full Occasion Historical past on the backside of the historical past record. Click on Create Athena Desk.

Select the bucket that comprises your CloudTrail logs.
Click on Create Desk.
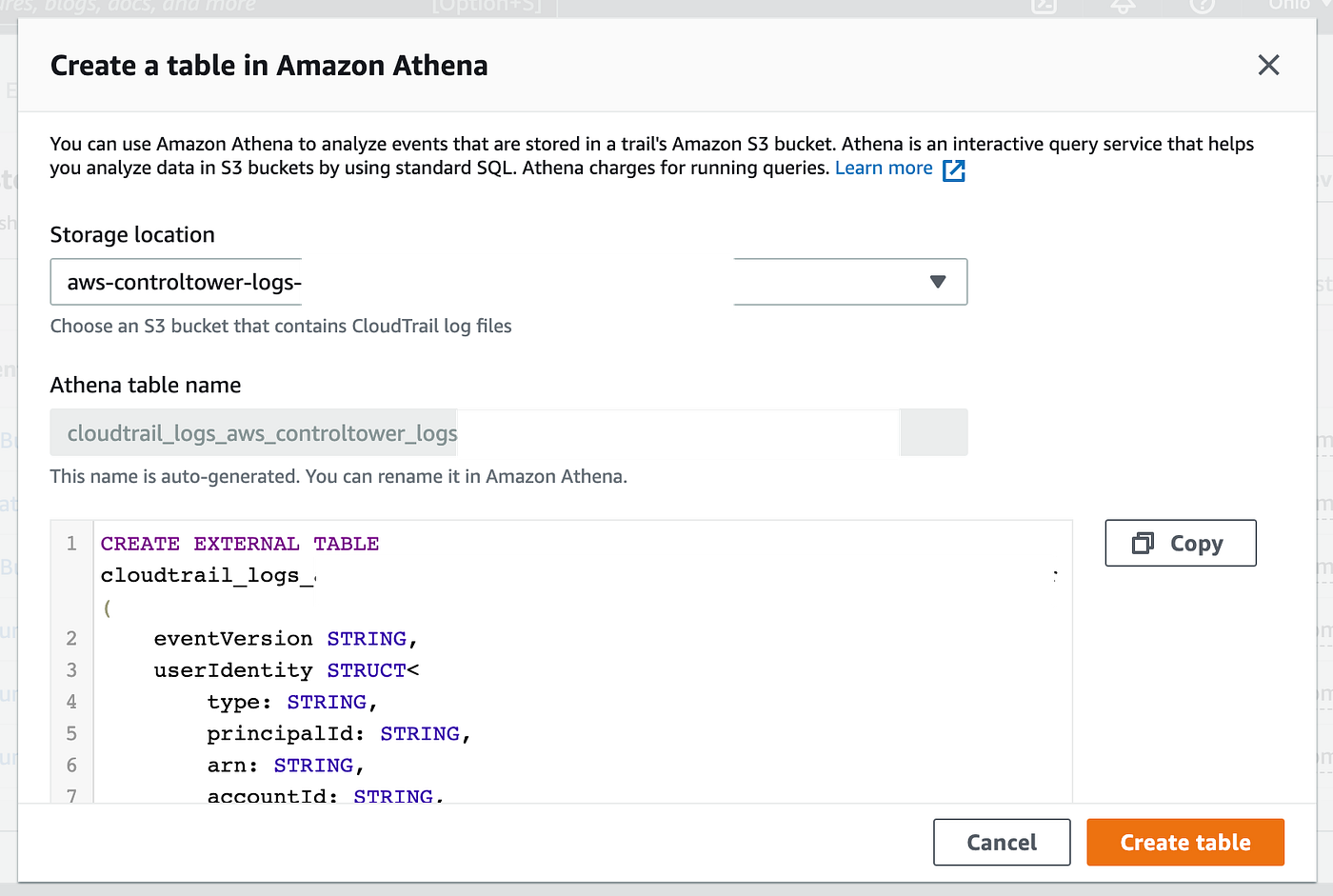
Click on the hyperlink on the prime to go to the Athena desk.

Right here’s the place I hit an error and stopped for some time. I submitted the request to Amazon by way of the #awswishlist to assist resolve this situation.
I ended up getting covid in between and hadn’t heard again so I went forward and took one other crack at fixing this drawback however hit the next highway blocks:
I’ve used Athena up to now and it was a part of my cloud safety class. However at this level, I’ve spent a lot time on this and I’m not attempting to put in writing a weblog submit on any of that I’m simply attempting to question cloud path to repair my coverage. This submit is already fairly lengthy so I’ll proceed it within the subsequent the place I check out CloudTrailLake as an alternative.
Observe for updates.
Teri Radichel
When you preferred this story please clap and comply with:
Medium: Teri Radichel or Electronic mail Listing: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests companies by way of LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this collection:
____________________________________________
Creator:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration take a look at or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety lessons, articles, white papers, shows, and podcasts


