Researchers from Wordfence have sounded the alarm a couple of “sudden” spike in cyber assaults trying to take advantage of an unpatched flaw in a WordPress plugin known as Kaswara Trendy WPBakery Web page Builder Addons.
Tracked as CVE-2021-24284, the difficulty is rated 10.0 on the CVSS vulnerability scoring system and pertains to an unauthenticated arbitrary file add that might be abused to achieve code execution, allowing attackers to grab management of affected WordPress websites.
Though the bug was initially disclosed in April 2021 by the WordPress safety firm, it continues to stay unresolved to this point. To make issues worse, the plugin has been closed and is now not actively maintained.
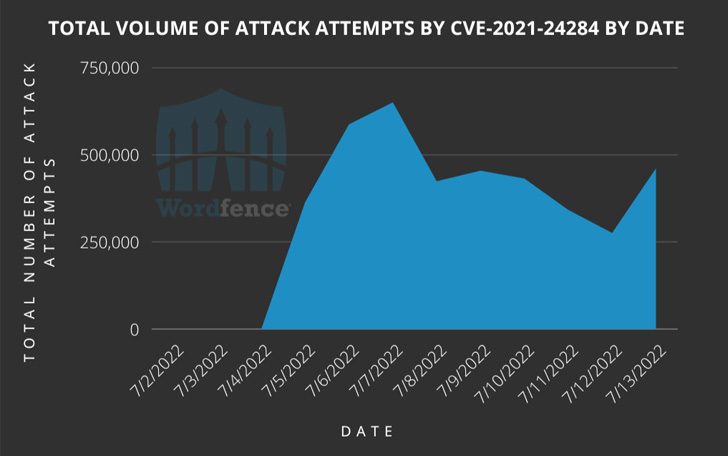
Wordfence, which is defending over 1,000 web sites which have the plugin put in, mentioned it has blocked a mean of 443,868 assault makes an attempt per day for the reason that begin of the month.
The assaults have emanated from 10,215 IP addresses, with a majority of the exploitation makes an attempt narrowed all the way down to 10 IP addresses. These contain importing a ZIP archive containing a malicious PHP file that enables the attacker to add rogue information to the contaminated web site.
The purpose of the marketing campaign, it seems, is to insert code into in any other case reliable JavaScript information and redirect website guests to malicious web sites. It is price noting that the assaults have been tracked by Avast and Sucuri underneath the monikers Parrot TDS and NDSW, respectively.
Between 4,000 and eight,000 web sites are mentioned to have the plugin put in, making it crucial that customers take away it from their WordPress websites to thwart potential assaults and discover an applicable various.