Cisco on Wednesday rolled out patches to deal with eight safety vulnerabilities, three of which might be weaponized by an unauthenticated attacker to achieve distant code execution (RCE) or trigger a denial-of-service (DoS) situation on affected gadgets.
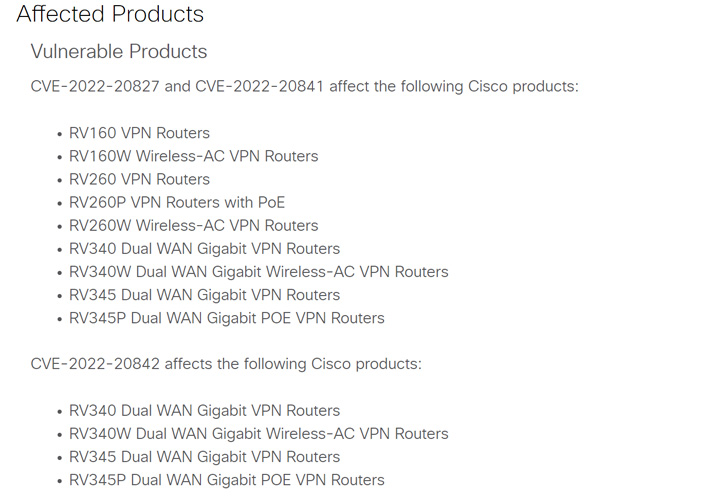
Probably the most important of the issues influence Cisco Small Enterprise RV160, RV260, RV340, and RV345 Collection routers. Tracked as CVE-2022-20842 (CVSS rating: 9.8), the weak spot stems from an inadequate validation of user-supplied enter to the web-based administration interface of the home equipment.
“An attacker may exploit this vulnerability by sending crafted HTTP enter to an affected system,” Cisco stated in an advisory. “A profitable exploit may enable the attacker to execute arbitrary code as the basis consumer on the underlying working system or trigger the system to reload, leading to a DoS situation.”
A second shortcoming pertains to a command injection vulnerability residing within the routers’ internet filter database replace function (CVE-2022-20827, CVSS rating: 9.0), which might be exploited by an adversary to inject and execute arbitrary instructions on the underlying working system with root privileges.
The third router-related flaw to be resolved (CVE-2022-20841, CVSS rating: 8.0) can also be a command injection bug within the Open Plug-n-Play (PnP) module that might be abused by sending a malicious enter to realize code execution on the focused Linux host.
“To use this vulnerability, an attacker should leverage a man-in-the-middle place or have a longtime foothold on a particular community system that’s related to the affected router,” the networking gear maker famous.
Additionally patched by Cisco are 5 medium safety flaws affecting Webex Conferences, Id Companies Engine, Unified Communications Supervisor, and BroadWorks Utility Supply Platform.
The corporate provided no workarounds to remediate the problems, including there isn’t a proof of those vulnerabilities being exploited within the wild. That stated, prospects are really useful to maneuver shortly to use the updates.