ACM.35: Creating Secrets and techniques in AWS Secrets and techniques Supervisor with CloudFormation
It is a continuation of my sequence on Automating Cybersecurity Metrics.
Let’s assessment the dependencies for this publish we created in prior posts.
We created a job for automated credential deployments for use by a batch job.
We created an AWS IAM person that’s allowed to imagine the batch job function:
We handed the batch job function into our KMS key coverage:
We added a coverage to our batch job function:
We refactored the function to work with an IAM Administrator Consumer.
We mounted an issue that would result in a confused deputy safety weak spot:
Now we are able to lastly deploy our credentials utilizing our new deployment function. We’re going to begin by getting the function working and repair the permissions a bit extra in subsequent posts.
CloudFormation Template to Create Credentials
The very first thing we’d like is a CloudFormation template that may create credentials for our batch job admin. Recall that we created this person in a earlier publish and assign digital MFA to the person, and each the person coverage and the batch job assume function coverage require MFA. The person doesn’t have permission to do something with out MFA so the credentials alone shouldn’t do anybody any good.
Even so we wish to restrict credential publicity so we’ll create them in an automatic means and retailer them in AWS Secrets and techniques Supervisor with out letting anybody see them.
Let’s check out the CloudFormation documentation for an entry key.
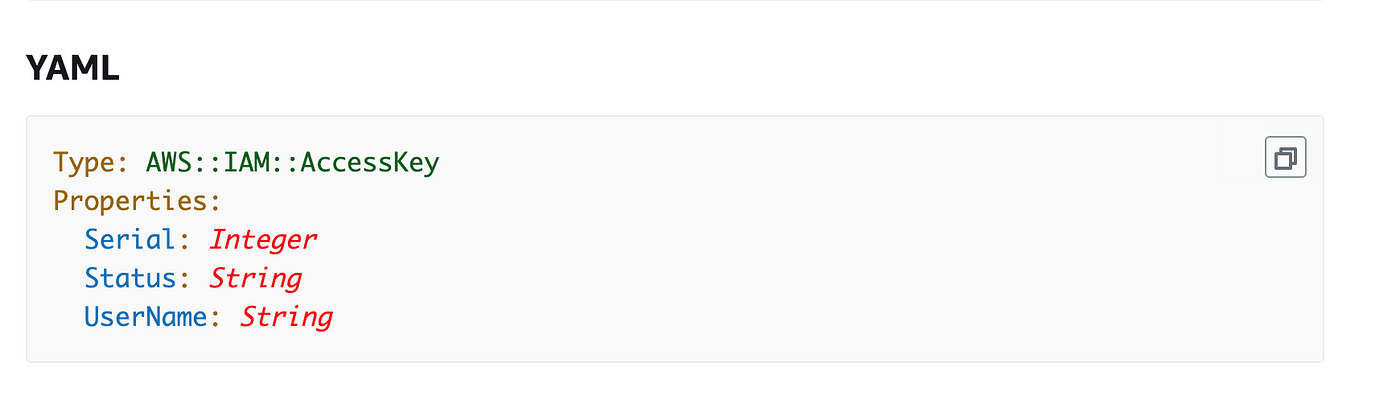
Serial isn’t required and used for rotation. We could revisit that later.
Standing: isn’t required. The allowed values are Lively and Inactive. Because the documentation doesn’t specify a default we’ll go in Lively.
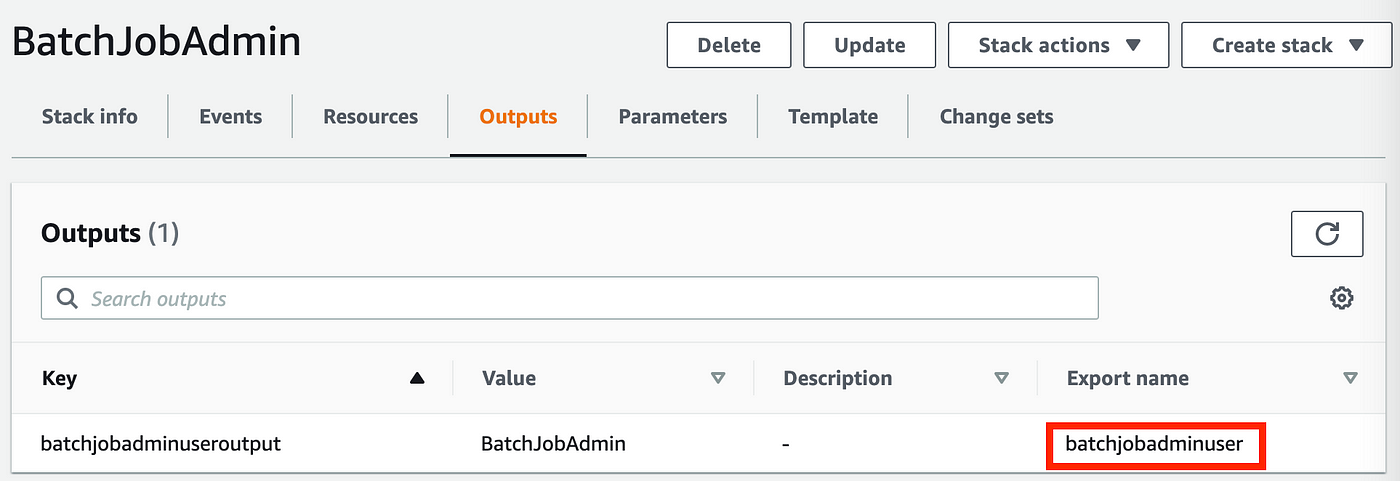
UserName is required. We’ll go in our batch admin username which is the output of our Batch Job Admin stack:
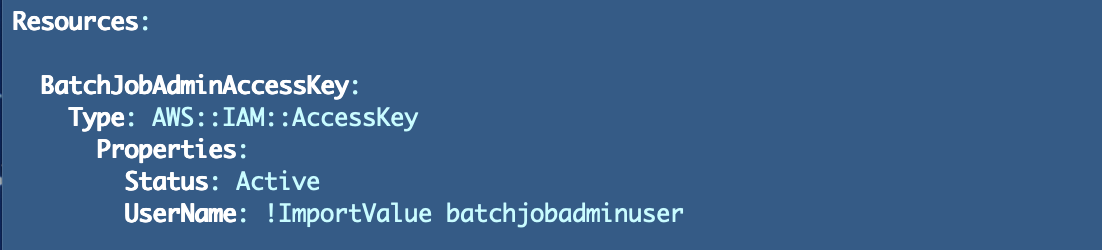
Create the template within the cfn listing for the batch job. I named the file:
credentials_batch_job_admin.yaml
Now how will be get entry to the credentials? Should you created these credentials within the console you’ll be capable of entry them on the level of creation, however after you allow that display screen there’s no strategy to get them once more. Head over to the documentation and search for Ref and GetAtt.
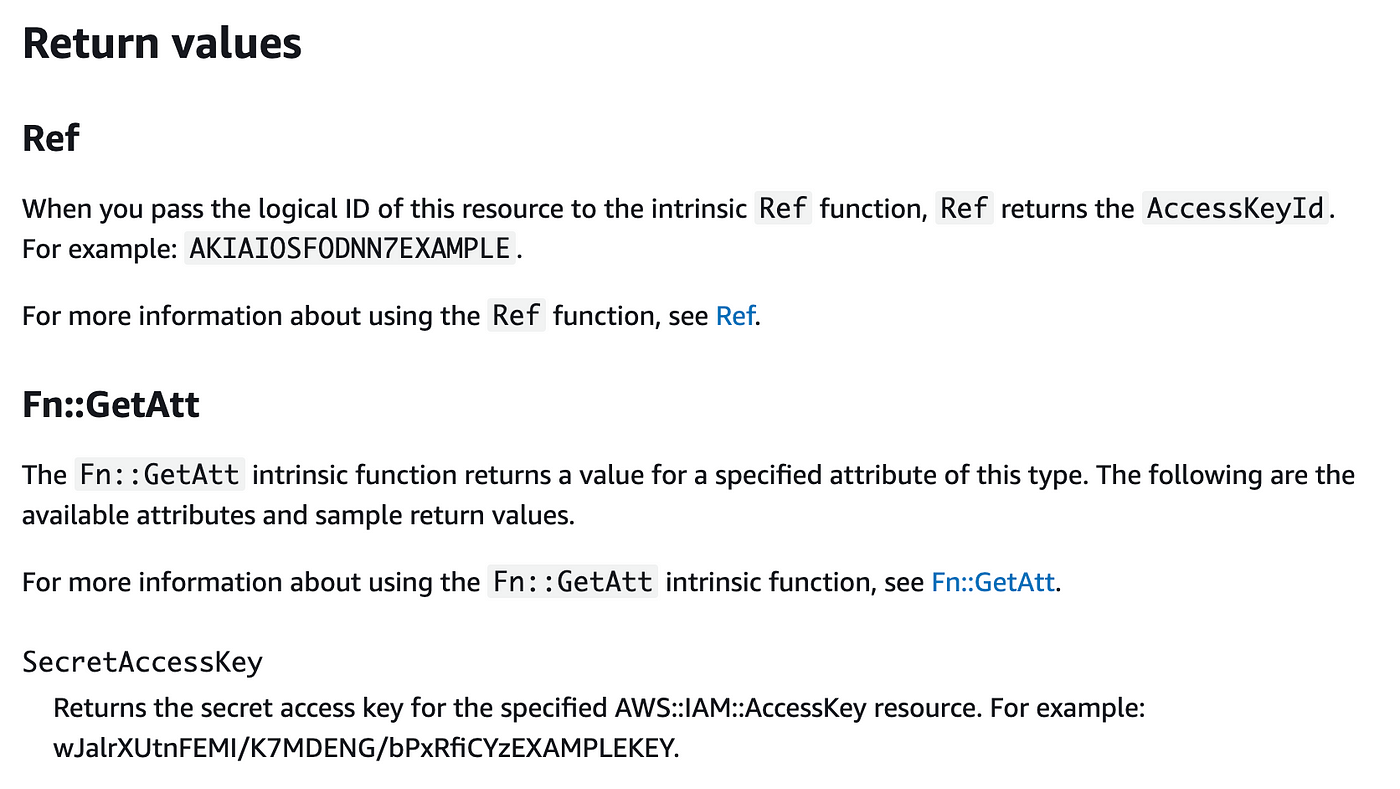
We are able to get our entry key id and secret entry key utilizing these constructs. On this case we positively do NOT wish to use a CloudFormation output. That may expose our credentials within the AWS Console to anybody who has entry to CloudFormation.
In an effort to keep away from that we’ll have to instantly create our Secrets and techniques Supervisor Secret right here and add our secrets and techniques instantly from Ref and GetAtt into our new secret.
CloudFormation for a Secret Supervisor Secret
Assessment the CloudFormation documentation for a Secret.
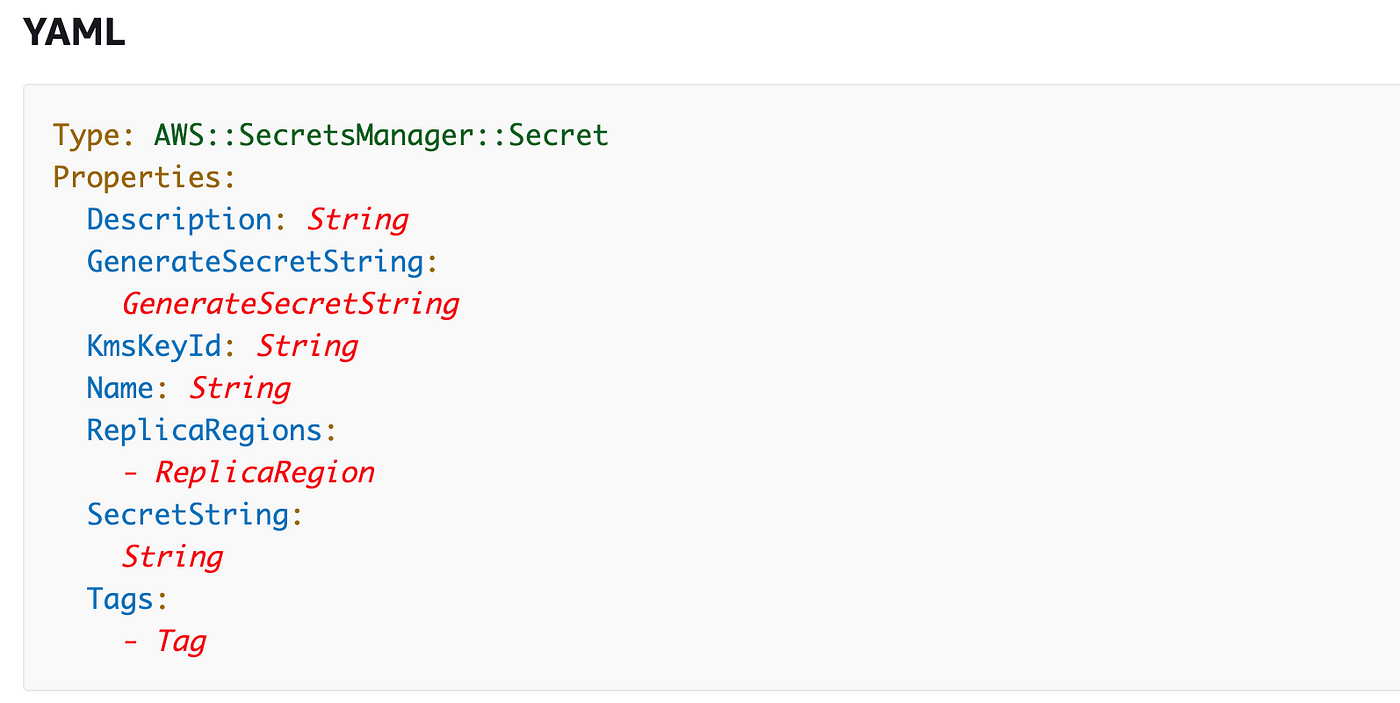
No fields are required however the documentation says:
Both
GenerateSecretStringorSecretStringshould have a worth, however not each.
We’ll use these fields: Description, Identify, KmsKeyId and SecretString.
We are able to go in key-value pairs for our secret as proven on this instance and we’ll use that format to go in our two secret values.
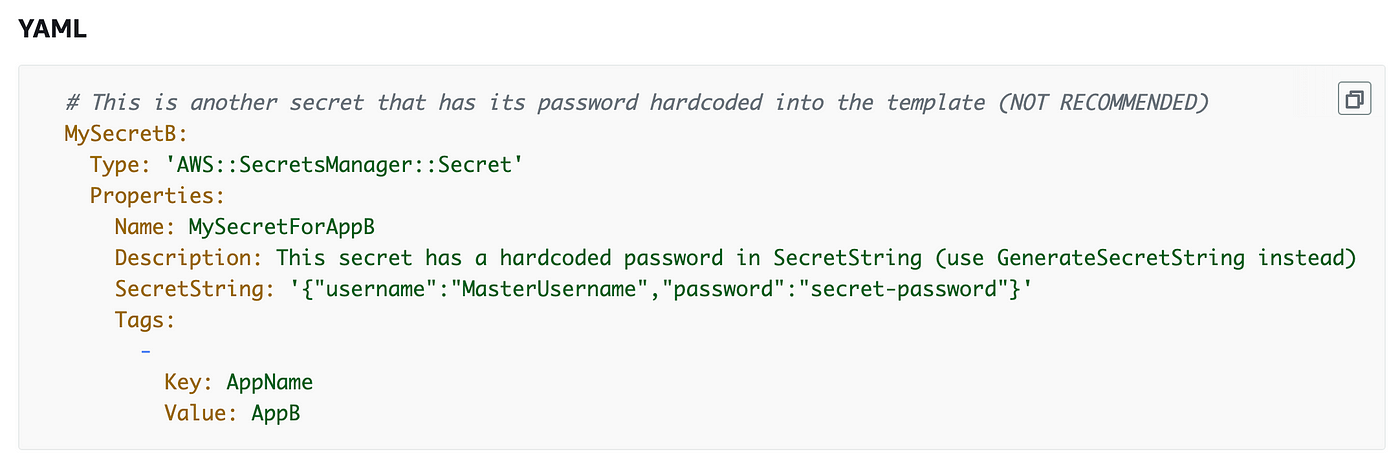
We’ll pull the KMSKeyId from the outputs of our key stack as we did once we examined the DescribeKey command above. So right here’s what our CloudFormation appears to be like like for our secret:
Now run the command with the right profile. As a substitute of letting the script use the default profile we’ll go in our new batch job profile:
./deploy.sh batch
Seems I obtained the next error:

For extra about what causes this error try this weblog publish.
I really feel like this can be a bug however for now we’ve so as to add each encrypt and decrypt permissions in the important thing coverage for our IAM person.
Different adjustments to the KMS key coverage
Notice that I needed to make another adjustments to the important thing coverage whereas figuring this all out I had another errors.
After eradicating the present person and root person as directors, I couldn’t view the important thing or the important thing coverage within the console with my present person.
Since I used to be logged in as an administrator, I added the foundation person to the DescribeKey assertion.
After doing that, I additionally want the GetKeyPolicy motion:

To disallow non-admins from viewing the coverage I created a separate assertion within the coverage for directors to view the important thing coverage.
Now our coverage permits admin customers to view however not modify keys by way of the KMS Key useful resource coverage.
Prior publish on IAM, Useful resource, and Belief insurance policies in case you are not acquainted:
Our coverage:
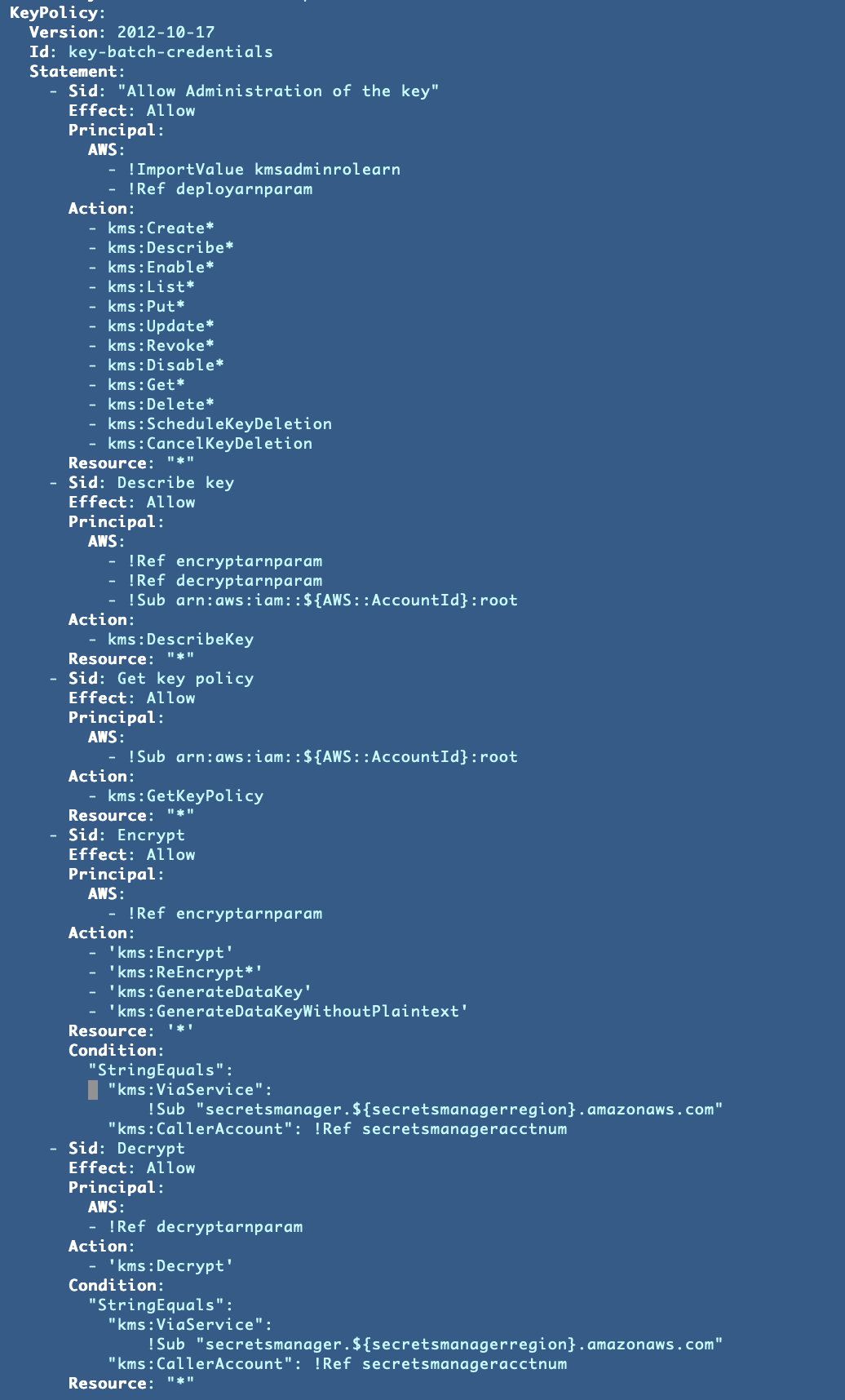
Notice that with these adjustments, the KMS person must create, replace and schedule keys for deletion. Nobody else will be capable of do this. I added a script to schedule key deletion into the kms folder which will be known as utilizing the kms AWS CLI profile we created in a previous publish:
Entry to KMS isn’t allowed
I had one different case of the KMS isn’t allowed error I needed to resolve.
After I take a look at the important thing coverage I see the next situation:
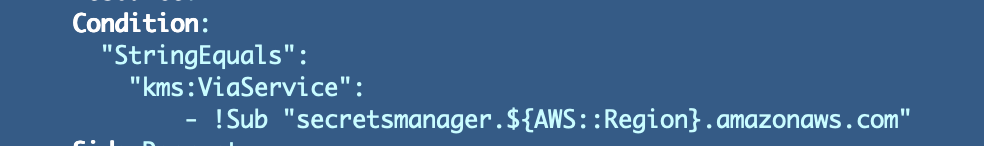
"Situation": {
"StringEquals": {
"kms:ViaService": "secretsmanager.${AWS::Area}.amazonaws.com",
"kms:CallerAccount": "${AWS::AccountId}"
}
}
I added that situation on this prior publish:
Oops. Our pseudo parameters didn’t resolve accurately. I used to be attempting to make use of them to set defaults for parameters however apparently that doesn’t work.
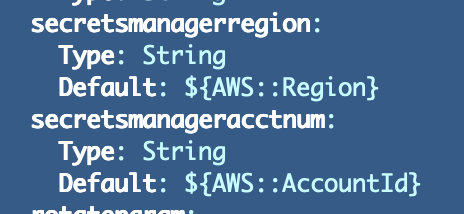
I made a decision to take away the Account ID as a result of we’ll be utilizing keys in a cross-account situation. If I wish to go in an account ID later I’ll add it again in.
I additionally moved the present area pseudo parameter as a substitute of passing within the area and we’ll assume for now that everybody in our accounts will use the present area the place the secret’s deployed. In an surroundings that requires failover to a distinct area or a cross-account situation you’ll want to check this to verify it really works.
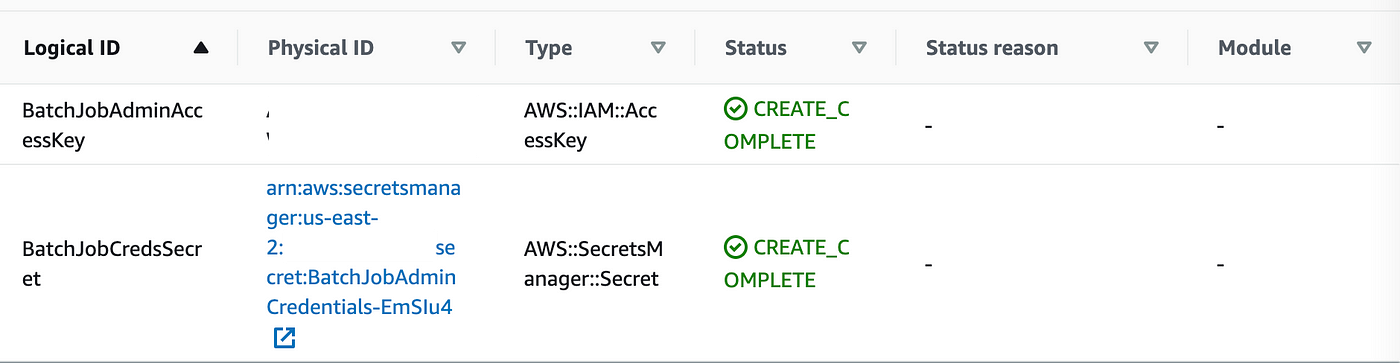
After fixing that downside, the CloudFormation deploys efficiently. The outputs present the sources which were deployed.
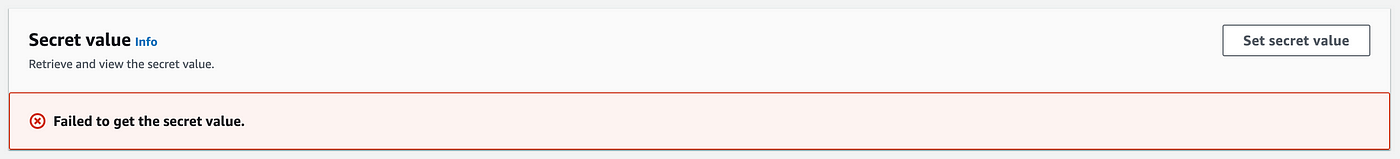
Trying to view the key as an admin fails, as anticipated, as a result of solely the function that triggers batch jobs can retrieve and examine the key.
We are able to attempt to flip this right into a batch job later, however it appears to be like like we’re going to have to make use of our KMS batch job function and person to deploy the KMS key and we’ll go away that till we finalize shifting administration of KMS keys to a separate account.
Now we have to revise our function to offer it solely the permissions it requires — or in different phrases, a zero belief IAM coverage. We’ll work on that subsequent.
Observe for updates.
Teri Radichel
Should you appreciated this story please clap and comply with:
Medium: Teri Radichel or E-mail Checklist: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests companies by way of LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this sequence:
____________________________________________
Writer:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration take a look at or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, displays, and podcasts


