The China-linked nation-state hacking group known as Mustang Panda is utilizing lures associated to the continuing Russo-Ukrainian Struggle to assault entities in Europe and the Asia Pacific.
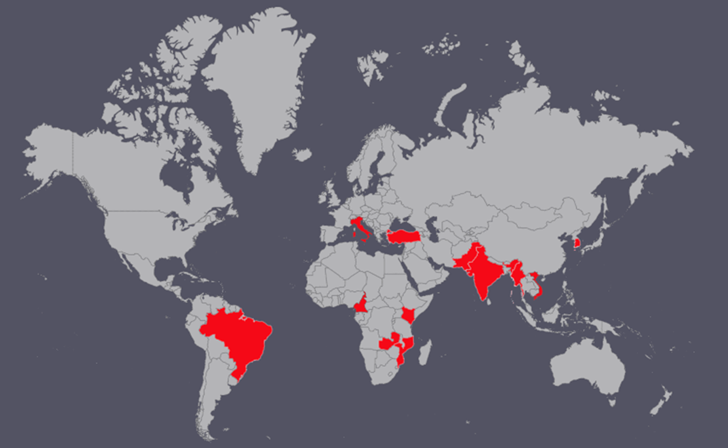
That is in line with the BlackBerry Analysis and Intelligence Workforce, which analyzed a RAR archive file titled “Political Steerage for the brand new EU strategy in the direction of Russia.rar.” A few of the focused international locations embody Vietnam, India, Pakistan, Kenya, Turkey, Italy, and Brazil.
Mustang Panda is a prolific cyber-espionage group from China that is additionally tracked below the names Bronze President, Earth Preta, HoneyMyte, RedDelta, and Crimson Lich.
It is believed to be energetic since at the least July 2018, per Secureworks’ menace profile, though indications are that the menace actor has been focusing on entities worldwide as early as 2012.
Mustang Panda is understood to closely depend on sending weaponized attachments by way of phishing emails to attain preliminary an infection, with the intrusions finally resulting in the deployment of the PlugX distant entry trojan.
Nonetheless, current spear-phishing assaults undertaken by the group focusing on authorities, training, and analysis sectors within the Asia Pacific area have concerned customized malware like PUBLOAD, TONEINS, and TONESHELL, suggesting an growth to its malware arsenal.
The most recent findings from BlackBerry present that the core an infection course of has remained roughly the identical, whilst Mustang Panda continues to make the most of geopolitical occasions to their benefit, echoing prior stories from Google and Proofpoint.
Contained inside the decoy archive is a shortcut to a Microsoft Phrase file, which leverages DLL side-loading – a way that was additionally employed in assaults geared toward Myanmar earlier this 12 months – to kick off the execution of PlugX in reminiscence, earlier than displaying the doc’s contents.
“Their assault chain stays in line with the continued use of archive information, shortcut information, malicious loaders, and using the PlugX malware, though their supply setup is often personalized per area/nation to lure victims into executing their payloads within the hope of creating persistence with the intent of espionage,” BlackBerry’s Dmitry Bestuzhev instructed The Hacker Information.