Cybercriminals goal firms with high-value belongings to steal knowledge, expose infrastructure vulnerabilities, and to spoil buyer confidence. The typical value of an information breach, in keeping with the Price of a Information Breach Report 2021 by IBM Safety, is $161 ($146 in 2020) per report. And the typical complete value of an information breach in 2021 is $4.24 million, up from $3.86 million in 2020. The prices of preventing cybercrime, restoring knowledge and providers following a breach, misplaced income, and fame harm are growing. Some industries, equivalent to healthcare, monetary establishments, and pharmaceutical corporations are hit hardest by cybercrime and its prices. The healthcare business’s cybercrimes prices rose 29.5 % from 2020 to 2021.
Misplaced enterprise accounts for the most important portion of cybercrime prices to companies at 38 % of the $4.24 million. Detection and escalation is liable for 29 % of that quantity, post-breach response is available in at 27 %, and notification finishes final at 6 %. Misplaced enterprise prices embody fame harm, buyer turnover, and system downtime.
On this article, we have a look at knowledge safety, software program knowledge safety, and software safety which incorporates an summary of some preventative and proactive measures that companies can take towards cybercrime.
Information safety
Some companies thrive on knowledge. They ingest it, manipulate it, create experiences from it, whereas others create knowledge for others to make use of. And for some companies, the information they create is their mental property. Cybercriminals who need to steal, promote, or just expose knowledge search out high-value knowledge equivalent to personally identifiable info (PII), which might be offered to different cybercriminals to commit id theft, to defraud bank card corporations, or to straight steal from sufferer’s financial institution accounts. Information safety is crucial for many who acquire, create, or work with knowledge, particularly knowledge that features PII or monetary info.
Information has three fundamental states, that are knowledge in-flight, in-transit, and at relaxation, although some sources outline these states in a different way. These areas are the place knowledge is susceptible to assault, clandestine seize, and corruption. All must be handled from a safety point-of-view to make sure integrity, security, and confidentiality.
In-flight
Information that’s in-flight is knowledge that’s being transferred over a community of some type. That community might be wired or wi-fi from a supply equivalent to an finish consumer or a distant gadget. It’s lively knowledge that’s being despatched and picked up, equivalent to a buyer getting into their info right into a product buy order type. It might be environmental knowledge being wirelessly transferred to an information collector from a distant climate station. It can be knowledge collected by a cybercriminal from a skimmer gadget at a financial institution the place victims enter their account info through an computerized teller machine to withdraw money.
For in-flight knowledge the answer to man-in-the-middle, community sniffing, or different dwell knowledge stream seize strategies, is to encrypt the information throughout transmission from the supply to the vacation spot. With sturdy encryption, AES-256 for instance, the information is unusable to cybercriminals as a result of they would want the decryption key to learn it.
In-transit
Information that’s in-transit is knowledge that’s within the technique of transferring between techniques, disks, networks, or different units for backup, catastrophe restoration (DR), archival functions, or disposal. Usually, knowledge in-transit has been compressed, deduplicated, or ready for archive. Two quite common strategies of preparation earlier than switch is to zip or to tar after which compress right into a bundle or tarball for simpler transmission.
All knowledge needs to be encrypted previous to transmission from one location to a different. Encrypting these packages or tarballs ensures that they can’t be unarchived and skim even when they’re disrupted or captured between their sources and their locations. It’s extremely beneficial that each one packaged knowledge be encrypted utilizing AES-256 encryption earlier than transferring between any two areas.
At relaxation
Information at relaxation can be susceptible to assault and exfiltration by cybercriminals. Information at relaxation implies that knowledge is in a saved state on disk, on tape, or inside a database. There are a number of strategies of encrypting knowledge at relaxation however the technique used needs to be able to AES-256 encryption.
Cybercriminals are persistent, can stay silent or close to silent for months, and may slowly exfiltrate knowledge at ranges that always function beneath alert thresholds however they will’t break sturdy encryption equivalent to AES-256, a minimum of not within the foreseeable future. Information in any respect phases and states should be encrypted from supply to focus on to disposal. No single safety measure can thwart each assault or legal. Safety requires fixed vigilance and a layered method on each endpoint. Within the subsequent part, the dialogue turns to software program safety.
Software program safety
Software program safety is a really broad matter that ranges from standalone software program functions to shopper and server functions on each ends of a shopper/server system to advanced N-tier functions, working techniques, platforms, and infrastructures. The variability and inconsistency in all points of those techniques make safety extraordinarily advanced. Have a look at the listing of units, software program, and platforms that companies of any dimension might need to take care of.
- Cellular units with quite a lot of working techniques
- Desktop, laptop computer, and Pill computer systems with quite a lot of working techniques and peripherals
- Virtualization know-how
- Server techniques utilizing Linux, Unix, and Home windows
- A number of {hardware} platforms and vendor options
- IoT units from completely different distributors
- Routers, switches, and WiFi units
- Digicam techniques
- PBX techniques
- Cloud options
You possibly can simply see from this listing that even a small group’s safety shortly turns into a posh difficulty. For proprietary techniques, you don’t have any management over fixes, patches, safety dangers, or replace frequency.
Add into this combine your personal in-house developed software program and you’ve got fairly the safety listing in your palms. Within the subsequent part, I cowl software safety for functions that you just develop in-house and have full software program improvement life cycle (SDLC) management over.
Software safety
There are a number of areas alongside the continual integration and steady deployment (CI/CD) pipeline (Determine 1) the place software safety testing can happen. The farther to the left one can check code, the sooner within the course of one can detect and remediate code safety flaws.
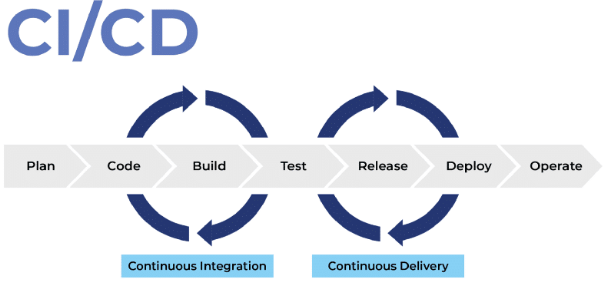
The 2 strategies of testing code early within the integration and supply course of are software program composition evaluation (SCA) and static software safety testing (SAST). They study uncompiled code for safety vulnerabilities. Combining these two vulnerability testing strategies early within the pipeline can alleviate many code flaws that result in insecure functions that end in breaches from assaults equivalent to injection, leaks, overflows, and cross-site scripting.
Early detection and remediation helps alleviate the potential for together with recognized vulnerabilities equivalent to these described in OWASP’s Prime Ten Net Software Safety Dangers, CWE Prime 25 Most Harmful Software program Weaknesses, and Widespread Vulnerabilities and Exposures (CVEs).
SCA
SCA testing scans your code for occurrences of open supply software program (OSS) which could embody vulnerabilities. These scans additionally aid you resolve any licensing points when utilizing code snippets from OSS functions.
SAST
SAST mixed with SCA permits builders to check and repair code early when it’s cheaper and fewer problematic to take action. SAST scans for weaknesses with out executing the code and prevents code flaws from flowing into manufacturing the place they develop into software vulnerabilities.
Scanning and remediating code early within the improvement course of doesn’t take away the necessity for late stage or post-production testing, but it surely removes apparent and recognized code flaws from being baked into functions previous to deployment.
Abstract
Web-facing net functions and their backend elements, together with saved and transferring knowledge, are beneath fixed scan, probe, and assault from cybercriminals, due to this fact a layered method to safety is important. Net functions might be scanned for code flaws and remediated early within the improvement course of by making use of the highly effective mixture of SCA and SAST. Through the use of this “left facet” testing and remediation course of, builders might be extra assured in releasing code to manufacturing. Nevertheless, steady vigilance and testing continues to be required on manufacturing functions to scan and remediate new vulnerabilities.
Content material supplied by Kiuwan.


