ACM.31: Contemplating how an attacker may abuse function templates
This can be a continuation of my collection on Automating Cybersecurity Metrics.
Earlier than we go any additional on this collection we wish to try a possible menace when utilizing our roles, and particularly cross-account or service roles. This safety drawback is called the Confused Deputy in AWS terminology.

This assault is consists of an exterior attacker is ready to leverage the permissions offered by a job externally to entry your account.
How does a confused deputy assault work?
This assault jogs my memory of the subdomain takeover assault I spoke about at RSA 2020. Yow will discover that and different shows I’ve given prior to now right here. In that state of affairs, an attacker leverages a subdomain you personal to realize entry to providers you could have utilized in that previous with that subdomain. They might additionally discover one other method to leverage your subdomain with out your permission.
There are two flavors of this confused deputy drawback: Cross-account and Cross-service.
Cross-Account Confused Deputy Assaults
On this case, an attacker is utilizing a job in your account from one other account. They one way or the other obtained the title of the function and so they can use it in locations the place a job is required to combine with a third-party system to acquire entry to your information.
For instance, I checked out a service that may leverage a job to run queries in your account remotely and show misconfigurations of their portal. What if an attacker may determine what function you gave that firm? If the seller isn’t monitoring for the duplicate use of roles of their system and never validating that prospects truly personal the accounts the place the function exists, an attacker may register their very own account on the vendor, present your AWS function to the seller, and think about all of the misconfigurations in your AWS account in their very own account on the third-party service.
To fight this drawback AWS recommends making use of a exterior ID.
Don’t use any delicate information in an exterior ID:

Will probably be seen in your AWS insurance policies to anybody who can view them.
The Exterior ID needs to be a random string generated by the third-party to whom you might be giving entry. Once you create a job you add two circumstances:

Meaning the opposite account can not take an motion until the exterior ID is configured on their aspect. As a way to grant entry to leverage the function, the client of the seller has so as to add their distinctive exterior ID to the function coverage.
How does this assist precisely? Let’s take the state of affairs of our attacker once more. The attacker tries to arrange an account with the seller to entry your account with a job they’ve one way or the other guessed or acquired. After they register their account with the seller, the seller gives them a novel exterior ID. The exterior ID that the seller gives to the attacker is not going to match the exterior ID they gave you. The attacker won’t be able to make use of your function ARN of their vendor account, as a result of the exterior IDs don’t match. They don’t know what exterior ID to make use of of their function configuration.
We’re not utilizing any third-party providers in the mean time however I may use my providers on buyer tasks. I do use exterior IDs once I work with prospects on penetration assessments in addition to MFA as I wrote about in a previous put up:
As well as, I ask prospects to disable roles and credentials as quickly as an engagement is over.
Cross-Service Confused Deputy Assaults with Useful resource Insurance policies
The opposite state of affairs AWS mentions is cross-service impersonation, which is particularly talked about with regard to AWS Lambda Step Features:
In AWS, cross-service impersonation can happen when one service (the calling service) calls one other service (the referred to as service). The calling service may be manipulated to make use of its permissions to behave on one other buyer’s assets in a manner it shouldn’t in any other case have permission to entry.
To resolve this AWS recommends the next:
We suggest utilizing the
aws:SourceArnandaws:SourceAccountinternational situation context keys in resource-based insurance policies to restrict the permissions {that a} service has to a particular useful resource. Useaws:SourceArnif you need just one useful resource to be related to the cross-service entry. Useaws:SourceAccountif you wish to enable any useful resource in that account to be related to the cross-service use.
May somebody entry our assets utilizing this assault that we’ve created to this point? It appears like we may add some extra safety to our useful resource insurance policies. We’ll contemplate that in an upcoming put up. For now I’m extra involved concerning the subsequent potential assault.
Confused deputy drawback and STS function assumption (belief insurance policies)
May an attacker use one of many roles I’ve constructed to this point to hold out this kind assault or some associated assault the place they’ll use our roles? Effectively, I’m not utilizing any third-party service to this point or utilizing any exterior roles. However what else may result in role-takeover or abuse?
We’ve particularly restricted assumption of the IAM and KMS admins to particular customers and required MFA. Until the attacker has the credentials for that particular person and authenticates with MFA, they shouldn’t be in a position to assume these roles as they’re particularly locked all the way down to a single person.
What about our batch job function?
The one factor I did simply do was present you methods to create a job the place somebody may cross in an ARN to imagine that function in a CloudFormation template. What would possibly somebody be capable to do with this template? Anybody who can run this CloudFormation template for a batch job may cross in any ARN to imagine the function they create. They may even be capable to assume any of the batch job roles that begin with the title “BatchRole.”
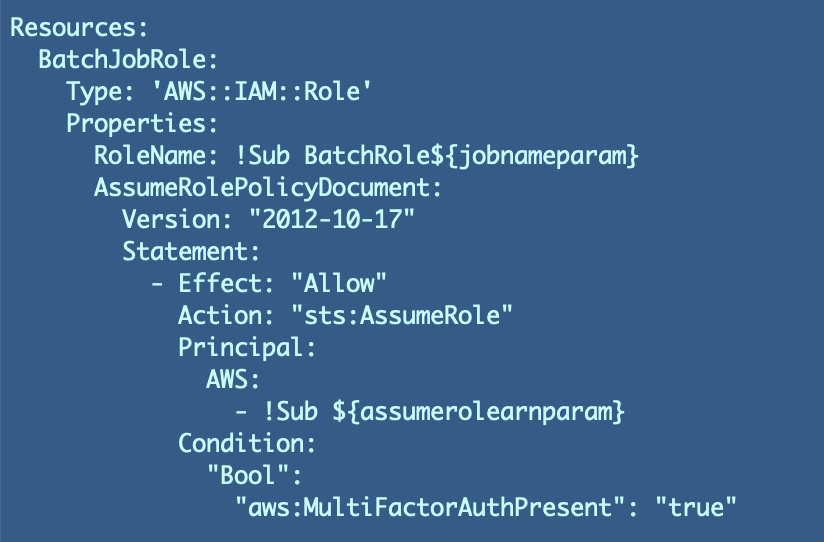
What have we performed to stop somebody from abusing this performance? Up to now now we have solely required MFA. Anybody who’s logged in with MFA may doubtlessly run the CloudFormation script and cross in their very own ARN to imagine any batch job function.
As soon as somebody has assumed batch job function they’ll do something that batch job can do. Up to now on this collection that features creating a brand new set of credentials for our Batch Job administrator, so considerably restricted, however the objective of our batch jobs is to carry out any variety of features. How may we additional lock this down?
Fixing the issue through the use of hard-coded templates
One factor could be to revert to utilizing a separate function template for every sort of batch job and person and hard-coding the ARN within the template once more. We may onerous code within the potential for the IAM person to imagine IAM batch job roles. We may onerous code a separate function template to permit the Batch Job person to imagine the common batch job roles.
That may in all probability be the best strategy however requires duplicating code. What’s the issue with duplicated code? I defined that on this weblog put up:
Along with hard-coding the templates you want to clearly ensure that an attacker or malicious insider can not edit the templates.
I would favor to not take this strategy if I can consider a greater answer.
Can we repair the issue with an exterior ID?
What if we require an exterior ID. Effectively, take my case. I’m an administrator working this template however let’s say I can’t change the code. After I run this template I’ve to cross in an exterior ID offered by somebody to cross into the script. There’s nothing from stopping me from altering the ARN and it’ll nonetheless work as a result of somebody has to present me the exterior ID so I can run the script.
What if we put the exterior ID in a secret? Effectively, the CloudFormation template might want to retrieve the key proper? I, as an administrator working the template, can nonetheless put in no matter ARN I would like and the CloudFormation template will nonetheless execute. Nonetheless, what occurs when I attempt to go use the function? I might want to cross within the exterior ID:If can’t see or know that exterior ID then I received’t be capable to put the exterior ID in my configuration and assume the function.
The caveat with that answer is that the exterior ID should not be current wherever within the CloudFormation outputs or metadata. If I, as administrator, have permission to edit the CloudFormation template, I may attempt to get the worth of the key and show it within the CloudFormation outputs. If I solely have permission to execute however not change the CloudFormation template, I received’t be capable to try this.
The opposite caveat with this answer is that if I’ve permission to view the assume function coverage after it’s deployed, then I can get the exterior ID from there. If we use this selection the individual deploying the template:
- Can’t have entry to alter the CloudFormation template.
- Can’t have visibility into anyplace the exterior ID is output.
If this can be a individual answerable for sustaining cloud deployments, then possible they want to have the ability to view the assets created when the deployments execute, so this can be problematic in some circumstances. In case you are offering a locked down surroundings for customers to create batch job insurance policies then you definitely would possibly be capable to meet these standards.
Limiting which roles customers can assume
One of many mitigations AWS recommends for STS assume-role issues is to restrict which roles a person can assume with circumstances within the IAM Consumer coverage. Their instance demonstrates a coverage for an incident supervisor who can solely assume an incident-manager function:

You may use this strategy to restrict these answerable for deployments who additionally wouldn’t have entry to alter this coverage above from assuming batch job roles. They could have permissions to imagine solely a deployment function to execute CloudFormation to deploy a batch job, however not assume the roles the batch job deployment scripts create.
Limiting the ARNs that may be handed into our batch job template
What about additional limiting the ARNs that may be handed into our batch job? We will replace our function additional to restrict what ARNs shall be utilized by our batch job roles as an alternative of permitting our template to take any ARN as a parameter. To me, that’s simply too dangerous, but it surely was a method to get began and suppose by way of how I may use a single template for batch job roles.
Primarily to this point I’ve decided I must have two various kinds of batch jobs to this point — batch jobs run by IAM directors, and the batch jobs run to course of information executed by a batch job administrator. If I can be certain that solely these two roles can be utilized to imagine batch jobs I’ll be higher off. If I can determine a manner to make sure solely the IAM administrator can assume IAM batch jobs and solely the batch job administrator can run different forms of jobs even higher.
Keep tuned for code modifications to deal with these issues in our function template.
Comply with for updates.
Teri Radichel
When you preferred this story please clap and comply with:
Medium: Teri Radichel or E-mail Checklist: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests providers through LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this collection:
____________________________________________
Creator:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, shows, and podcasts


