Welcome again, my aspiring RF hackers!
Among the many multitude of radio indicators swirling round us on a regular basis are the cellular phone indicators that each one of us have grow to be so dependent upon. Cellular networks use a number of completely different applied sciences together with GSM, CDMA, TDMA, 4G, LTE, 5G and plenty of others.
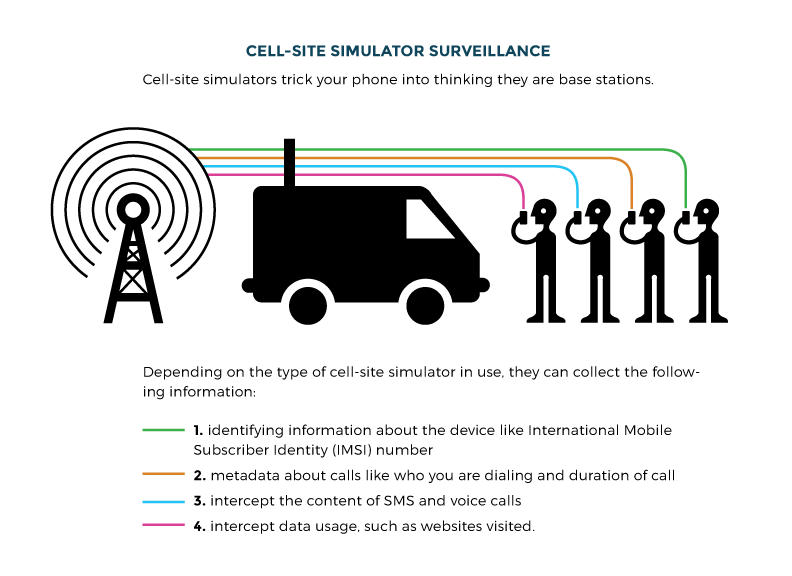
For nearly twenty years now, legislation enforcement around the globe have been utilizing IMSI catchers (aka Stingrays) to eavesdrop and monitor suspects. These IMSI catchers act as moveable mobile towers and sniff the mobile visitors, establish the IMSI, monitor the IMSI geographically, intercept and skim metadata/Web visitors, and listen in on voice conversations.

Commercially out there IMSI catchers go by the identify “Stingray”and others. These stingrays are presupposed to be solely out there to legislation enforcement however they’ve made their manner into the arms of others. Many have complained in regards to the civil liberties features of permitting legislation enforcement and oppressive governments utilizing these units to trace and hearken to targets however this has not stopped their use. The Digital Frontier Basis has known as the units “an unconstitutional, all-you-can-eat knowledge buffet.”
Usually, these units are estimated to price between $50,00-$200,000 from electronics firms reminiscent of Harris. It’s my speculation that if the fee had been to drop to about $2000 and be out there to anybody with a little bit of technical information, they might be rapidly outlawed. That’s our aim on this collection; develop a low-cost Stingray.
Technically, a Stingray can be a IMSI catcher with a mobile base station. In our tutorial right here, we’ll implement the primary stage of the mobile man-in-the-middle assault; the seize of the IMSI. Right here we’ll solely be capable to seize the IMSI of 2G and 3G cellphones. That will appear limiting if you’re within the US or Western Europe, however current knowledge signifies about 46% of present telephones around the globe are utilizing these two older applied sciences. In future tutorials, we’ll work on 4G, LTE and 5G applied sciences.
As soon as we have now are capable of seize the IMSI, we have now begun the method of constructing our Stingray. The subsequent step is constructing a mobile base station. Mobile base stations are prohibitively costly however an opensource challenge known as OpenBTS has developed a base station for lower than $1000.
GSM Networks and IMSI numbers
GSM is commonplace developed by the European Telecommunications Requirements Institute (ETSI) and first deployed in Finland (residence of Nokia and Linus Torvalds) in December 1991. It quickly turned the European commonplace for mobile phone transmission and achieved 90% penetration of the worldwide cellular community by the twenty first century.
One of many safety vulnerabilities of GSM networks is the shortage of mutual authentication. The GSM handset doesn’t authenticate the bottom station previous to accessing the community. On this tutorial, we’ll use this safety vulnerability to smell and purchase the handset’s IMSI.

The IMSI quantity is a globally distinctive quantity that identifies the consumer. It’s as much as 15 digits and contains;
MCC – Cellular Nation Code. 3 decimals locations and identifies the nation of the cellular machine proprietor
MNC – Cellular Community Code. 2 decimal locations and identifies the service community
MSIN – Cellular Subscriber Quantity 10 decimal locations and identifies the subscriber

The IMSI quantity is held inside the SIM card within the cell phone and identifies the nation, the service, and the consumer. With this info, the individual sniffing this visitors can establish and find the telephone consumer at a minimal and doubtlessly intercept and spoof the consumer’s visitors.
Let’s have a look at how we are able to harvest that info from 2G and 3G cellular networks with our RTL-SDR dongle and some items of software program.
Step #1: Set up New Software program in Kali
For this tutorial, we might be utilizing Kali and several other new items of software program. Let’s start with gr-gsm. Gr-gsm is a set of instruments for receiving GSM transmissions, which works with any software program radio (SDR) {hardware} able to receiving a GSM sign.
Though gr-gsm is out there within the Kali repository, I discovered that constructing it from the supply code works higher. To put in gr-gsm, first set up the dependencies;
kali > sudo apt-get set up -y cmake autoconf libtool pkg-config build-essential python-docutils libcppunit-dev swig doxygen liblog4cpp5-dev gnuradio-dev
gr-osmosdr libosmocore-dev liborc-0.4-dev swig
Then, clone gr-gsm from the github repository.
kali > sudo git clone https://git.osmocom.org/gr-gsm

Then comply with the subsequent few steps to construct the applying.
cd gr-gsm
mkdir construct
cd construct
cmake ..
make -j 4
sudo make set up
sudo ldconfig
Lastly, we’d like change the PYTHONPATH surroundings variable
kali > sudo echo ‘export PYTHONPATH=/usr/native/lib/python3/dist-packages/:$PYTHONPATH’ >> ~/.bashrc
Now you might be prepared to put in kalibrate-rtl from the Kali repository.
kali > sudo apt set up kalibrate-rtl

Subsequent, clone the IMSI-catcher from github.

Step #2: Discover the Frequencies the Base Stations are Working on
The subsequent step is to seek out the bottom stations in your space and the frequency they’re working on. For this motion, we are able to use kalibrate.
Let’s start by inspecting the kalibrate assist display screen.
kali > kal -h

As you may see above, kal merely wants -s to scan adopted by the expertise reminiscent of GSM850, GSM-R, GSM900, EGSM, DCS or PCS. As well as, we are able to specify the achieve with the-g choice. Since GSM850 is frequent in North and South America, I am going to scan for it with a achieve of 45db.
kali > sudo kal -s GSM850 -g 45

As you may see above, there have been 2 base stations inside vary at 889.0Mhz and 890.0Mhz. These fall inside the receiving vary of my RTL-SDR dongle (24-1766Mhz).
Step #3: Tune grgsm to the Base Station Frequency
Now we have to flip the grgsm to the frequency of the close by base station. Navigate to the gr-gsm listing and enter;
kali > grgsm_livemon -f 889.0M -g 45

This could open the gr-gsm GUI. In case you want, you may alter the frequency with the slide bar.
The place 889.0M is the frequency we need to “pay attention” on (make sure to substitute the frequency discovered at your locale with kalibrate) and -g 45 is the achieve charge.

Step #4: Begin IMSI Catcher
Lastly, let’s begin the IMSI catcher.
Navigate to the IMSI-catcher listing after which execute the catcher with the -s choice (scan).
kali > cd IMSI-catcher
kali > sudo python simple_IMSI-catcher.py -s

As I dwell in a distant location within the Rocky Mountains of the US the place few individuals are nonetheless utilizing 2G and 3G GSM telephones, my IMSI-catcher doesn’t choose up any IMSI’s. As well as, our hardware–the cheap rtl-sdr– is restricted to 1766Mhz within the higher vary and several other GSM telephone applied sciences function outdoors that band at larger frequencies.
Then again, one other consumer in Europe the place GSM is the usual and nonetheless has many 2G and 3G telephones, captured quite a few IMSI’s together with operator and cell ID as seen beneath.

Abstract
Even with a reasonable RTL-SDR, we are able to choose up and sniff 2G and 3G mobile visitors full with the IMSI. For the reason that IMSI is embedded within the SD card, there may be little likelihood of spoofing the IMSI with out costlier gear. Then again, IMSI’s are collected by a variety of cellular purposes and these IMSI’s can be utilized to correlate with that knowledge to establish the consumer. After all, legislation enforcement can get a subpoena for the consumer’s IMSI and establish the consumer with this knowledge.
As we progress by way of this collection, we might be including extra refined software program and {hardware} as we develop a reasonable Stingray for intercepting cellular communications.