A risk cluster with ties to a hacking group known as Tropic Trooper has been noticed utilizing a beforehand undocumented malware coded in Nim language to strike targets as a part of a newly found marketing campaign.
The novel loader, dubbed Nimbda, is “bundled with a Chinese language language greyware ‘SMS Bomber’ device that’s almost certainly illegally distributed within the Chinese language-speaking internet,” Israeli cybersecurity firm Test Level mentioned in a report.
“Whoever crafted the Nim loader took particular care to offer it the identical executable icon because the SMS Bomber that it drops and executes,” the researchers mentioned. “Subsequently your complete bundle works as a trojanized binary.”
SMS Bomber, because the title signifies, permits a consumer to enter a telephone quantity (not their very own) in order to flood the sufferer’s system with messages and doubtlessly render it unusable in what’s a denial-of-service (DoS) assault.
The truth that the binary doubles up as SMS Bomber and a backdoor means that the assaults should not simply aimed toward those that are customers of the device — a “fairly unorthodox goal” — but in addition extremely focused in nature.
Tropic Trooper, additionally identified by the monikers Earth Centaur, KeyBoy, and Pirate Panda, has a observe document of hanging targets positioned in Taiwan, Hong Kong, and the Philippines, primarily specializing in authorities, healthcare, transportation, and high-tech industries.
Calling the Chinese language-speaking collective “notably refined and well-equipped,” Pattern Micro final 12 months identified the group’s skill to evolve their TTPs to remain below the radar and depend on a broad vary of customized instruments to compromise its targets.
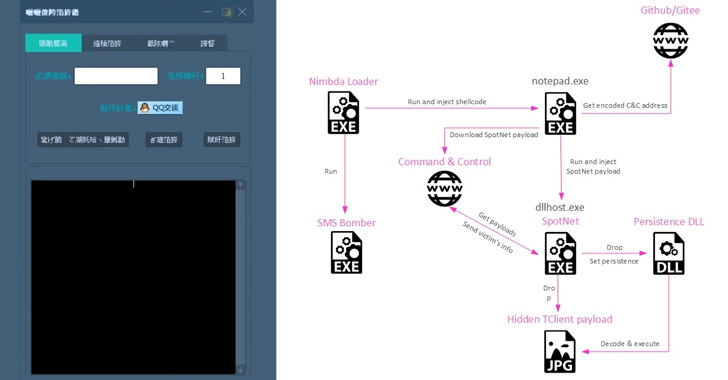
The most recent assault chain documented by Test Level begins with the tampered SMS Bomber device, the Nimbda loader, which launches an embedded executable, on this case the reliable SMS bomber payload, whereas additionally additionally injecting a separate piece of shellcode right into a notepad.exe course of.
This kicks off a three-tier an infection course of that entails downloading a next-stage binary from an obfuscated IP deal with laid out in a markdown file (“EULA.md”) that is hosted in an attacker-controlled GitHub or Gitee repository.
The retrieved binary is an upgraded model of a trojan named Yahoyah that is designed to gather details about native wi-fi networks within the sufferer machine’s neighborhood in addition to different system metadata and exfiltrate the main points again to a command-and-control (C2) server.
Yahoyah, for its half, additionally acts as a conduit to fetch the final-stage malware, which is downloaded within the type of a picture from the C2 server. The steganographically-encoded payload is a backdoor generally known as TClient and has been deployed by the group in earlier campaigns.
“The noticed exercise cluster paints an image of a targeted, decided actor with a transparent objective in thoughts,” the researchers concluded.
“Normally, when third-party benign (or benign-appearing) instruments are hand-picked to be inserted into an an infection chain, they’re chosen to be the least conspicuous doable; the selection of an ‘SMS Bomber’ device for this function is unsettling, and tells a complete story the second one dares to extrapolate a motive and an supposed sufferer.”