Whereas making ready the Web Routing Safety webinar, I stumbled upon RFC 7908, containing a wonderful taxonomy of BGP route leaks. I by no means checked whether or not it covers each potential state of affairs, however I discovered it a useful useful resource when organizing my ideas.
Let’s stroll by way of the assorted leak sorts the authors recognized utilizing the next pattern topology:
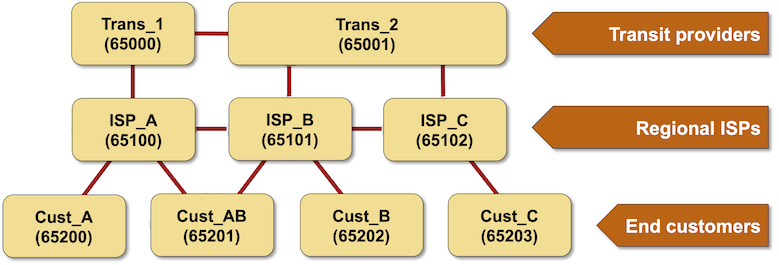
Hairpin flip: a buyer lacks output filters and propagates routes between two service suppliers (instance: Cust-AB propagates ISP-A routes to ISP-B). Relying on the upstream connectivity of the ISPs, the trail by way of the client AS would possibly consequence within the shortest AS path. Even worse, many service suppliers choose buyer routes over peer routes no matter AS path size
Lateral leak: a service supplier is leaking peer routes (instance: ISP-B forwards ISP-A prefixes to ISP-C), and its friends often settle for them as greatest routes:
- AS path on a lateral leak is shorter than the paths going by way of the transit suppliers
- No one of their proper thoughts would favor transit routes (the place they’re paying for site visitors or bandwidth) over settlement-free peer routes.
Everybody concerned in a lateral leak must be grateful {that a} sort soul supplies free transit connectivity. Sadly, that sort soul often forgets to provision its peer hyperlinks accordingly, leading to congestion and buyer complaints.
Peer-transit leaks: a service supplier is leaking peer routes to its upstream transit supplier (or vice versa). In our topology, ISP-B would leak routes between ISP-A and Trans-2. The transit supplier would usually choose leaked routes (coming from its buyer), and the peer ISP would most likely select them because of the shorter AS path size.
As earlier than, karma punishes the type soul offering free transit with further site visitors costs, and everybody will get yelled at as a consequence of inevitable hyperlink congestion. Not precisely a enjoyable day within the workplace.
Lack of routing insurance policies (= filters) on EBGP classes often trigger the abovementioned leaks. Now for some heavy hitters:
Prefix re-origination: an autonomous system advertises third-party prefixes as belonging to itself:
Lastly, there’s the unintended leak of internal- or more-specific prefixes, often ensuing from a lacking route map in an IGP-to-BGP redistribution level. We’re most likely coping with this kind of leak when somebody pronounces an extra 20.000 routes and revokes them a couple of minutes later. Bonus factors for type if these routes carry the dimension of the worldwide BGP desk over a {hardware} restrict of core Web routers.
Within the subsequent weblog posts on this collection we’ll focus on particular person leak sorts and instruments you should utilize to keep away from them. Within the meantime, learn RFC 7908 and watch the Web Routing Safety webinar.

