The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software program or and intrusion detection system (IDS). A zero-day exploit is able to skating proper previous these defenses as they don’t include a signature or one other approach of detecting them.
Creating a zero-day could be tedious and time-consuming and isn’t for the novice. It often entails discovering a buffer that may be overflowed, then writing the code that overflows the buffer, and taking management of the execution in order that your malicious software program is run. Not a easy activity.
An alternate, in fact, is to seize a zero-day exploit. Prison hackers and nationwide governments are all the time creating new zero-day exploits so as steal bank card numbers, confidential info, or nationwide secrets and techniques. If we will persuade these entities that our system is each essential and weak, they are going to possible assault it as nicely. Once they do, we could possibly seize their exploit and reuse it. A few of these exploits are price thousands and thousands of {dollars}.
Within the first a part of this collection, we downloaded and arrange the Dionaea honeypot. What makes Dionaea totally different than different honeypots is its means to seize exploits. We had arrange the honeypot within the final information, however we had but to configure it. On this tutorial, we are going to configure Dionaea to arrange it for capturing exploits. I started this collection organising Dionaea on an Ubuntu 14.04 desktop system, so we are going to proceed to make use of Dionaea on Ubuntu—however Dionaea will run on many Linux distributions.
Step 1: Open the Dionaea Configuration File
Step one is to open the Dionaea configuration file. First navigate to the/and so forth/dionaea listing.
ubuntu > cd /and so forth/dionaea
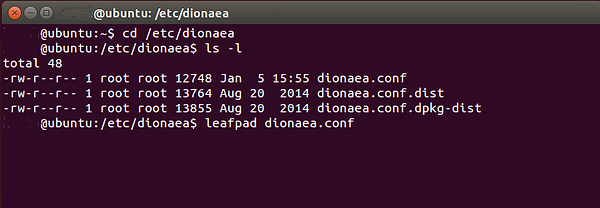
Once you do a protracted itemizing on that listing, you possibly can see the dionaea.conf file. Let’s open that file with a textual content editor. On Ubuntu, we have now a number of decisions. On this case, I used Leafpad, however gedit, Vim, or another textual content editor will work.
ubuntu > leafpad dionaea.conf
Step 2: Configure Logging
In its default configuration, Dionaea will create shiploads of logs in a manufacturing setting. In some instances, you will notice a number of gigabytes per day of log recordsdata. To stop that, we have to configure logging to solely log “error” priorities and above degree. (For extra info on Linux logging, see my Linux Fundamentals article on the subject or my new e book “Linux Fundamentals for Hackers” out there on Amazon).
To take action, we have to navigate right down to the logging part of the configuration file. There you will notice a bit that appears like this:
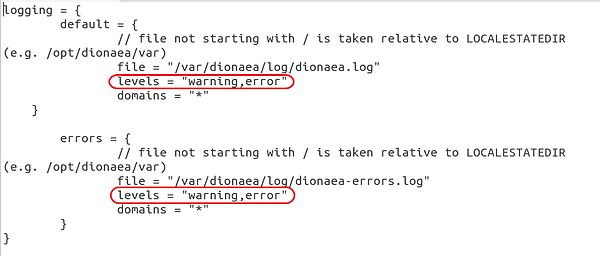
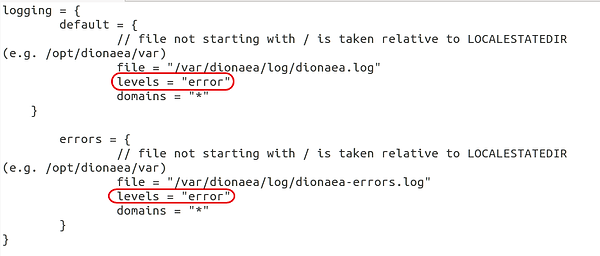
Notice the 2 areas I’ve circled. Change each of them from “warning,error” to simply “error”.
Step 3: Interface and IP Part
Subsequent, navigate right down to the pay attention and interface part of the configuration file. We wish the interface to be set to “handbook” and the IP addresses set to any. It will enable Dionaea to seize on the interface of your selection (eth0) it doesn’t matter what IP tackle is assigned to it.
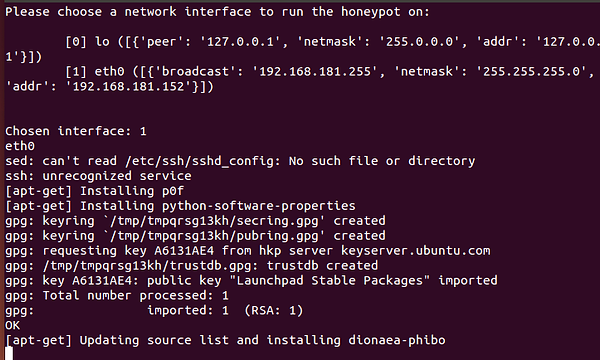
In order for you Dionaea to solely pay attention on a single IP tackle, you possibly can place that IP tackle within the line beneath, changing the “::” half.
addrs = {eth0 = “::”}
As you recognize, “::” is IPv6 shorthand for any IP tackle.
Step 4: Modules
Subsequent, we have to inform Dionaea what modules we would like it to run.
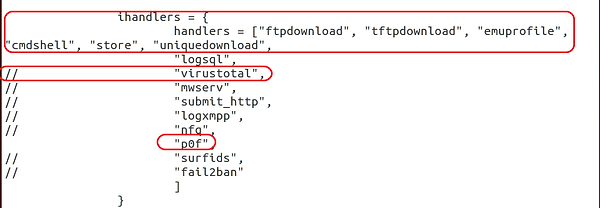
Go away the default setting right here, however be aware that we have now “virustotal” commented out. If the feedback are eliminated, you possibly can configure Dionaea to ship any captured malware to VirusTotal. Let’s hold it commented out.
Additionally be aware that we are going to be utilizing one in every of our favourite instruments, p0f, for the working system fingerprinting. Lastly, we have now “logsql” uncommented, enabling Dionaea to create and use an SQLite database. It will improve our means to handle the exercise from our sensor by putting the information right into a SQLite database.
Step 5: Companies
Slightly below the modules, we have now a bit detailing the companies we need to run. Notice beneath that Dionaea by default is ready as much as run http, https, tftp, ftp, mirror, smb, epmap, sip, mssql, and mysql.
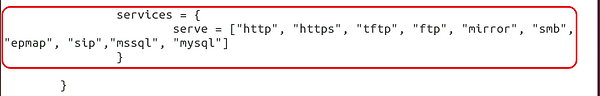
I like to recommend that you just disable http and https as they don’t seem to be prone to idiot many attackers and should, the truth is, establish it as a honeypot. Go away the others as they signify weak companies that could be attacked.
Step 6: Begin Dionaea to Check
Lastly, to check our new configuration we have to run Dionaea. We will do that by typing:
ubuntu> dionaea -u no one -g nogroup -w /decide/dionaea -p /decide/dionaea/run/dionaea.pid
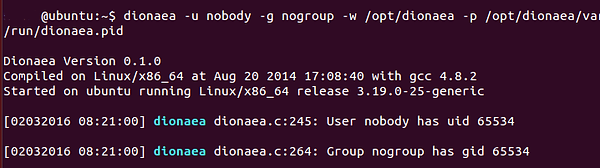
Now that Dionaea is working efficiently, we will go to the subsequent step, capturing and analyzing malware with Dionaea.


