A malicious marketing campaign concentrating on the Center East is probably going linked to BackdoorDiplomacy, a complicated persistent menace (APT) group with ties to China.
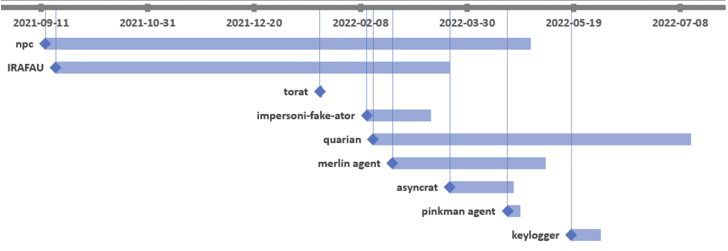
The espionage exercise, directed towards a telecom firm within the area, is alleged to have commenced on August 19, 2021 by the profitable exploitation of ProxyShell flaws within the Microsoft Alternate Server.
Preliminary compromise leveraged binaries susceptible to side-loading methods, adopted through the use of a mixture of reputable and bespoke instruments to conduct reconnaissance, harvest information, transfer laterally throughout the atmosphere, and evade detection.
“File attributes of the malicious instruments confirmed that the primary instruments deployed by the menace actors have been the NPS proxy software and IRAFAU backdoor,” Bitdefender researchers Victor Vrabie and Adrian Schipor stated in a report shared with The Hacker Information.
“Beginning in February 2022, the menace actors used one other software – [the] Quarian backdoor, together with many different scanners and proxy/tunneling instruments.”
BackdoorDiplomacy was first documented by ESET in June 2021, with the intrusions primarily aimed toward diplomatic entities and telecommunication firms in Africa and the Center East to deploy Quarian (aka Turian or Whitebird).
The espionage motives of the assault is evidenced by means of keylogger and PowerShell scripts designed to assemble electronic mail content material. IRAFAU, which is the primary malware element delivered after acquiring a foothold, is used to carry out data discovery and lateral motion.
That is facilitated by downloading and importing recordsdata from and to a command-and-control (C2) server, launching a distant shell, and executing arbitrary recordsdata.
The second backdoor used within the operation is an up to date model of Quarian, which comes with a broader set of capabilities to regulate the compromised host.
Additionally put to make use of is a software dubbed Impersoni-fake-ator that is embedded into reputable utilities like DebugView and Putty and is engineered to seize system metadata and execute a decrypted payload acquired from the C2 server.
The intrusion is additional characterised by means of open supply software program comparable to ToRat, a Golang distant administration software, and AsyncRAT, the latter of which is probably going dropped by way of Quarian.
Bitdefender’s attribution of the assault to BackdoorDiplomacy comes from overlaps within the C2 infrastructure recognized as utilized by the group in prior campaigns.