 The most recent iteration in Copyright Declare scams is an evolution of this repeated assault methodology that has confirmed to get the eye – and response – of victims over the previous couple of years.
The most recent iteration in Copyright Declare scams is an evolution of this repeated assault methodology that has confirmed to get the eye – and response – of victims over the previous couple of years.
The rip-off itself is nothing new; I’ve coated it right here when it was concentrating on Instagram credentials, and earlier than that trying to put in the IceID information-stealing trojan. However in accordance with safety researchers at South Korean safety vendor AhnLab, it’s LockBit ransomware’s flip.
The assault begins with (in accordance with AhnLabs) a really similarly-written electronic mail in regards to the recipient being in violation of a copyright held by the sender, informing the recipient to take a look at the attachment for extra particulars on the violation.
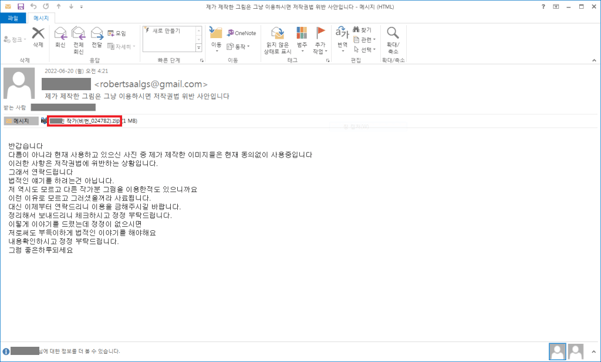
Supply: Ahn Labs
The assault does make a number of makes an attempt to obfuscate its’ malicious nature from safety options by attaching a zipper file that incorporates one other compressed file – an executable disguised as a PDF doc – that’s really an NSIS script file (Nullsoft Scriptable Set up System) which is an open-source Home windows installer.
There was no element included across the trade, dimension, or geography of the marketing campaign’s targets, however in accordance with Palo Alto’s Unit42, LockBit 2.0 traditionally targets skilled companies, building, wholesale and retail, and manufacturing firms.
And whereas AhnLab’s examples are in Korean, Unit42 notes that LockBit 2.0 has primarily targets the USA, Italy, Germany, Canada, France, the U.Ok., Spain, Thailand, Brazil and Switzerland.
Customers inside your group – notably these both in Advertising and marketing or Authorized (who would really care a couple of copyright declare) ought to be put by Safety Consciousness Coaching so they’re conscious of such scams, decreasing the probability of the assault succeeding.


