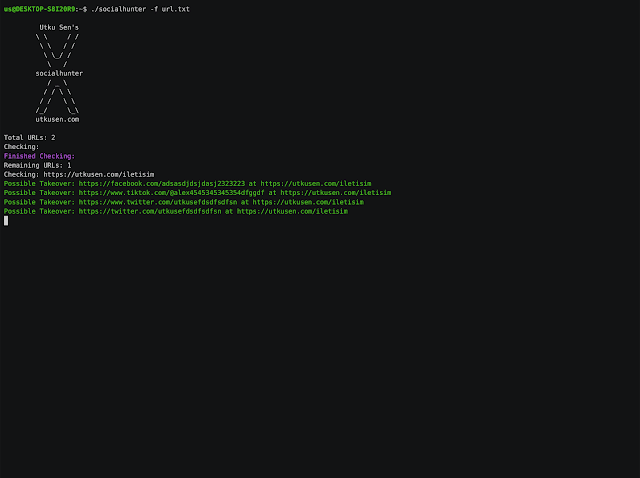
Crawls the given URL and finds damaged social media hyperlinks that may be hijacked. Damaged social hyperlinks could enable an attacker to conduct phishing assaults. It can also price a lack of the corporate’s repute. Damaged social media hijack points are often accepted on the bug bounty applications.
At the moment, it helps Twitter, Fb, Instagram and Tiktok with none API keys.
From Binary
You’ll be able to obtain the pre-built binaries from the releases web page and run. For instance:
wget https://github.com/utkusen/socialhunter/releases/obtain/v0.1.1/socialhunter_0.1.1_Linux_amd64.tar.gz
tar xzvf socialhunter_0.1.1_Linux_amd64.tar.gz
./socialhunter --help
From Supply
- Set up Go in your system
- Run:
go get -u github.com/utkusen/socialhunter
socialhunter requires 2 parameters to run:
-f : Path of the textual content file that accommodates URLs line by line. The crawl operate is path-aware. For instance, if the URL is https://utkusen.com/weblog, it solely crawls the pages beneath /weblog path
-w : The variety of employees to run (e.g -w 10). The default worth is 5. You’ll be able to improve or lower this by testing out the aptitude of your system.