ACM.82 IAM Insurance policies to permit customers to explain their very own secrets and techniques
It is a continuation of my collection of posts on Automating Cybersecurity Metrics.
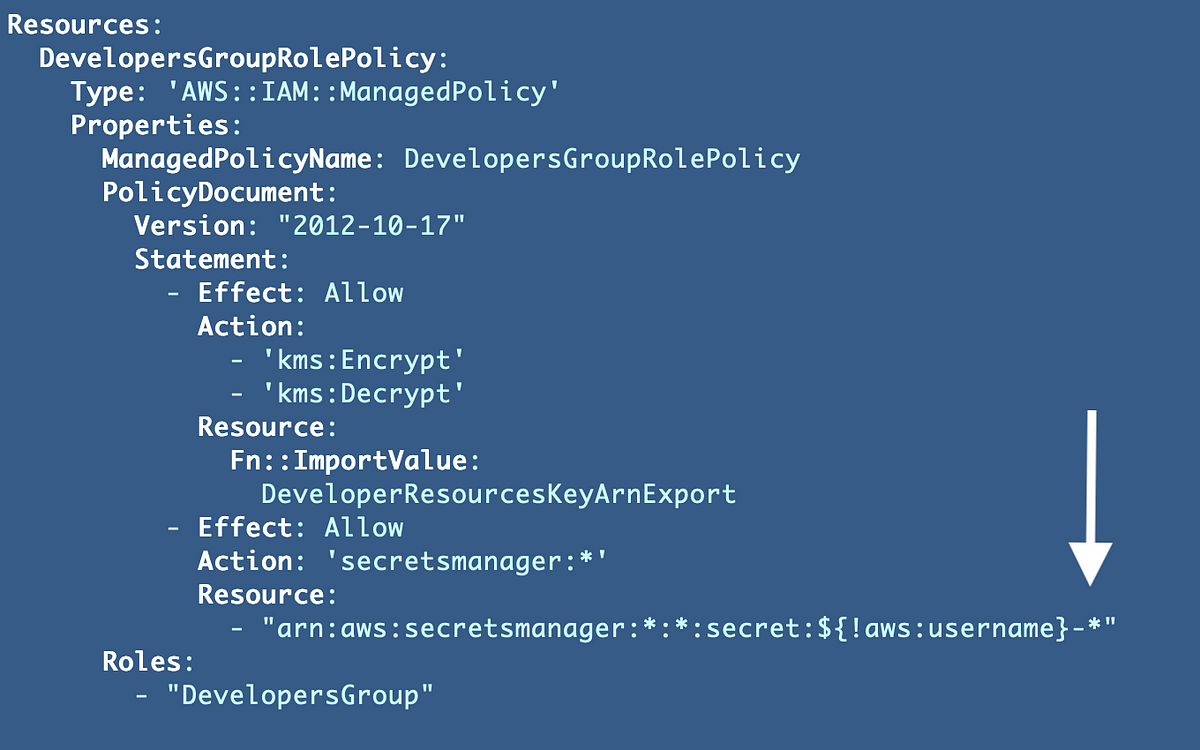
Within the final submit, we created an SSH key for a person programatically. I created a coverage for our Developer Group Function utilizing the ${aws:username} parameter which I hoped would prohibit every person to solely entry their very own secret.
Seems like we are able to’t view the key within the console. Extra on that later.
Drawback accessing a user-specific secret with a task
In case you recall, I’ve not given the Developer person console entry at this level. I’d tackle this later however for now let’s use the AWS CLI to see if the developer position can entry the key. I’ll have to arrange an AWS CLI profile for the developer position:
Now let’s see if we are able to get the key utilizing the AWS CLI and the developer profile. There’s one different factor we’ll want to repair. The describe-secret CLI command requires a secret ID which doesn’t precisely match our secret identify. Some additional characters received added on the finish.
We’ll want to regulate our Developer Group Function coverage:
That’s not an ideal resolution. Somebody may be capable of manipulate a person identify so as to add dashes to it and entry our secret. What if somebody may create a username “Developer-1” after which attempt to entry our secret? This coverage would grant them entry.
We even have one other drawback. Utilizing the AWS CLI with the assumed position, the identify of the person is not our Developer person. It’s the position identify: DevelopersGroup.
Recall that we gave the person identify entry to the key not the position or group as a result of we wish to implement non-repudiation. (See prior posts.)
Making use of the coverage to a bunch
What if we apply the coverage to a bunch as an alternative of the position? Would the coverage then apply to a person identify accurately? It would, however we nonetheless have the issue above. The key identify doesn’t match the developer identify. If we use a * within the coverage we’d find yourself with unintended penalties as defined above.
Making use of a user-specific coverage
What if we attempt to entry the key with an AWS CLI profile particular to the person as an alternative of the position?
DescribeSecret on useful resource: Developer-fnL9lq as a result of no identity-based coverage permits the secretsmanager:DescribeSecret motion
We haven’t granted any permissions on to the person particularly — we solely granted permission to imagine the DeveloperGroup position. We have to take away the permission from the position and apply them to the person as an alternative.
Typically it’s not observe to create user-specific insurance policies in AWS. Actually, I’d ding you for that on a safety evaluation in sure circumstances. Nonetheless, on this case, every particular person coverage is exclusive and the coverage ought to be deleted or deactivated with the person. The coverage may be very particular and for one objective. We’ve a single template to use the identical coverage to all customers, so if you must replace it, you replace it in as soon as place and redeploy it to all customers.
It could be rather a lot simpler if AWS would simply create the key with the identify we specified within the ARN (#awswishlist). That may additionally be sure that our secret names are distinctive we may merely reference the username within the template as an alternative of trying up the key identify and making a per-user coverage.
There are execs and cons to this method, however we are able to get a really particular coverage that provides a person solely entry to their very own secret. As a result of secret naming conventions I don’t see one other technique to do it as cleanly in the meanwhile with out including a harmful asterisk. Let’s attempt it.
If we have to deactivate or delete a person, we would want to take away the user-specific secret and SSH key, the identical method you’d delete a person identify and password or disable it. You may wish to create a service management coverage that forestalls deleting a person till their user-specific secret has been deleted or perhaps inactivated in some way so that you don’t have orphan secrets and techniques. I have to assume that via a bit extra.
Making a Per-Consumer Secret with CloudFormation
What if we create a person secret for a person with CloudFormation and cross our SSH key in as a parameter when creating the key?
The place would that parameter find yourself? Recall that parameters seem learn solely within the AWS console:
We will’t create a secret with no worth in any respect that we are able to replace later both. So we’d should cross one thing to our secret worth. We don’t wish to cross in any delicate knowledge as a result of it is going to find yourself within the AWS console in plain textual content for anybody with entry to learn.
Creating the key in CloudFormation assist us defend a secret we’re creating, however it permits us to get the key id as an output. However as you recall we are able to get that secret ID once we create it with a CLI command as effectively within the prior submit.
Which resolution works higher for us? Properly, we’ve got one other drawback we haven’t but addressed: If the key already exists, we are able to’t recreate it. If we use the CloudFormation deploy command that can deal with whether or not the key must be created or up to date. We may do this with our personal code, however why create extra work for ourselves? We’ll use CloudFormation to create the key.
Create a Secret With CloudFormation
We will change our script to create a secret with CloudFormation so it is going to create or replace the key as wanted. We’ll set a default worth for the key and overwrite it with the SSH key within the a later step.
Notice that as defined above, we are able to see that the parameter we used to set a default worth for our secret is seen in clear textual content within the AWS console. Don’t cross secret values in as parameters to AWS Secrets and techniques Supervisor.
Even when utilizing NoEcho…many warnings right here:
In case you test CloudTrail logs for the UpdateSecret entry, you’ll see that the key worth isn’t current. You’d simply want to think about the place it would exist on the system the place you’re making the API name.
Right here’s our up to date operate the place we:
- Test if the important thing already exists
- Create or replace the key
- Replace the key with the worth of the SSH key
- Replace the person coverage to permit the person to entry their very own secret
Right here’s the coverage that enables the person to get the worth of their very own secret.
Take away the permissions we tried so as to add to the Developer Function Coverage.
Now check to see if the developer can entry his or her personal secret:
aws secretsmanager describe-secret --secret-id Developer --profile developeruser
Sure!
There may be one different factor we are able to and doubtless ought to add to this coverage since it’s not a task and we wish to ensure that solely the proper developer can entry their very own secret. Are you aware what it’s?
Including an MFA situation to an IAM person coverage
We will add an MFA situation. I’ve written in regards to the MFA situation documentation earlier than right here:
I feel we are able to simply test if MFA is current with out the ifexists however let’s do this out:
Situation:
"Bool":
"aws:MultiFactorAuthPresent" : "True"
That deploys, now let’s see if we are able to nonetheless entry our secret. No:
An error occurred (AccessDeniedException) when calling the DescribeSecret operation: Consumer: arn:aws:iam::xxxx:person/Developer isn't licensed to carry out: secretsmanager:DescribeSecret on useful resource: Developer as a result of no identity-based coverage permits the secretsmanager:DescribeSecret motion
As soon as once more, this error message is deceptive. I want it might specify that the situation isn’t met. In any case, let’s go see what the request appears like in CloudTrail.
To seek out the motion that precipitated the error I needed to search by UserName.
For some motive I didn’t discover it once I searched by AWS Secrets and techniques Supervisor Secret because the useful resource.
I may additionally discover it by looking for DescribeSecret:
Properly, would you have a look at that. There’s no MFA worth in any respect on this request, though I’ve configured my person within the CLI to make use of MFA:
So that is the place the “long run credentials” come into play together with your MFA situations that I wrote about within the prior submit. Apparently there is no such thing as a technique to implement MFA for this motion for a single person utilizing programmatic credential or they will be unable to programmatically get to the key.
If we take away MFA, then if a Developer has credentials hard-coded on their native laptop computer then somebody may use them with out MFA to get to this user-specific secret programmatically. That’s fairly unlucky.
What if we take away the MFA situation? We will as soon as once more entry our secret, and curiously sufficient, now the Useful resource Kind accurately exhibits an AWS::SecretsManager:Secret
Maintain the above in thoughts if you’re attempting to put in writing alerts associated to failure to entry a Secrets and techniques Supervisor Secret and also you’re looking out on Useful resource sort — at all times check your alerts with precise values.
OK let’s say we add “if exists” to our coverage as really helpful within the AWS documentation. Does that really assist us? As I’ve written about earlier than — no. On this case, MFA doesn’t exist when somebody is utilizing long run credentials. So if we had been so as to add if exists our situation merely wouldn’t be enforced when the situation doesn’t exist, because it doesn’t within the above state of affairs. I really feel that the AWS documentation isn’t precisely clear on this level and it makes it appear to be the “if exists” possibility is OK when it’s actually not should you really wish to implement MFA.
We’ll have a look at among the different actions the person took and see if the MFA authentication exhibits up wherever else in a later submit. For now, I eliminated the MFA requirement till we are able to check different actions.
Observe for updates.
Teri Radichel
In case you favored this story please clap and observe:
Medium: Teri Radichel or E-mail Listing: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests providers through LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this collection:
____________________________________________
Writer:
Cybersecurity for Executives within the Age of Cloud on Amazon
Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, shows, and podcasts