ACM.49 Safety and Utility Structure for operating batch jobs (A piece in progress…)
It is a place to trace the parts we create as we work via our cybersecurity metrics automation structure on this collection. These structure diagrams usually are not full and shall be up to date as I add new sources and parts. Comply with alongside by signing up for the e-mail checklist to get the quickest updates, or observe me on Twitter, LinkedIn or the GitHub repo on this put up. Additionally try this put up for a proof and the evolution of what we’re constructing:
This put up highlights what I already defined earlier than. Safety structure is just not a guidelines.
Though I’m creating a particular structure on this collection the ideas apply to cloud safety structure normally. The identical controls and strategy may very well be used for different sorts of purposes deployed within the cloud. Among the controls used on this structure are common — IAM, encryption, and networking.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Only a be aware that I’m nonetheless monitoring for plagiarism as defined right here:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
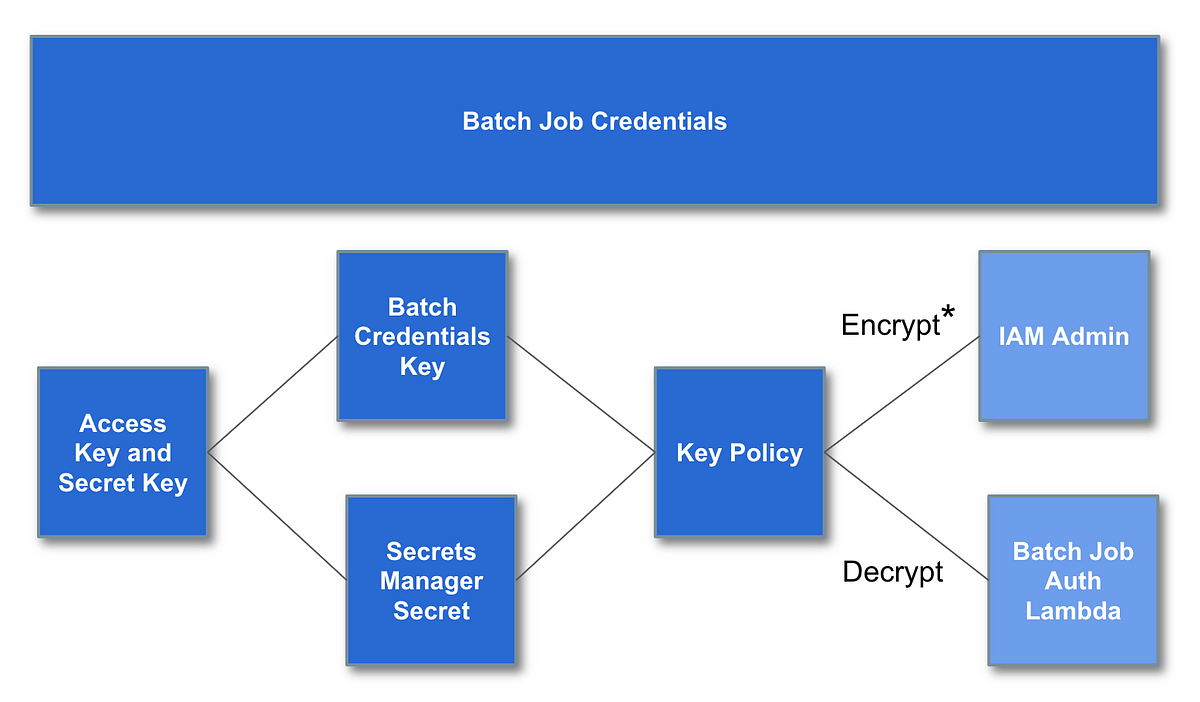
A generic batch job structure
Discover that I’m not calling this an AWS structure as a result of as I discussed earlier every of the three main cloud suppliers have a Batch service. I’ve additionally used batch jobs outdoors of cloud environments so you can use containers to realize an analogous structure on-premises — you’d simply need to do a number of further work to safe the containers and an orchestration surroundings like Kubernetes. Cloud suppliers handle a few of that behind the scenes when utilizing companies that supply batch jobs and features.
What are the parts of our safety and utility structure?
- IAM roles, customers, teams and insurance policies
- Useful resource Insurance policies
- A KMS key and a key coverage to encrypt batch job credentials
- A KMS Entry key and secret key with MFA related
- A Secret to retailer our credentials, encrypted with our encryption key
- Lambda features to deal with batch job triggers and authentication
- The precise Batch jobs and associated parts
- Information storage (similar to S3 buckets) and associated encryption keys
- Community safety controls
Take a look at script to construct all of the sources under
There’s a check script within the root of the GitHub repo that ought to create all of the parts under. I like to recommend operating the check script in a check account with no naming conflicts or restrictions.
You’ll have to observe the directions for including MFA to customers when required and configuring the proper AWS CLI profiles as defined within the collection. The check script within the GitHub repo pauses and refers you to the knowledge to set this up when required.
Id and Entry Administration
Id and Entry Administration (IAM) is the administration of customers allowed to entry the cloud and the permissions that outline the actions they’re allowed take within the cloud. Identities usually characterize a single individual and safety greatest observe ensures that every id has their very own credentials and may be independently recognized in logs. In different phrases, you don’t create a consumer title and password and provides these credentials to 6 individuals, as a result of then if it’s good to examine a safety incident you may’t inform which individual took the motion.
As defined within the collection we aren’t utilizing AWS SSO 4 our batch job credentials because it doesn’t at the moment assist what we’re going to do. Nonetheless, you can have an AWS SSO consumer who assigns their MFA gadget to a set of batch job automation credentials only for the aim of kicking off batch jobs.
IAM Customers
The very first thing to do in any cloud account is to login because the admin consumer and create different customers. The code within the GitHub repository has separate scripts for creating the preliminary IAM consumer. After that, instructions may be executed utilizing the permissions assigned to the IAM consumer.
Subsequent the IAM consumer can create customers within the account. In our case, we’re creating customers immediately within the account. Some organizations could have customers that exist in a separate listing and customers authenticate to a third-party id supplier (IdP) however to maintain it easy right here we’re creating customers within the cloud listing. IdPs and federation are outdoors the scope of this instance.
IAM Teams and Insurance policies
Finest observe is to create and apply insurance policies to teams, not particular person customers so we crated some teams for that can have separate permissions. A brand new group are created when it’s good to apply a unique set of permissions to a bunch of individuals. You additionally may create completely different teams if it’s good to give completely different individuals permission to handle the group.

After creating the teams we did two issues:
- Add a coverage to every group that permits the group to assign a bunch position. Teams are additionally allowed to assign different roles similar to batch job roles.
- Add customers to the teams.
IAM Roles and Insurance policies
Subsequent we created IAM roles. IAM roles outline a set of permissions. Customers and companies on AWS can assume roles after which take actions allowed in that permission set.

Why do we want teams and roles? First, AWS companies can solely assume roles. They will’t be part of teams. We simply checked out how we may permit a Lambda perform to imagine a job. We’re additionally going to make use of roles from inside our Batch jobs in a means that we can not with the insurance policies assigned to a bunch.
Encryption keys, key insurance policies, automation credentials, and secrets and techniques
Encryption keys must be created earlier than issues that must be encrypted are created. On AWS, an encryption key coverage can restrict who can take what actions may be taken with that encryption key (encrypt or decrypt).
We are able to created a KMS key coverage to guard batch job credential which we’ll use as a result of we need to require MFA to start out a batch job. We create the credentials and a coverage that specifies which AMI identities can encrypt and decrypt the credentials. We then created the credentials with the IAM Admin position and saved it in Secrets and techniques Supervisor (a secrets and techniques vault). Then we examined decrypting secrets and techniques in secrets and techniques supervisor utilizing a Lambda position that’s approved to decrypt the credentials. We created a Lambda perform to set off our batch job and examined our position to entry the batch job credentials.

Encrypt has an asterisk* subsequent to it as a result of as defined as a result of order to encrypt the credentials a principal wants encrypt, not decrypt permissions. Meaning you can’t segregate your encrypt and decrypt permissions cleanly in an AWS coverage. Nonetheless, we restricted the flexibility to place secrets and techniques into Secrets and techniques supervisor to the IAM position and the permission to retrieve them to the Lambda position. That implies that despite the fact that the IAM Admins have decrypt permissions, they will’t retrieve the key to decrypt it.
I perceive how AWS justifies this implementation. Nonetheless, this looks like a flaw within the design of KMS insurance policies as a result of the client is just not attempting to outline a coverage to encrypt or decrypt the info key. The shopper is attempting to outline a coverage round who can encrypt or decrypt their very own information that the encryption key protects. Performance associated to envelope encryption ought to a part of the behind-the-scenes implementation. It is going to be troublesome to repair now resulting from backward compatibility however AWS may provide two variations like they did with EC2 basic and attempt to get individuals to maneuver over to the corrected implementation over time.
The code to create batch admin credentials, secrets and techniques, and keys above was refactored to permit creation of a number of units of credentials since you might need a number of individuals managing several types of batch jobs.
Zero Belief Insurance policies
Several types of insurance policies exist on AWS — IAM Insurance policies, Belief Insurance policies, and Useful resource Insurance policies. The posts into this collection dive into a few of the particulars of what these several types of insurance policies are and how one can create them. The collection covers subjects similar to proscribing entry to sure CloudFormation stacks and batch jobs, limiting who can entry particular sources similar to KMS keys and and what sources a principal can entry (two sides to the equation). Within the final part we checked out how insurance policies will help with segregation of duties. As well as we lined the confused deputy assault and the way that applies to belief insurance policies.
Generally, each coverage we construct shall be as near a zero belief coverage as potential as defined on this put up. That’s simpler to do on a cloud platform than in an on-premises surroundings and too few individuals make the most of this functionality. I’m attempting to indicate you on this collection that it may be achieved, and the place the platforms may enhance to make it simpler.
I defined why you may want a separate IAM workforce resulting from all this complexity. Separate the individuals who give the permissions (create the insurance policies) from those that use the permissions.
Batch Job Set off
To set off our batch job we want a mechanism to get the MFA required to imagine a job. The next outlines the steps within the course of.

We’ll be engaged on the above parts subsequent. This web page shall be up to date as further items of the structure get carried out. Comply with for updates.
Teri Radichel
For those who favored this story please clap and observe:
Medium: Teri Radichel or Electronic mail Listing: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests companies by way of LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this collection:
____________________________________________
Creator:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, shows, and podcasts