ConnectWise, a self-hosted, distant desktop software program software that’s broadly utilized by Managed Service Suppliers (MSPs), is warning about an unusually refined phishing assault that may let attackers take distant management over person methods when recipients click on the included hyperlink. The warning comes simply weeks after the corporate quietly patched a vulnerability that makes it simpler for phishers to launch these assaults.

A phishing assault focusing on MSP prospects utilizing ConnectWise.
ConnectWise’s service is extraordinarily in style amongst MSPs that handle, defend and repair massive numbers of computer systems remotely for shopper organizations. Their product gives a dynamic software program shopper and hosted server that connects two or extra computer systems collectively, and gives short-term or persistent distant entry to these shopper methods.
When a assist technician desires to make use of ConnectWise to remotely administer a pc, the ConnectWise web site generates an executable file that’s digitally signed by ConnectWise and downloadable by the shopper by way of a hyperlink.
When the distant person in want of help clicks the hyperlink, their pc is then immediately related to the pc of the distant administrator, who can then management the shopper’s pc as in the event that they had been seated in entrance of it.
Whereas fashionable Microsoft Home windows working methods by default will ask customers whether or not they need to run a downloaded executable file, many methods arrange for distant administration by MSPs disable that person account management function for this explicit software.
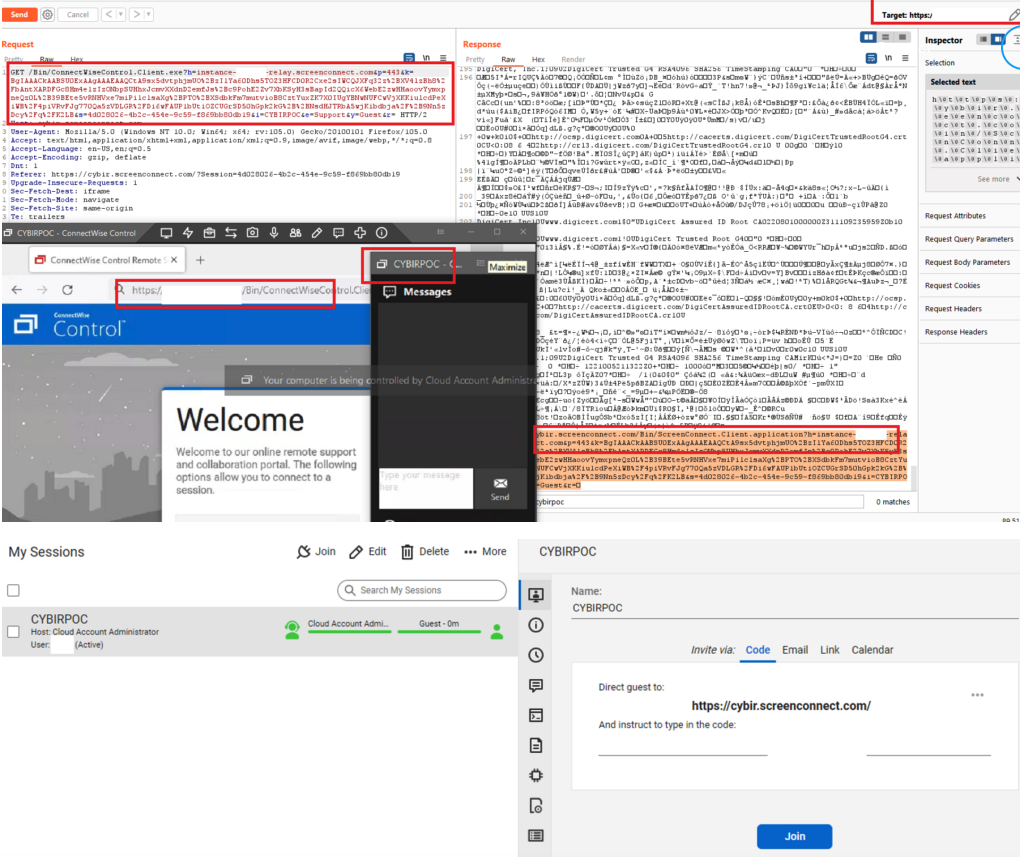
In October, safety researcher Ken Pyle alerted ConnectWise that their shopper executable file will get generated primarily based on client-controlled parameters. That means, an attacker may craft a ConnectWise shopper obtain hyperlink that might bounce or proxy the distant connection from the MSP’s servers to a server that the attacker controls.
That is harmful as a result of many organizations that depend on MSPs to handle their computer systems typically arrange their networks in order that solely distant help connections coming from their MSP’s networks are allowed.
Utilizing a free ConnectWise trial account, Pyle confirmed the corporate how straightforward it was to create a shopper executable that’s cryptographically signed by ConnectWise and might bypass these community restrictions by bouncing the connection by means of an attacker’s ConnectWise management server.
“You because the attacker have full management over the hyperlink’s parameters, and that hyperlink will get injected into an executable file that’s downloaded by the shopper by means of an unauthenticated Net interface,” mentioned Pyle, a accomplice and exploit developer on the safety agency Cybir. “I can ship this hyperlink to a sufferer, they may click on this hyperlink, and their workstation will join again to my occasion by way of a hyperlink in your web site.”
A composite of screenshots researcher Ken Pyle put collectively for instance the ScreenConnect vulnerability.
On Nov. 29, roughly the identical time Pyle printed a weblog put up about his findings, ConnectWise issued an advisory warning customers to be on guard in opposition to a brand new spherical electronic mail phishing makes an attempt that mimic official electronic mail alerts the corporate sends when it detects uncommon exercise on a buyer account.
“We’re conscious of a phishing marketing campaign that mimics ConnectWise Management New Login Alert emails and has the potential to result in unauthorized entry to official Management cases,” the corporate mentioned.
ConnectWise mentioned it launched software program updates final month that included new protections in opposition to the misdirection vulnerability that Pyle reported. However the firm mentioned there is no such thing as a motive to imagine the phishers they warned about are exploiting any of the problems reported by Pyle.
“Our crew rapidly triaged the report and decided the chance to companions to be minimal,” ConnectWise spokesperson Tarran Avenue mentioned. “However, the mitigation was easy and offered no danger to accomplice expertise, so we put it into the then-stable 22.8 construct and the then-canary 22.9 construct, which had been launched as a part of our regular launch processes. Because of the low severity of the problem, we didn’t (and don’t plan to) concern a safety advisory or alert, since we reserve these notifications for critical safety points.”
Pyle mentioned he doubts the problem he reported is unrelated to the phishing assaults ConnectWise is warning about.
“They don’t need to speak about my work (no advisory), and so they suggest making use of the patch they issued in response to my work,” Pyle wrote when requested to touch upon ConnectWise’s response.
The ConnectWise advisory warned customers that earlier than clicking any hyperlink that seems to come back from their service, customers ought to validate the content material contains “domains owned by trusted sources,” and “hyperlinks to go to locations you acknowledge.”
However Pyle mentioned this recommendation shouldn’t be terribly helpful for purchasers, as a result of in his assault state of affairs the phishers can ship emails immediately from ConnectWise, and the quick hyperlink that will get offered to the person is a wildcard area that ends in ConnectWise’s personal area identify — screenconnect.com. What’s extra, inspecting the exceedingly lengthy hyperlink generated by ConnectWise’s methods presents few insights to the typical person.
“It’s signed by ConnectWise and comes from them, and for those who join a free trial occasion, you’ll be able to electronic mail folks invitations immediately from them,” Pyle mentioned.
ConnectWise’s warnings come amid breach reviews from one other main supplier of cloud-based distant assist applied sciences: GoTo disclosed on Nov. 30 that it’s investigating a safety incident involving “uncommon exercise inside our growth setting and third-party cloud storage companies. The third-party cloud storage service is at the moment shared by each GoTo and its affiliate, the password supervisor service LastPass.
In its personal advisory on the incident, LastPass mentioned they imagine the intruders leveraged info stolen throughout a earlier intrusion in August 2022 to achieve entry to “sure parts of our prospects’ info.” Nevertheless, LastPass maintains that its “buyer passwords stay safely encrypted attributable to LastPass’s Zero Information structure.”
In brief, that structure means for those who lose or overlook your all-important grasp LastPass password — the one wanted to unlock entry to all your different passwords saved with them — LastPass can’t enable you with that, as a result of they don’t retailer it. However that very same structure theoretically signifies that hackers who would possibly break into LastPass’s networks can’t entry that info both.

