Over a dozen military-industrial advanced enterprises and public establishments in Afghanistan and Europe have come beneath a wave of focused assaults since January 2022 to steal confidential knowledge by concurrently making use of six totally different backdoors.
Russian cybersecurity agency Kaspersky attributed the assaults “with a excessive diploma of confidence” to a China-linked menace actor tracked by Proofpoint as TA428, citing overlaps in ways, strategies, and procedures (TTPs).
TA428, additionally tracked beneath the names Bronze Dudley, Temp.Hex, and Vicious Panda, has a historical past of hanging entities in Ukraine, Russia, Belarus, and Mongolia. It is believed to share connections with one other hacking group referred to as Mustang Panda (aka Bronze President).
Targets of the newest cyber espionage marketing campaign included industrial crops, design bureaus and analysis institutes, authorities companies, ministries and departments in a number of East European nations and Afghanistan.
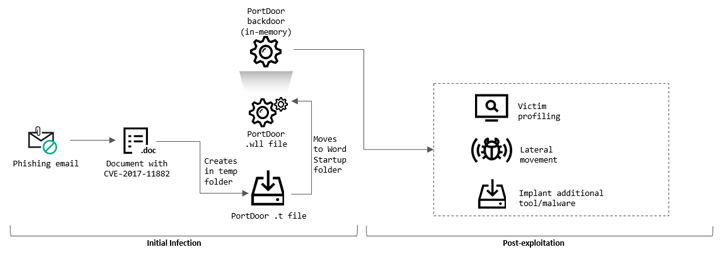
Assault chains entail penetrating the enterprise IT networks utilizing fastidiously crafted phishing emails, together with some that referenced private data pertaining to the organizations, to trick recipients into opening rogue Microsoft Phrase paperwork.
These decoy recordsdata include exploits for a 2017 reminiscence corruption flaw within the Equation Editor element (CVE-2017-11882) that would result in the execution of arbitrary code within the affected techniques, finally resulting in the deployment of a backdoor referred to as PortDoor.
PortDoor was notably employed in spear-phishing assaults mounted by Chinese language state-sponsored hackers in April 2021 to hack into the techniques of a protection contractor that designs submarines for the Russian Navy.
The usage of six totally different implants is probably going an try on the a part of the menace actors to determine redundant channels for controlling contaminated hosts ought to one in all them get detected and faraway from the networks.
The intrusions culminate with the attacker hijacking the area controller and gaining full management of all the group’s workstations and servers, leveraging the privileged entry to exfiltrate recordsdata of curiosity within the type of compressed ZIP archives to a distant server situated in China.
Different backdoors utilized within the assaults embrace nccTrojan, Cotx, DNSep, Logtu, and a beforehand undocumented malware dubbed as CotSam, so named owing to its similarities with Cotx. Every offers intensive performance for commandeering the techniques and harvesting delicate knowledge.
Additionally included within the assaults is Ladon, a hacking framework for the lateral motion that additionally allows the adversary to scan for units within the community in addition to exploit safety vulnerabilities in them to execute malicious code.
“Spear phishing stays some of the related threats to industrial enterprises and public establishments,” Kaspersky stated. “The attackers used primarily identified backdoor malware, in addition to normal strategies for lateral motion and antivirus answer evasion.”
“On the similar time, they had been in a position to penetrate dozens of enterprises and even take management of your entire IT infrastructure, and IT safety options of among the organizations attacked.”
The findings arrive a bit of over two months after the Twisted Panda actors had been noticed concentrating on analysis institutes in Russia and Belarus to drop a bare-bones backdoor referred to as Spinner.