A months-long cyber espionage marketing campaign undertaken by a Chinese language nation-state group focused a number of entities with reconnaissance malware in order to glean details about its victims and meet its strategic objectives.
“The targets of this latest marketing campaign spanned Australia, Malaysia, and Europe, in addition to entities that function within the South China Sea,” enterprise safety agency Proofpoint stated in a printed in partnership with PwC.
Targets embody native and federal Australian Governmental businesses, Australian information media corporations, and international heavy business producers which conduct upkeep of fleets of wind generators within the South China Sea.
Proofpoint and PwC attributed the intrusions with average confidence to a risk actor tracked by the 2 corporations below the names TA423 and Purple Ladon respectively, which is also called APT40 and Leviathan.
APT40 is the identify designated to a China-based, espionage-motivated risk actor that is recognized to be lively since 2013 and has a sample of putting entities within the Asia-Pacific area, with a major concentrate on the South China Sea. In July 2021, the U.S. authorities and its allies tied the adversarial collective to China’s Ministry of State Safety (MSS).
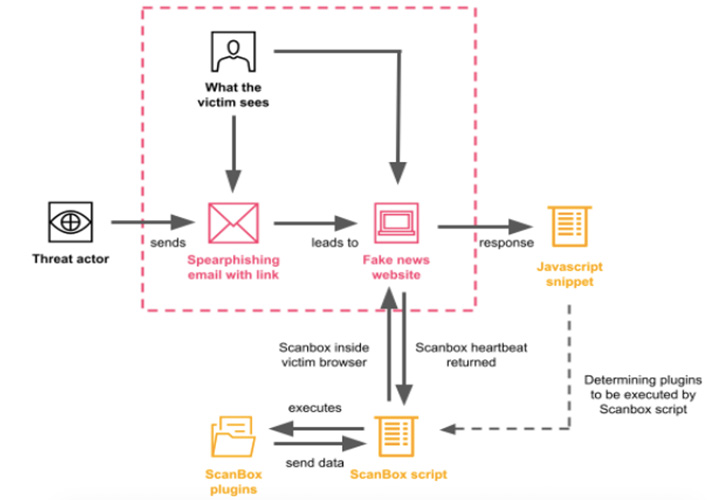
Assaults took the type of a number of phishing marketing campaign waves between April 12 and June 15 that employed URLs masquerading as Australian media companies to ship the ScanBox reconnaissance framework. The phishing emails got here with topic strains comparable to “Sick Go away,” “Person Analysis,” and “Request Cooperation.”
Not like watering holes or strategic internet compromises whereby a respectable web site recognized to be visited by the targets are contaminated with malicious JavaScript code, the APT40 exercise leverages an actor-controlled area that is used to ship the malware.
“The risk actor would continuously pose as an worker of the fictional media publication ‘Australian Morning Information,’ offering a URL to the malicious area and soliciting targets to view its web site or share analysis content material that the web site would publish,” the researchers stated.
ScanBox, utilized in assaults as early as 2014, is a JavaScript-based malware that allows risk actors to profile their victims in addition to ship next-stage payloads to targets of curiosity. It is also recognized to be privately shared amongst a number of China-based hacking teams, similar to HUI Loader, PlugX, and ShadowPad.
A number of the notable risk actors which were beforehand noticed utilizing ScanBox embrace APT10 (aka Purple Apollo or Stone Panda), APT27 (aka Emissary Panda, Fortunate Mouse, or Purple Phoenix) and TA413 (aka Fortunate Cat).
Additionally retrieved and executed by the malware within the sufferer’s internet browser are a variety of plugins that enable it to log keystrokes, fingerprint the browser, collect a listing of browser add-ons put in, talk with the contaminated machines, and examine for the presence of Kaspersky Web Safety (KIS) software program.
This isn’t the primary time APT40 has adopted the modus operandi of using faux information web sites to deploy ScanBox. A 2018 phishing marketing campaign uncovered by Mandiant used information article URLs hosted on a rogue area as lures to trick recipients into downloading the malware.
Curiously, the April-June assaults are a part of a sustained phishing exercise linked to the identical risk actor focusing on organizations primarily based in Malaysia and Australia in addition to international corporations probably associated to offshore vitality tasks within the South China Sea from March 2021 to March 2022.
These assaults made use of malicious RTF paperwork to ship a first-stage downloader that then acted as a conduit to retrieve encoded variations of the Meterpreter shellcode. One of many victims of this marketing campaign in March 2022 was a European producer of heavy gear that is utilized in offshore wind farms within the Strait of Taiwan.
That is not all. APT40 has additionally been attributed as behind the Copy-Paste Compromises the Australian Cyber Safety Centre (ACSC) disclosed in June 2020 that had been directed towards authorities businesses.
“This risk actor has demonstrated a constant concentrate on entities concerned with vitality exploration within the South China Sea, in tandem with home Australian targets together with protection and healthcare,” the researchers stated.